This is part two of our series on Snowflake security. Check out part one to learn how to manage and secure access to data in Snowflake at scale.
Enterprises that work with Snowflake are well aware of the challenges associated with keeping control over what happens as apps, services, data, people, and business requirements change. One significant issue known as “entitlement creep”—where users gradually accumulate unnecessary permissions—happens as a business evolves and roles within a company become fluid.
In this post, we’ll look at using Veza to avoid entitlement creep in Snowflake.
What is entitlement creep, and how does it happen?#
Entitlement creep happens when an identity—usually an employee or contractor— slowly accumulates privileges over time. These privileges may have been necessary when first granted, but as the employees’ duties evolve, new privileges are granted without removing old privileges no longer needed to perform the employee’s new duties. These over-permissive privileges can be difficult to detect because of the slow and gradual nature of the changes. Ultimately, entitlement creep leads to users having more permissions than necessary for their function.
As an illustration, let’s consider a user, Janet, who is part of a special project involving employee retention. Because of this involvement, Janet is given access to employee data in Snowflake.
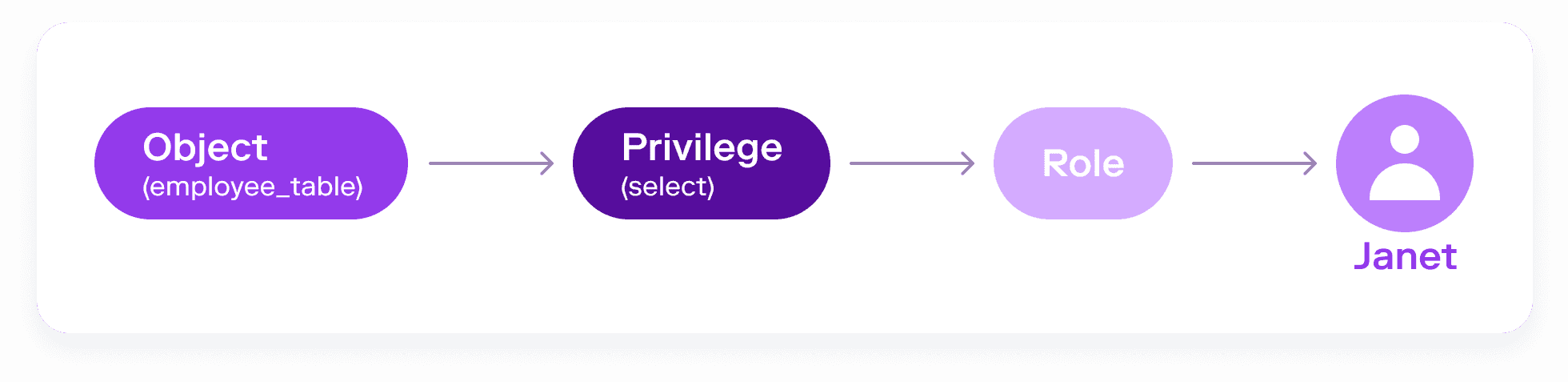
Several months later, a new time-sensitive project arises, this one dealing with headcount and employee costs. Janet is also granted access to salary information based on employee ID, without losing her previous privileges to the employee table. Now, the combination of her old and new privileges means that Janet is able to query any employee’s salary by name. This opens the possibility not just of intentional or accidental misuse by Janet, but also of sensitive employee information being breached if Janet’s identity is compromised by an attacker.
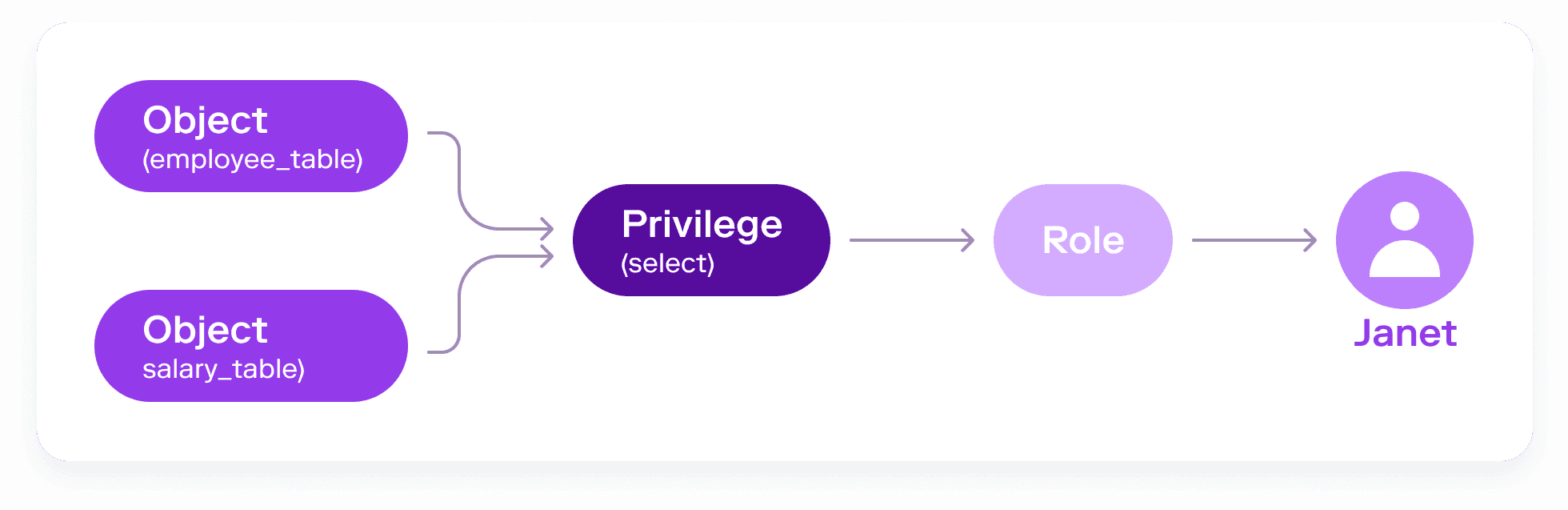
Consequences of entitlement creep#
Entitlement creep, if noticed at all, can often appear fairly harmless…right up until it doesn’t. Unintended combinations of local roles, hierarchical and nested roles, local users, and system-specific permissions in Snowflake can lead to serious data breaches and compliance issues. Consider the following examples:
Example 1: Temporarily granted permissions become permanent
A user is granted permissions for a special one-time project. However, once that project is completed, those permissions are not removed or updated.
Alice is a Snowflake administrator who is about to take an extended leave of absence. Alice works closely with Bob, whom she trusts, and grants elevated privileges to him. This way, Bob can respond to data access requests in Snowflake and cover Alice’s responsibilities while she’s away.
However, when Alice returns, they forget that this temporary elevation occurred. Bob, returns to his original role, but retains these powerful privileges in Snowflake. In consequence, Bob becomes a sort of “shadow admin” who can continue to grant Snowflake access to himself or others without oversight or review. Bob’s identity also becomes a gateway to a trove of sensitive data if compromised by an attacker.
Example 2: Organizational changes not matched by permissions changes
In this example, an employee has a change in job or reporting structure, but their access permissions are not updated to reflect those changes.
Charlie works in HR as a compensation consultant. In Snowflake, Charlie has access to highly-sensitive employee datasets. As Charlie progresses in his career, he shifts his role to training and development. With no systematic workflows in place, there is no way for the Snowflake administrator to know that this move occurred. Charlie retains his unneeded access to highly sensitive compensation data, and becomes a potential access pathway for an attacker.
Example 3: Accumulation of permissions-related tech debt
IT Help Desks are often overwhelmed with requests for access, especially for large Snowflake data sets. The communication between IT and the Snowflake administrator becomes strained over time, as both parties feel overworked and annoyed at the daily interruptions requesting the granting or removal of access.
To meet demand, a Snowflake administrator may decide to make a few generic and highly privileged Snowflake roles to be able to meet a wide range of access requests.
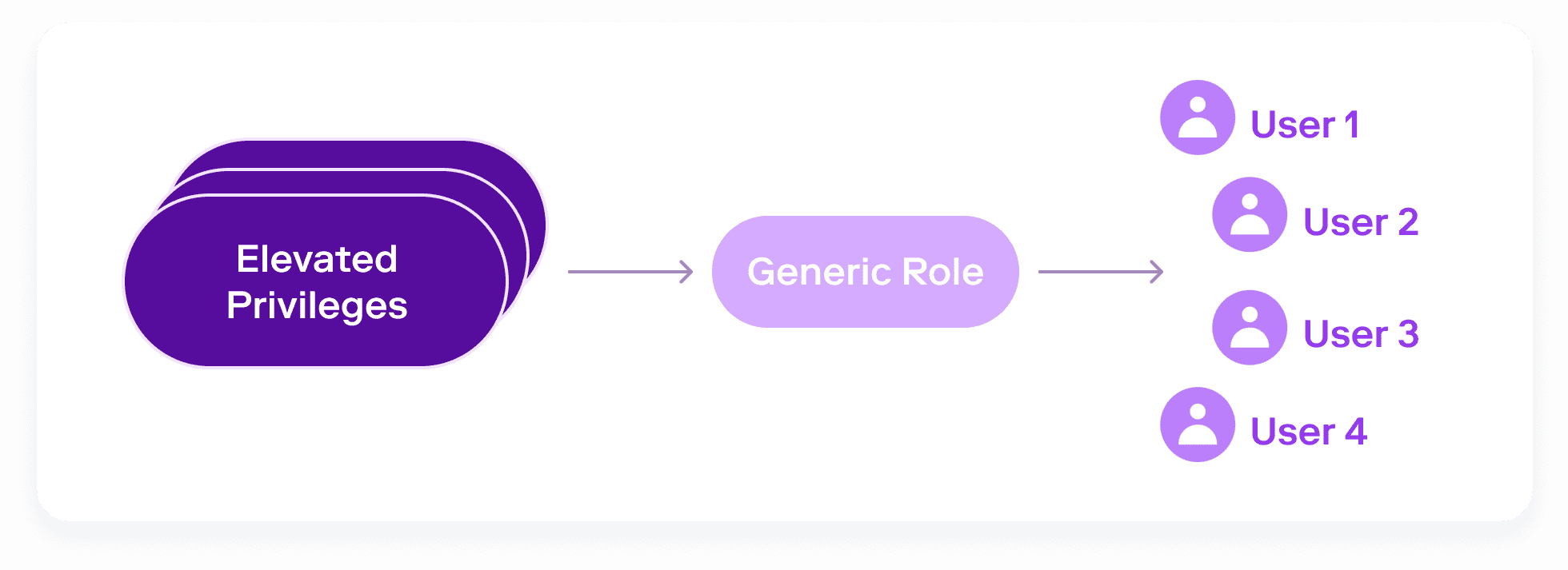
However, this poor practice accumulates tech debt over time, resulting in a snowball effect. New permissions continue to be added to these blanket roles, and more and more people are given access. The administrator is left with no simple way to back out of these decisions and apply only the necessary permissions to each user.
How to prevent Snowflake entitlement creep with Veza#
Veza is an authorization platform for data security that integrates with the major cloud providers, identity providers, databases and SaaS apps to provide a singular and central place to understand, manage, and control data access across your entire organization and for all your services (including Snowflake). Veza enables organizations to institute effective data governance through privilege automation. This includes proactively preventing entitlement creep.
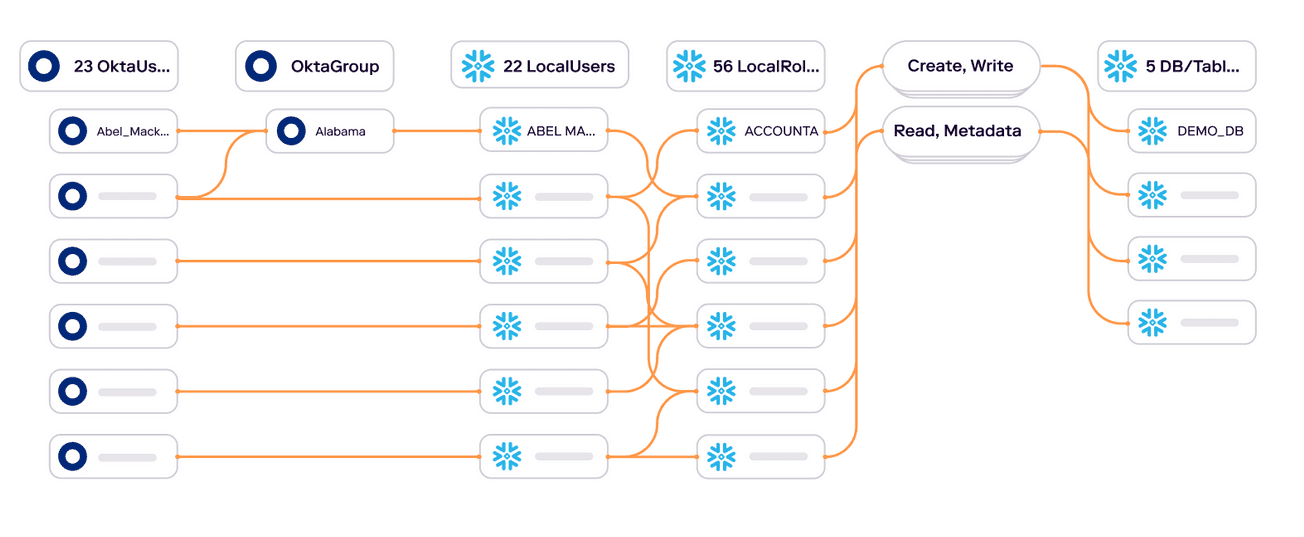
Unmask entitlement creep by understanding relationships of identities to data#
This simple example shows how the gradual creep of permissions over time, without proactive access management, can lead to undesired, and potentially harmful, results resulting in increased risk for businesses. Entitlement creep can occur for any users across an organization, including in IT, development, marketing, and product.
Why does entitlement creep happen?#
It’s the Second Law of Thermodynamics: entropy increases. Without a focused and continual effort to contain privilege it will always expand. Any organization attempting to control entitlement creep faces the following problems:
- It’s always more urgent to grant needed privileges than to remove them when they’re no longer needed. Administrators with limited time will naturally focus on tasks that unblock necessary work, causing “temporary” access grants to become permanent.
- Lack of granular insight into the effective permissions of groups and roles creates a bias towards always granting more access than is needed, since granting too little access results in additional tickets and support work.
- Organizations have no way to monitor changes to roles and associated critical permissions. For example, how many people have permission to delete rows from financial and PCI tables? Is that number higher than last week? Without this kind of visibility, permissions to critical data objects can grow unchecked.
To combat entitlement creep, organizations need to be able to visualize and manage it. By combining RBAC and authorization metadata from Snowflake with data from an identity provider (Okta, etc.), Veza reveals the effective permissions of an identity (whether human or machine) to each data object (databases, tables, etc.). For example, a simple query in Veza’s Authorization Graph can identify all identities with “write” permissions to a Snowflake table containing sensitive customer data.
Critically, Veza can reveal all access to the table, regardless of the access path. The Authorization Graph will show access held by virtue of membership in a role, whether or not the role was provisioned through an Identity Provider, and even access granted directly to a local snowflake user. Covering all paths to access lets companies understand the true extent of entitlement creep in relation to your most critical data objects in Snowflake.
Set up privilege automation to combat entitlement creep#
In addition to being able to search for, and reveal entitlement creep, you can constantly monitor for changes in access to your critical data objects in Snowflake. For example, you can use the Veza Query Builder to constantly monitor for changes to the number of users with delete permissions to customer payment data, or to the number of Snowflake admins. When a change is detected, create Rules to display notifications in Slack or email, create tickets in an ITSM like ServiceNow, or even use a custom webhook to automatically remove unwanted entitlements.
Applying privilege automation helps you to combat entitlement creep before it becomes a catastrophic problem.
Conduct intelligent access reviews#
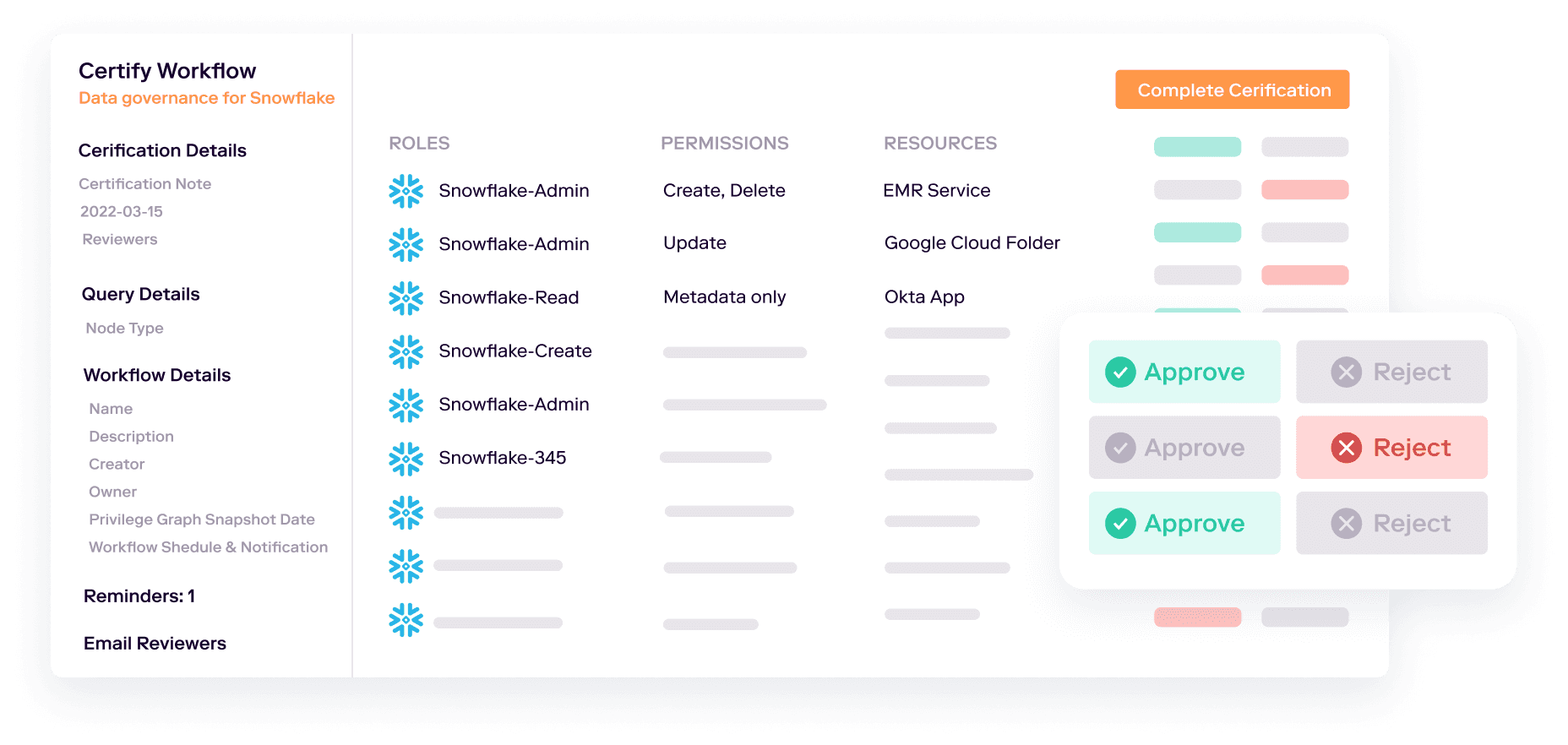
While most organizations conduct periodic access reviews, they often only review and certify an employee’s membership in groups and roles granted through your identity provider (such as Okta) or an IGA platform. This causes a blindspot in the review, ignoring access granted directly to local users. Traditional reviews also don’t allow you to drill into the granular permissions granted by groups and roles, so they’re often ineffective at reducing entitlement creep.
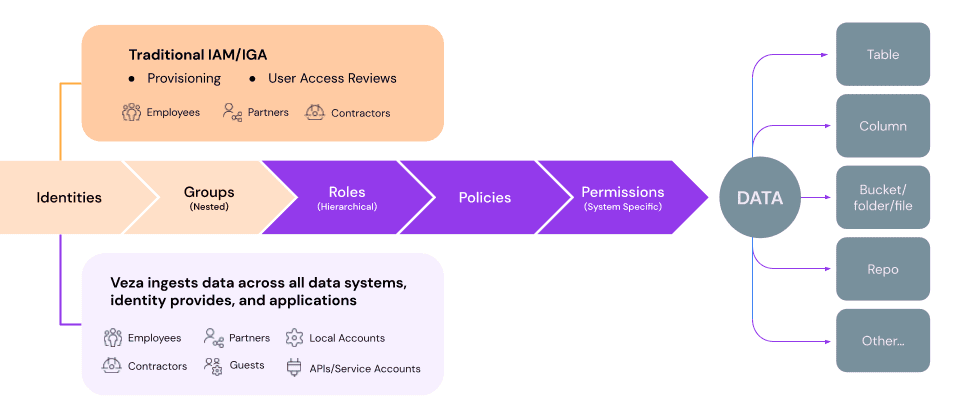
Veza’s Access Review Workflows help understand the effective permissions to data with the power of the Authorization Graph and Query Builder. By reviewing a user’s actual permissions to critical data objects in Snowflake, your access reviews become—instead of an obligatory rubber stamp exercise—an opportunity to review what permissions employees actually need, and compare it against the current reality. This method of access governance review becomes a powerful tool against entitlement creep.
Veza even provides the ability to test changes to access and identity management for a user before they are applied in production to that user. This allows administrators and IT to catch unwanted and unnecessary mistakes or changes. By simplifying and improving the management of permissions in Snowflake, Veza helps enterprises reduce future entitlement creep problems.
Veza is the privilege automation platform for tackling the problem of entitlement creep in Snowflake, especially as datasets and teams scale and grow. As the single place to go for an end to end view of the complex relationships between Snowflake objects, roles, and permissions, Veza unpacks the complexities of Snowflake identity, access control, and resource management.
Conclusion#
Many enterprises struggle to properly implement data lake security & access governance. Their lack of processes and effective tools make for an uphill battle against Snowflake access control and permissions complexities, rapidly growing data, and evolving business requirements. Entitlement creep can run rampant in these types of environments. Without the tools to visualize, monitor, alert, and implement modern access governance workflows, entitlement creep is inevitable.
Veza allows you to visualize, manage, and control the complex permissions and policies involved with Snowflake—in a way that enables your teams to exercise true access governance of identity and access management.
For more information on how your organization can leverage Veza—for Snowflake or for any component in your tech stack—contact Veza or schedule a demo today.
Table of Contents
- What is entitlement creep, and how does it happen?
- Consequences of entitlement creep
- How to prevent Snowflake entitlement creep with Veza
- Unmask entitlement creep by understanding relationships of identities to data
- Why does entitlement creep happen?
- Set up privilege automation to combat entitlement creep
- Conduct intelligent access reviews
- Conclusion