For those with a tenured cybersecurity career, you’re well aware that August marked the 25th anniversary of Black Hat USA. The first in-person Black Hat conference in three years revealed some interesting sessions and speakers, and some of the same cautions and warnings.
Looking back on videos about cybersecurity from 1997, while technology has evolved, in some ways, InfoSec concerns haven’t changed. Case in point –
- 1997: here’s the info that can be found about you on the internet
- 2022: here’s how we protect massive data files in the cloud
- 1997: here’s why financial transactions on the internet are safe
- 2022: here’s a solution to prioritize vulnerabilities
After 3 years, there were great sessions, speakers, and topics. Here’s a few that stood out:
- Cyber Safety Review Board
Think of it like the cybersecurity equivalent of the National Transportation Safety Board (NTSB). With a formalized investigation process and public disclosure of results, a Cyber Safety Review Board can root out all causes of hacks to help protect the industry as a whole.
- APIs, machine identities, and IAM policies
Veza isn’t the only one talking about non-human identities and complex IAM policies. Two sessions at Black Hat explained why non-human identities are vulnerable (companies typically have a 45:1 ratio of non-human identities to protect compared to human identities).
- Supply Chain Attacks
No surprise here, given the high profile of the SolarWinds attack. Businesses rely on third party software for business operations. The more popular a technology, the more appealing it is for bad actors.
From our survey at the booth, we noticed a larger theme: security considerations resulting from the move to a multi-cloud environment. The past few years have seen an acceleration of companies moving to a multi-cloud environment. Multi-cloud gives companies the best solution for a specific needs, while also getting:
- Flexibility
- Performance
- protection against failure
- Vendor independence, and
- Pricing
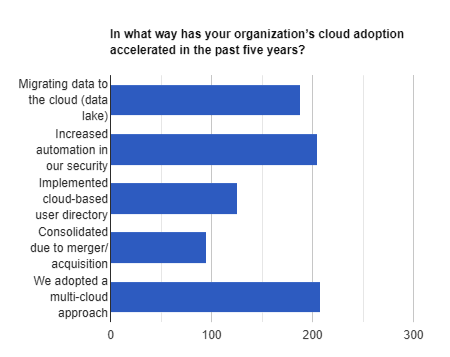
What companies lose are transparency and security. Each organization needs to make their own decision based on their specific environment, but it’s safe to say that, for now, the benefits outweigh the challenges. Here’s the answers to our survey question, “In what way has your organization’s cloud adoption accelerated in the past five years?”
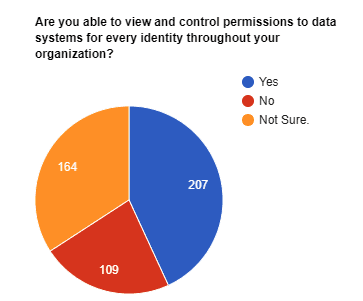
And when asked, “Are you able to view and control permissions to data systems for every identity throughout your organization?”, Black Hat attendees had a high level of confidence.
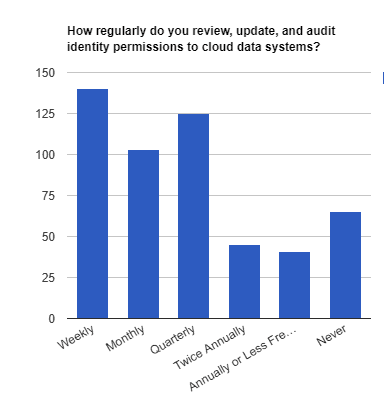
Here’s something many didn’t consider: as cloud adoption increased, so did the varieties of identities to manage. While companies have been moving to the cloud, now the multi-cloud environment means identities for employees, partners, vendors, and a boatload of non-human identities, like service accounts and bots, and even APIs. Without a strong identity foundation, maintaining access control for a rapidly growing number of identities is impossible.
And how often are organizations auditing identity permissions? Surprisingly, the Black Hat audience has a high percentage auditing weekly (compare that to the Identiverse audience).
So – what does this tell us?
- Multi-cloud isn’t going anywhere.
- Companies need to find a solution to gain transparency and security across multi-cloud and hybrid cloud environments.
- Non-human / machine / service identities are exponentially increasing in number and risk.
To learn more about how Veza secured enterprise data in multi-cloud environments, see Core Authorization Platform.