Explore our posts
-
The Imperative for Identity Security: A Call to Action for the Industry
Learn more -
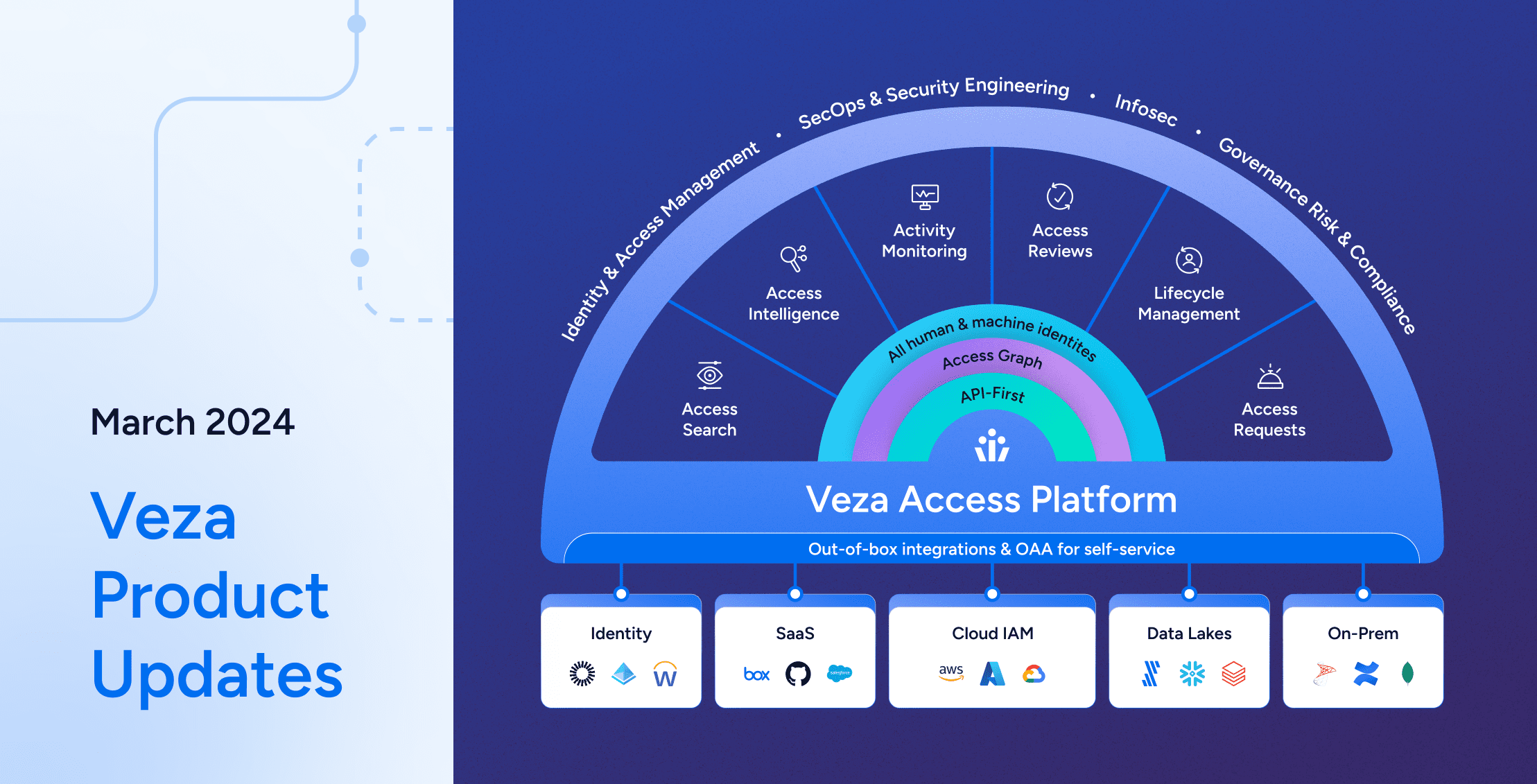
Veza Product Updates – March 2024
Learn more -
What is non-human identity management
Learn more -

Identity Security Posture Management
Learn more -
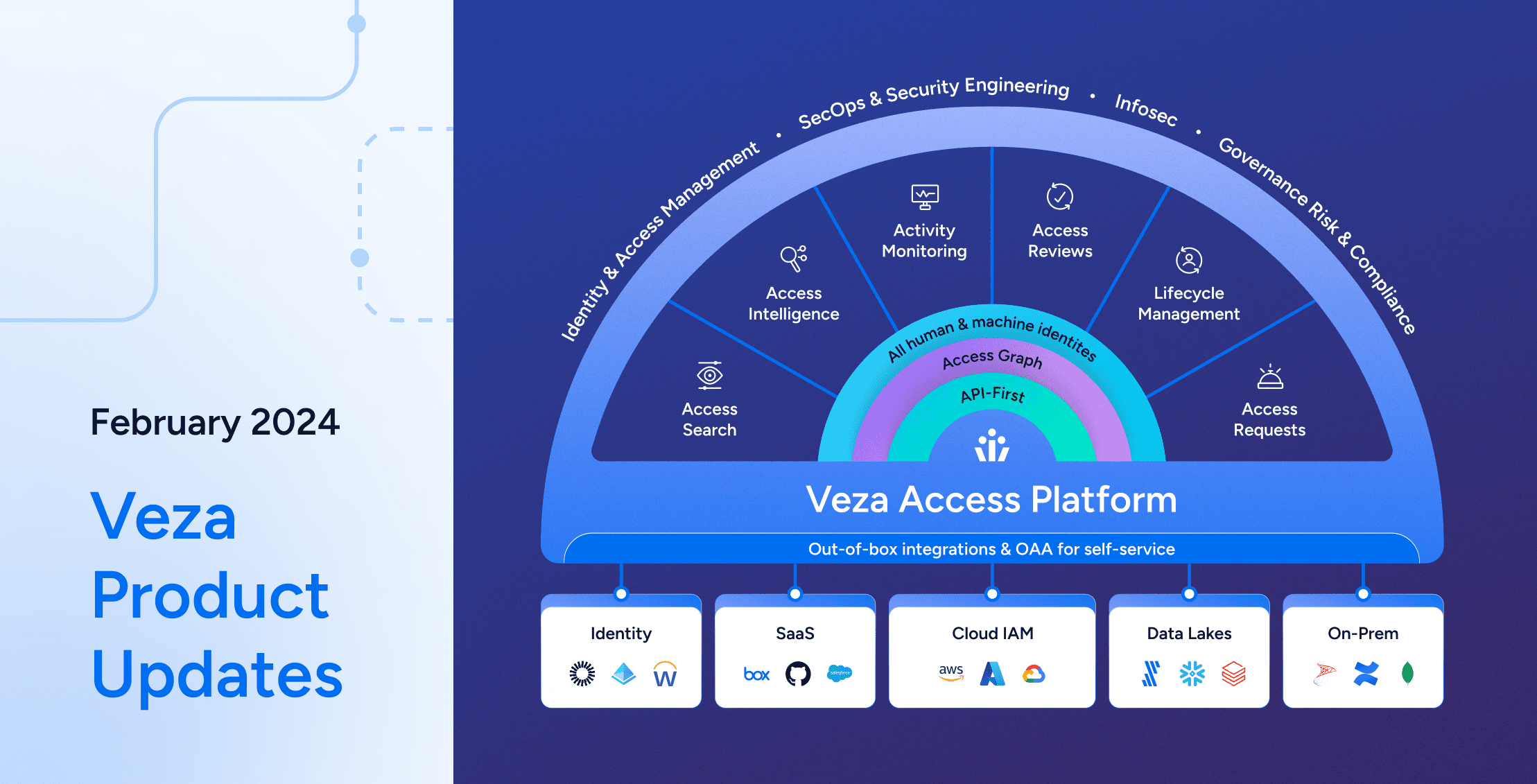
Veza Product Updates – February 2024
Learn more -

Veza for Crowdstrike: Identify, triage and remediate in minutes
Learn more
-

Identity Security Posture Management
Learn more -

Veza welcomes Mike Towers as Chief Security & Trust Officer
Learn more -

Identity Security Spotlight: Cisco announces “Identity Intelligence”
Learn more -

Veza @ Blackstone: Modernizing IGA with Automation and Intelligence
Learn more -
The year of Intelligent Access
Learn more -
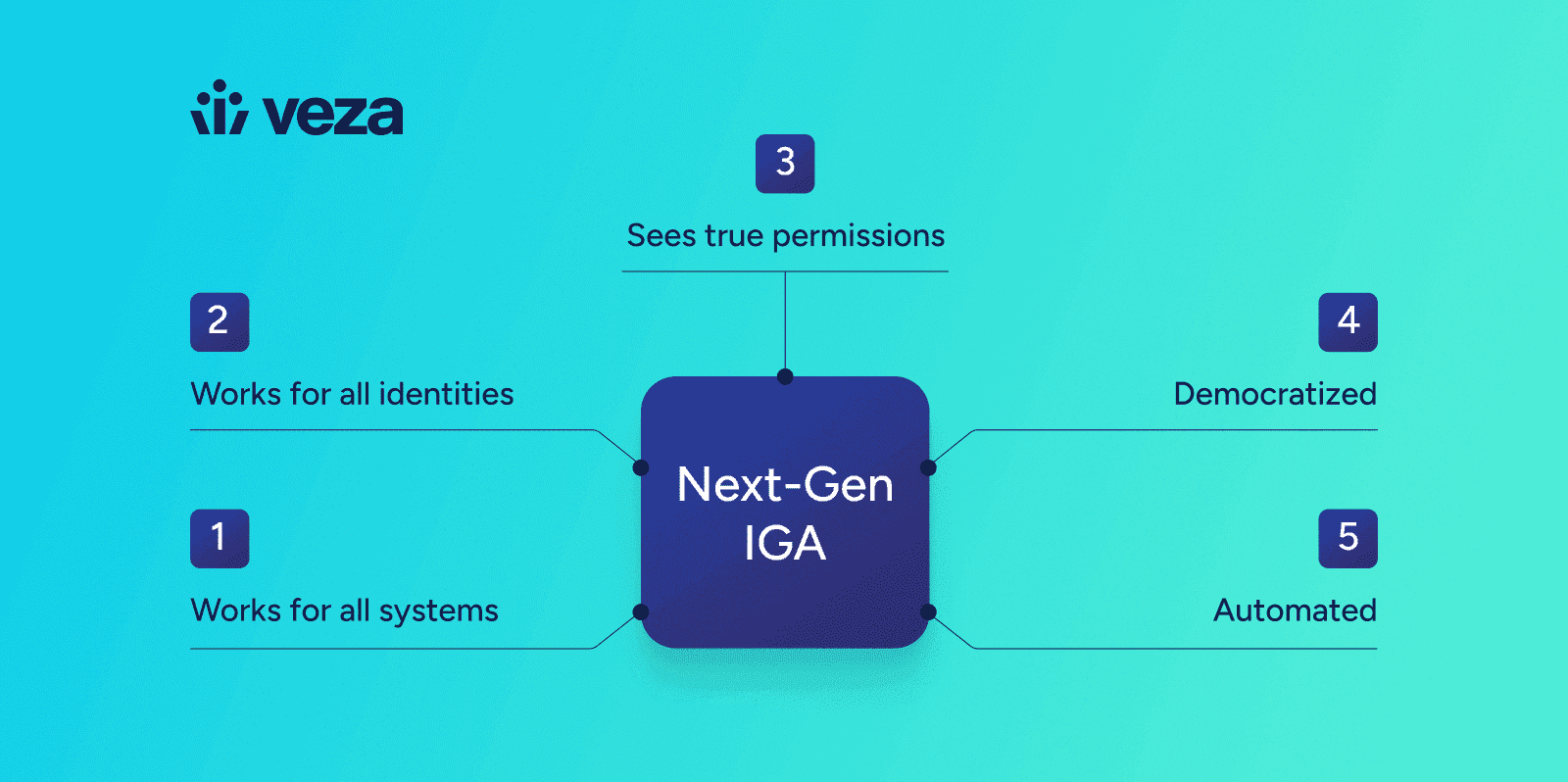
The Five Tenets of Next-Gen IGA
Learn more
-

Identity Security Posture Management
Learn more -

Decoding Data Sovereignty with Jenner Holden | Ep 3
Learn more -

Disrupting Breaches and Advancing InfoSec with David Tyburski | Ep 2
Learn more -

Identity Targeting: A Growing Threat with Rachel Wilson | Ep 1
Learn more -

Welcome to the Identity Radicals Podcast
Learn more
-

The Imperative for Identity Security: A Call to Action for the Industry
Learn more -

Veza Product Updates – March 2024
Learn more -

What is non-human identity management
Learn more -

Identity Security Posture Management
Learn more -

Veza Product Updates – February 2024
Learn more -

Veza for Crowdstrike: Identify, triage and remediate in minutes
Learn more