If you use a data warehouse or data lake tool such as Snowflake, you already know that as applications, users, and data multiply, it becomes nearly impossible to know who has access to what data. Proliferation of analytics apps, traditional IAM / SSO techniques, hierarchical roles, accounts, and objects make it nearly impossible to effectively govern, and secure access to data.
Veza is an authorization platform for data security that solves this visibility and access control problem. Veza maps identities (both human, and service accounts) through access control structures (such as RBAC) to data (databases, tables, etc.), making it easy to understand, manage, and control data access and giving you effective data governance, at scale.
Let’s look in more detail at Snowflake, how it manages data access, the problems this creates, and how Veza can help.
Data access control in Snowflake
When an organization uses Snowflake as a central datastore, it must consider how to secure access to its datasets. Sensitive datasets, like sales figures, proprietary customer information, and personally identifiable information (PII), bring unique compliance and governance demands. Organizations must understand who has—and who has previously had—access to the data stored in Snowflake databases or tables.
Snowflake approaches its data access controls similarly to many other relational-type database systems of the past, with a “granular object-access” model that covers the following concerns:
- Who can access what data objects?
- What operations can a given identity perform on given objects? For example, read access is different from write or delete access.
- Who can grant or change permissions for these operations?
Snowflake’s data objects are the typical database objects familiar to anyone who has worked closely with database systems of any type:
- Accounts
- Local users and roles (often multiple levels of hierarchy)
- Schemas, databases, and tables
For access control in Snowflake, privileges can be granted on objects, which can be granted to roles that can be passed down to users. In the real world, this could be seen in the following simple statement:
GRANT select # Privilege
ON customer_table # Object
TO analytics_role # RoleWith large organizations using Snowflake to house copious amounts of data, we see clearly how complex and fine-grained the data access controls around roles, users, and privileges can—and will—become.
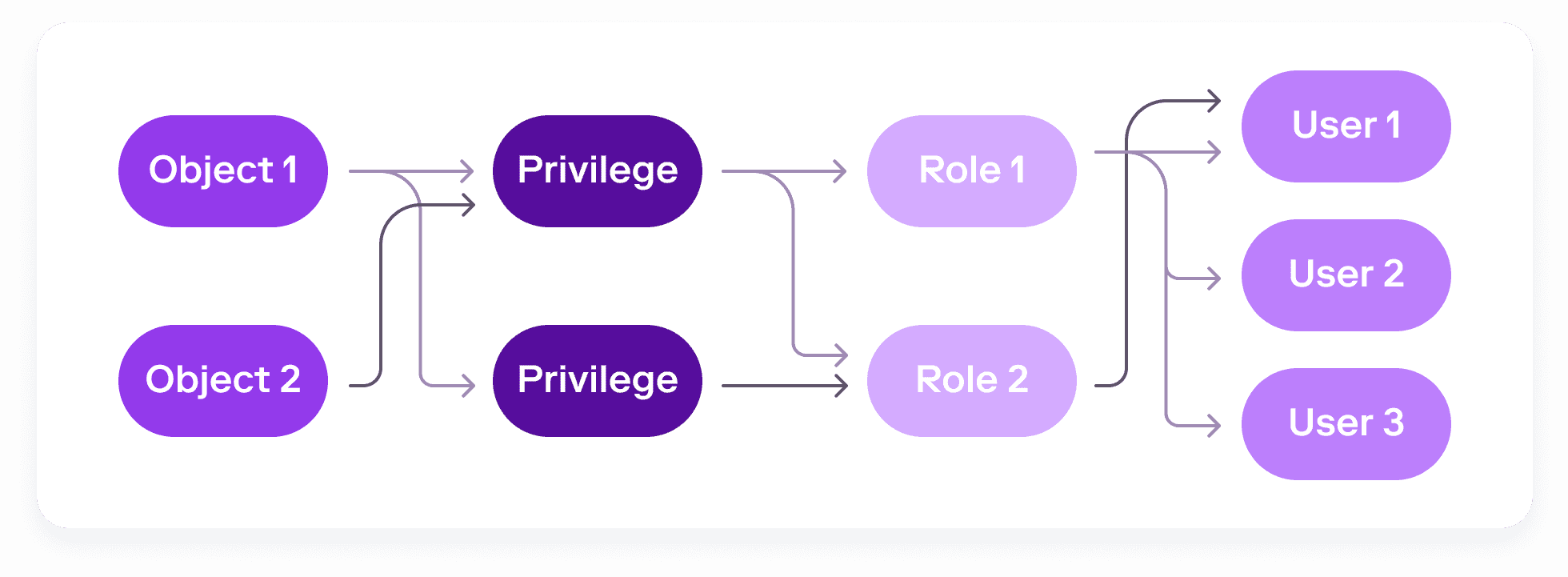
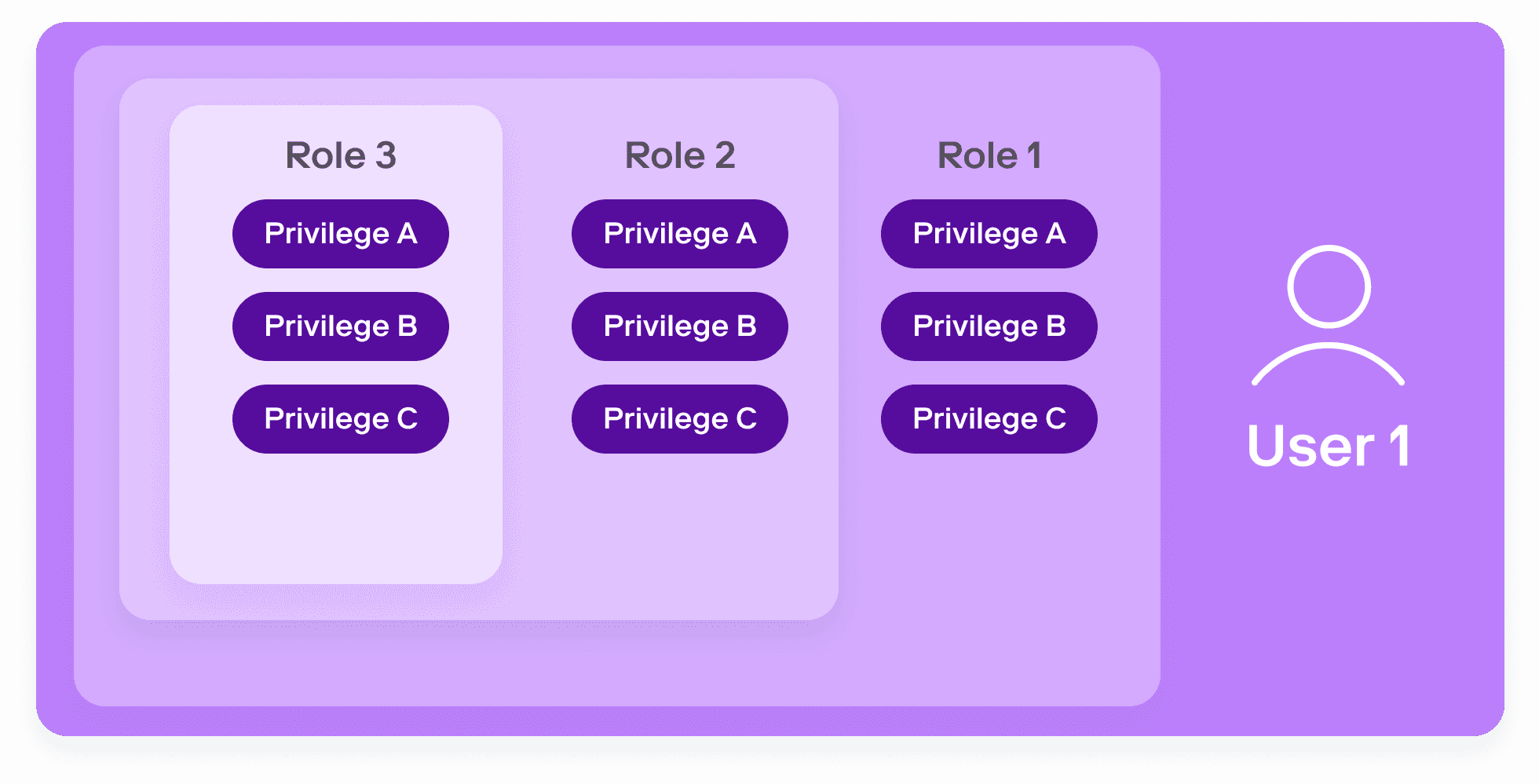
Users can be assigned to many roles, each with different, and overlapping privileges.
It’s easy to see the ensuing governance nightmare. No single role or policy tells the full story. Roles can be nested and can inherit privileges. Users can have multiple roles. Privileges absent in one of a user’s roles might be included in others, making it hard to definitively rule out whether a user can access a given object.
It simply isn’t possible to monitor and administer this complexity manually.
To be able to secure access to data in Snowflake, you first need to be able to determine who has what access to what data. But the complexity of Snowflake’s access controls make it nearly impossible to answer this question confidently at scale. Without this visibility, implementing a coherent access policy is simply not possible. Veza addresses these concerns by mapping identities to data.
Using Veza to understand Snowflake data access permissions
With Veza’s Authorization Platform, you can view, control, query, alert, and even see historically how a set of complex roles and permissions in Snowflake affects the true access of end users to sensitive datasets.
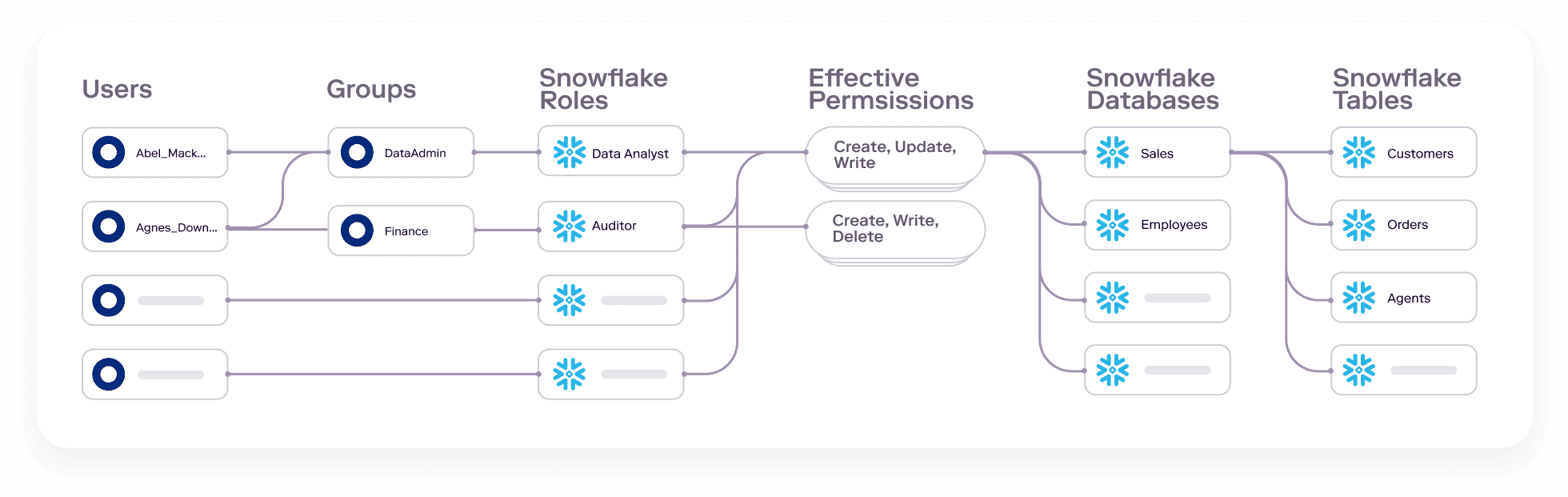
Visualize identity-to-data relationships
Veza integrates with an enterprise’s identity providers, cloud providers, apps, and data systems to capture authorization metadata. By connecting all these systems together, Veza can visualize and clearly help you understand direct identity-to-data relationships. For example, you could search for all Snowflake tables a particular user can access, or surface a full list of users with delete access to a particular table.
Veza also ingests Snowflake Tags. When managing a large number of objects, filtering by Tags can help you identify and focus on key data assets, for example, tables that include personally-identifiable information (PII).
Understand effective permissions
You don’t need to understand the exact role structure your organization uses, or the exact permission names used by Snowflake. Veza translates this information into the simple language of effective permissions: Create, Read, Update & Delete. This means that security teams, governance teams, and even external auditors can easily understand exactly what access any user has to a particular data resource in Snowflake without using Snowflake-specific permission terms
Track the history of permissions for threat response
If a compromised identity is discovered, you need to know what access the identity had at the time of the incident, not just the current state. Veza’s Time Machine capabilities capture changes to permissions over time, allowing you to wind back the clock and see what permissions an identity had at a previous time. This historical view is crucial for quick and effective damage control when responding to a threat or potential attack (insider attacks, cyber attacks, ransomware, privilege drift, etc.).
Constantly monitor for least privilege violations
Instead of waiting to stumble upon misconfigurations, Veza’s continual monitoring and automation allows you to surface and fix these problems as soon as they appear, before they become an expensive issue.
With Veza you can constantly monitor for common access misconfigurations, such as orphaned accounts. When violations are discovered, Veza automates the first steps of remediation by alerting stakeholders. For example, you can deliver notifications to Slack or email, automatically create a ticket for your ops team in ServiceNow, or even create a custom webhook to automatically revoke unwanted access.
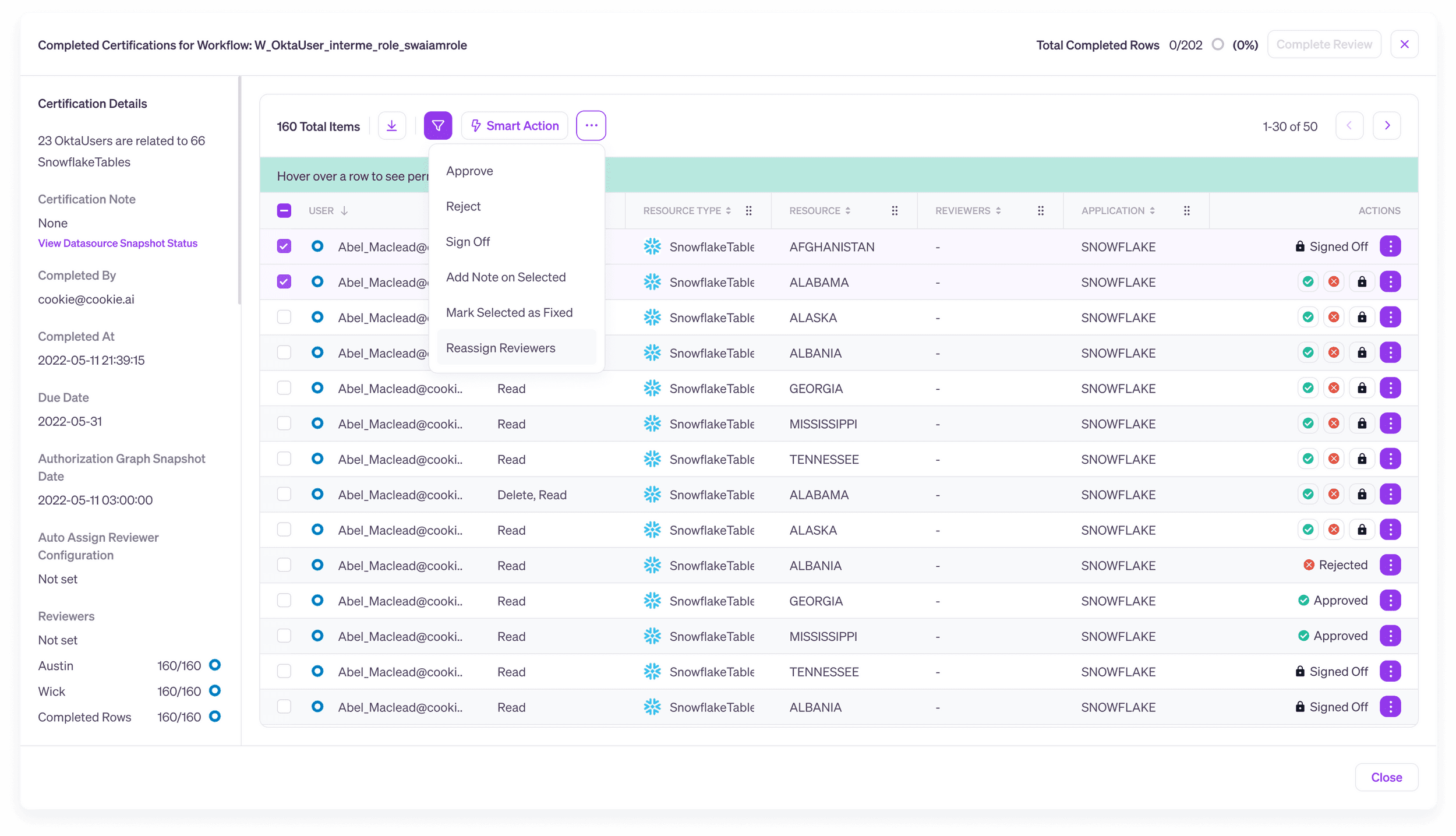
Conduct intelligent access reviews
Traditional access reviews are often conducted on the basis of identity provider groups, or roles. But just knowing the name of a group or role isn’t enough to know the real permissions a user has. Roles can conceal complex nested permission hierarchies and the permissions given by a role can change over time, moving away from the original role name. For example a role labeled “read-only” can easily come to contain write or delete permissions. Traditional group- or role-based access reviews can gloss over these complexities, leading to rubber-stamp processes that don’t help you combat excess privilege and may even fail to meet audit and compliance objectives – all ultimately exposing the organization to increased risks of data breach.
Veza’s Access Review Workflows let you create custom review processes that reflect the actual effective permissions of each user for sensitive data in Snowflake. Reviewers can accept, reject and certify the actions each user can take on Snowflake databases and tables, not just rubber stamp membership in a group or role.
Conclusion
It’s become clear that Snowflake’s incredibly flexible and versatile access control structures can quickly turn into a compliance and governance nightmare, especially when sensitive data is involved.
With the growing volume and complexity of data collected by modern organizations, restoring the relationship between identities and data is the only way to effectively manage Snowflake permissions and identity at scale. It is no longer possible for a single person—or even a team of people—to manually manage complex data access with confidence and clarity.
By helping organizations answer the not-so-simple question of who has what access to what data in Snowflake, Veza changes the game for organizations seeking to meet regulatory, compliance, and access governance needs. With Veza’s real-time search, queries, alerting, and activity monitoring, along with historical timelines, organizations can save time and quickly find answers to compliance and governance questions involved with managing a complex data access landscape.
For more information on how your organization can leverage Veza—for Snowflake or for any component in your tech stack—contact Veza or schedule a demo today.