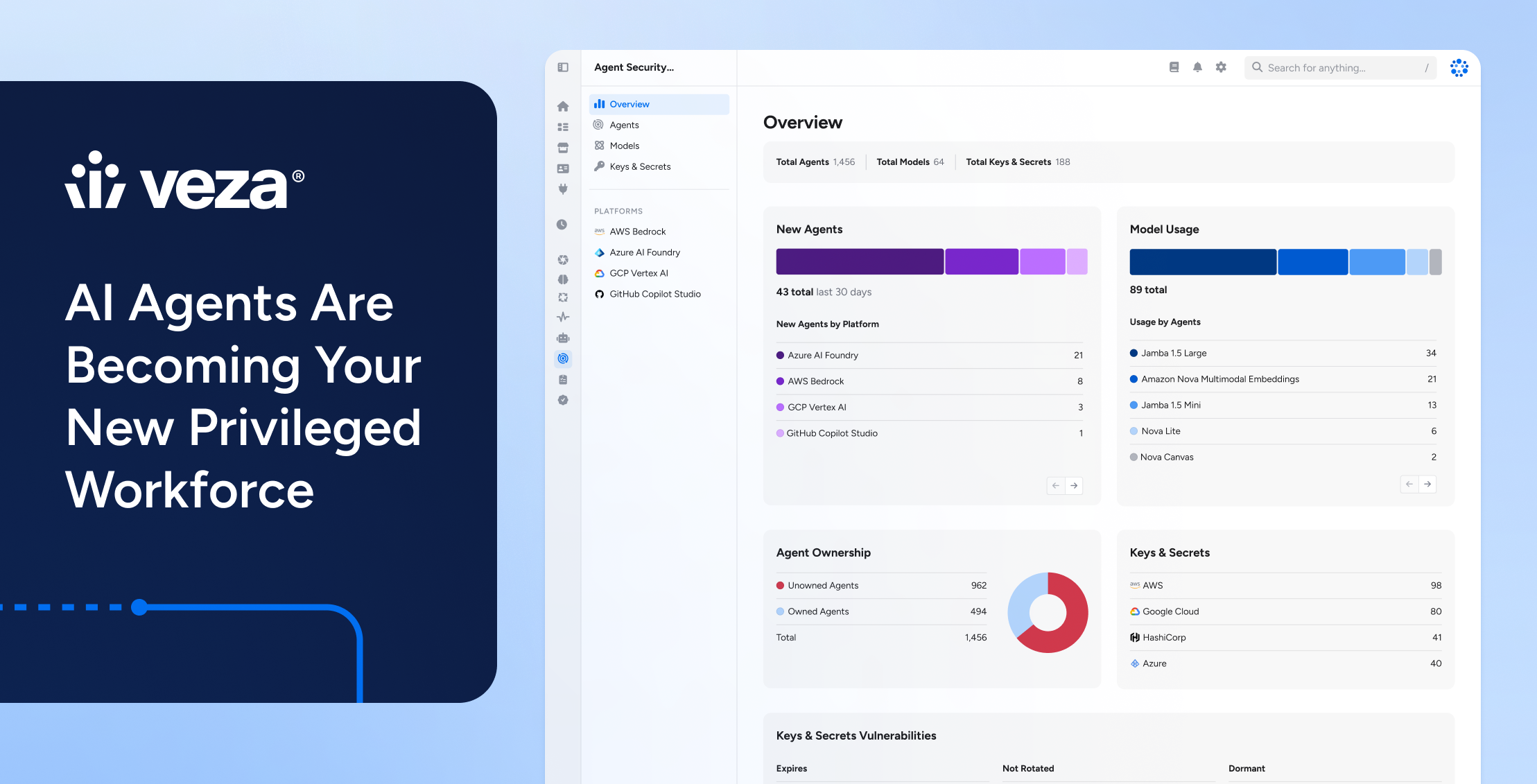
Service accounts are a type of non-human privileged account, typically used to automate various system tasks. Authenticated service accounts can be set to perform a wide range of routine actions, including:
· Executing a batch file of actions
· Running a network service
· Installing a new application
· Executing administrative functions on network appliances, servers, virtual machines
· Connecting two applications to perform specific functions
· Connecting an application to target data to perform specific actions
Automated tasks like these can be executed on-premises or in the cloud, and can be continuous, event triggered, or scheduled. Different platforms (e.g., Windows, Unix, Linux) and cloud environments (e.g., Azure, Google, Amazon, Oracle, IBM, etc.) typically require a separate, dedicated set of service accounts, each of which require privileged access to authenticate to various servers, applications, and databases so they can accomplish their tasks and microtasks.
Why Service Accounts Are Attractive Targets for Threat Actors
Service accounts can be charged with millions of tedious and repetitive tasks and save humans a lot of time and energy. But because they act as identities, service accounts require provisioning and lifecycle management, just like their human counterparts. And because they often enjoy privileged or even admin-level access, they’re a prime target for threat actors hoping to move laterally across your network.
To be effective, service accounts often must be known and verifiable not just to the application, but to everything that interacts with the application. The same broad access that makes the service account powerful makes it dangerous, and a significant number of well-known security breaches have been caused by compromised service accounts. But despite this threat, service accounts are seldom controlled as tightly as human identities. With more than 80% of all hacking breaches involving brute force or the use of lost or stolen credentials, why is service account management so often neglected?
It’s complicated.
Challenges in Securing Service Accounts
The broad access privileges of service accounts, combined with the security shortcuts account owners sometimes make to simplify management, make these nonhuman entities attractive attack targets. Service accounts need uninterrupted access to servers, applications, and databases to be effective. But because different platforms and cloud environments each require their own set of service accounts, it can create a nightmare for organizations trying to manage all their identities. Environment-based manual management processes are tedious and prone to errors, and an accurate inventory of service accounts with documented up to date ownership and entitlements is, at best, extremely rare. More typical is a poor understanding of what, exactly, each service account can access, who owns them, and whether they’re being actively managed at all.
It all adds up to a serious security risk that many organizations aren’t even aware of. Here are three particular challenges that make service account management difficult:
- Challenge #1: There’s no central source of truth for service account status.
The foundational challenge of effective lifecycle management of service accounts is the lack of an authoritative source for status. Human employee identities can be centrally managed with an HR application like Workday, which gives enterprise teams a single source of truth and up-to-date, authoritative status that enables automated authorization changes in response to change events, including the termination of privileges when they’re no longer needed. For humans, this challenge has been largely solved. Unfortunately, there’s no off-the-shelf solution for service account lifecycle management. Currently available IGA (Identity Governance and Administration) solutions need to be customized to support life cycle management and governance of service accounts by leveraging attestation processes that depend on associated owners. And that means accurately identifying the owners of these accounts, maintaining accurate owner data over time, and being able to enforce accountability so owners are properly incentivized to perform their service account management responsibilities. It’s expensive and complicated—most organizations struggle with these dependencies. - Challenge #2: Service accounts can’t authenticate themselves.
Security best practices for humans, like multi-factor authentication, unfortunately do nothing to help close the vulnerabilities of service accounts. These nonhuman entities can’t respond to a prompt to provide a time window restricted OTP (One Time Passcode) from an application, SMS message, or an email message, and they can’t provide biometric confirmation of identity. There are some emerging approaches, like cryptographic certificate-based authentication and just-in-time pulling of a password from an encrypted store via a Privileged Identity Management (PIM) or Privileged Access Management (PAM) tool. But unless the application provides out-of-the-box support for them—which is not common—these approaches typically require a significant investment to modify the application code to support them. - Challenge #3: Reuse of service accounts leads to over-privilege.
Many service accounts are routinely leveraged for multiple usages, even within a single application, and often with the same password. Some application owners, when pressed for time or concerned that a password rotation may risk application downtime if all the associated usages don’t successfully update in a timely manner, take the shortcut of utilizing an existing service account. This can bypass the delay of acquiring a new service account, and may simplify their lives in the moment—after all, they already know the password. But this risky, common practice can lead to a dangerous, shadowy expansion of service account privilege that’s not well understood even by the owners granting these accounts more and more power. Should an overprivileged service account identity be compromised, a laterally spreading attack becomes a lot more likely—and virtually impossible to understand, let alone contain.
Secure and Simplify Service Account Management with Veza
Veza helps organizations effectively manage their service accounts and reduce their vulnerability footprint by enabling customers to understand, manage and control the truest form of identity – authorization. We empower Security, IT and Data teams to better secure sensitive information by delivering a complete understanding over who can and should take what action on what data—whether those identities are human or not. Our platform uncovers existing service accounts and their permissions to apps, data, and cloud services, and provides a secure, easy to implement account request workflow. Organizations use Veza to introduce true lifecycle management for human and nonhuman entities, including scheduled password changes and automatic authorization updates when status change occurs.
Organizations with legacy solutions are quickly finding their data security tools are insufficient to secure service accounts within modern cloud data systems. They often lack the use of certificate-based authentication, can’t dynamically pull passwords from an encrypted store, and are limited in their ability to minimize downtime—a crucial consideration for today’s dynamic developer and workforce communities.. Veza seamlessly integrates with existing identity management platforms, cloud services, apps and data systems to help organizations manage data access governance, least privilege, entitlements, and more.