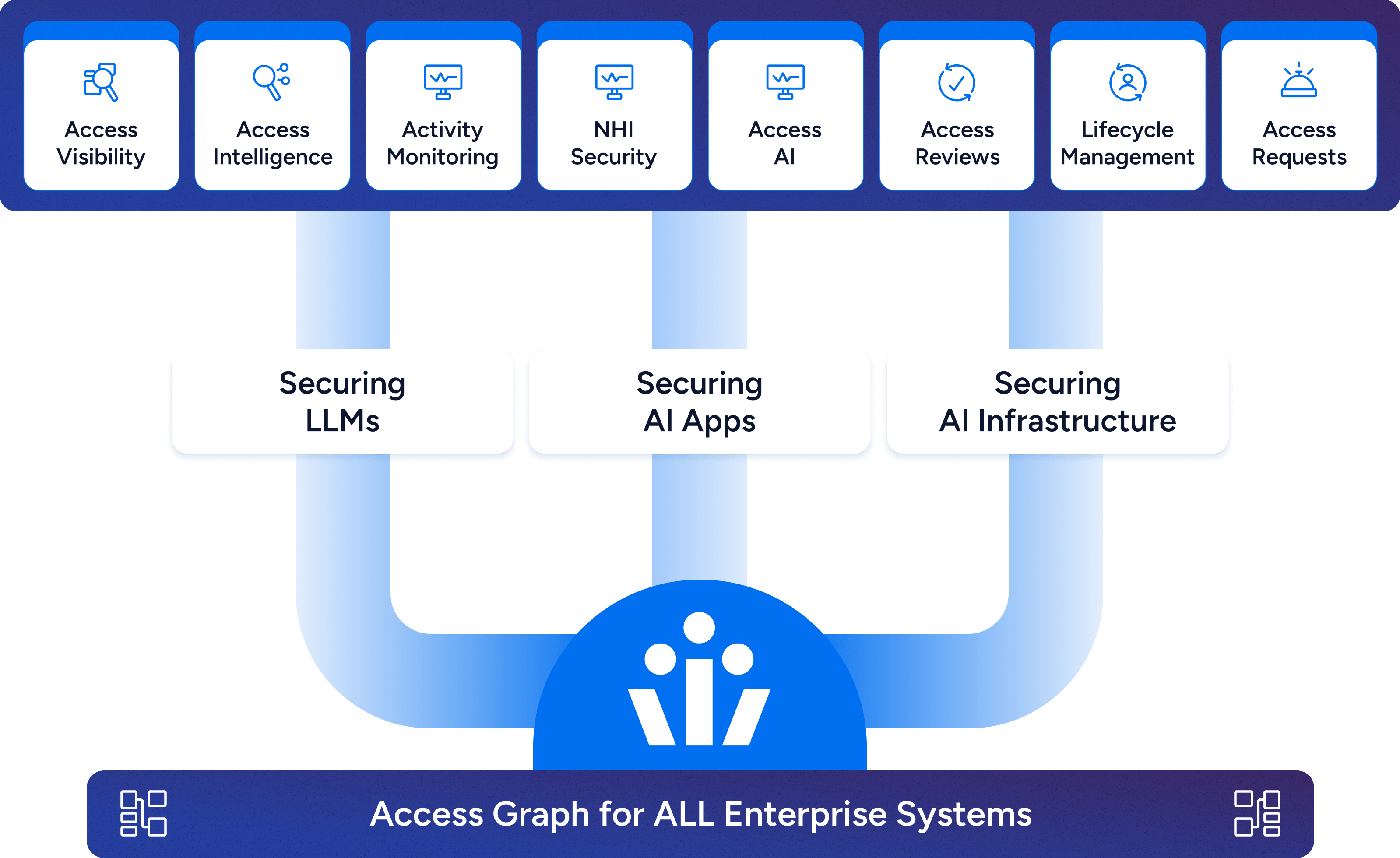
One platform for enterprise-wide access governance
Veza’s Access Platform unlocks the truth of access permissions, powering security and governance initiatives across your organization.
Our Solutions
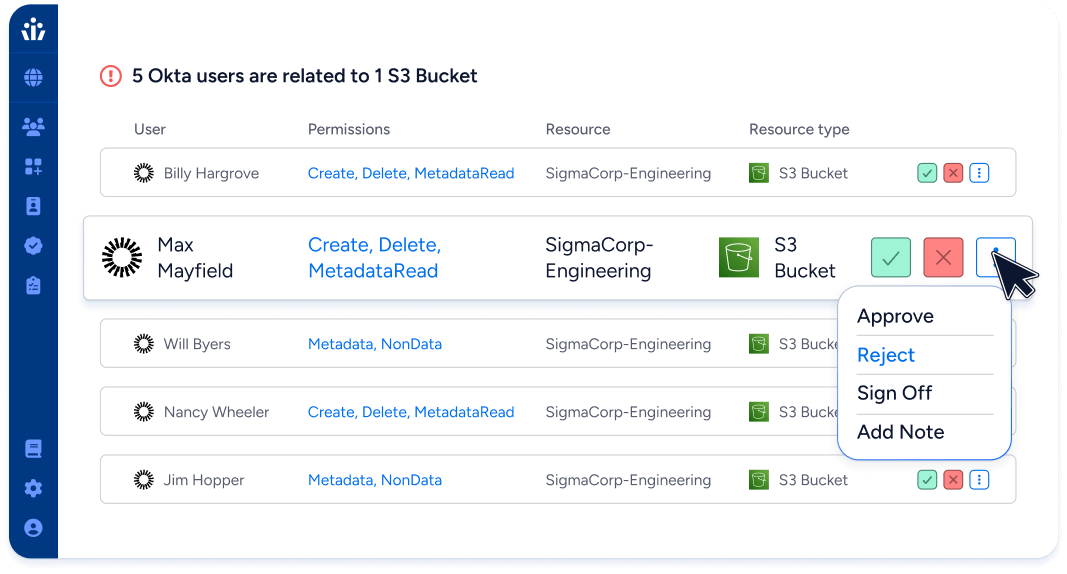
Privileged Access Monitoring
Visualize and control data access across all systems, proactively mitigating risks for both human and machine identities.
- Control permissions, identify unused access, and manage privileged accounts.
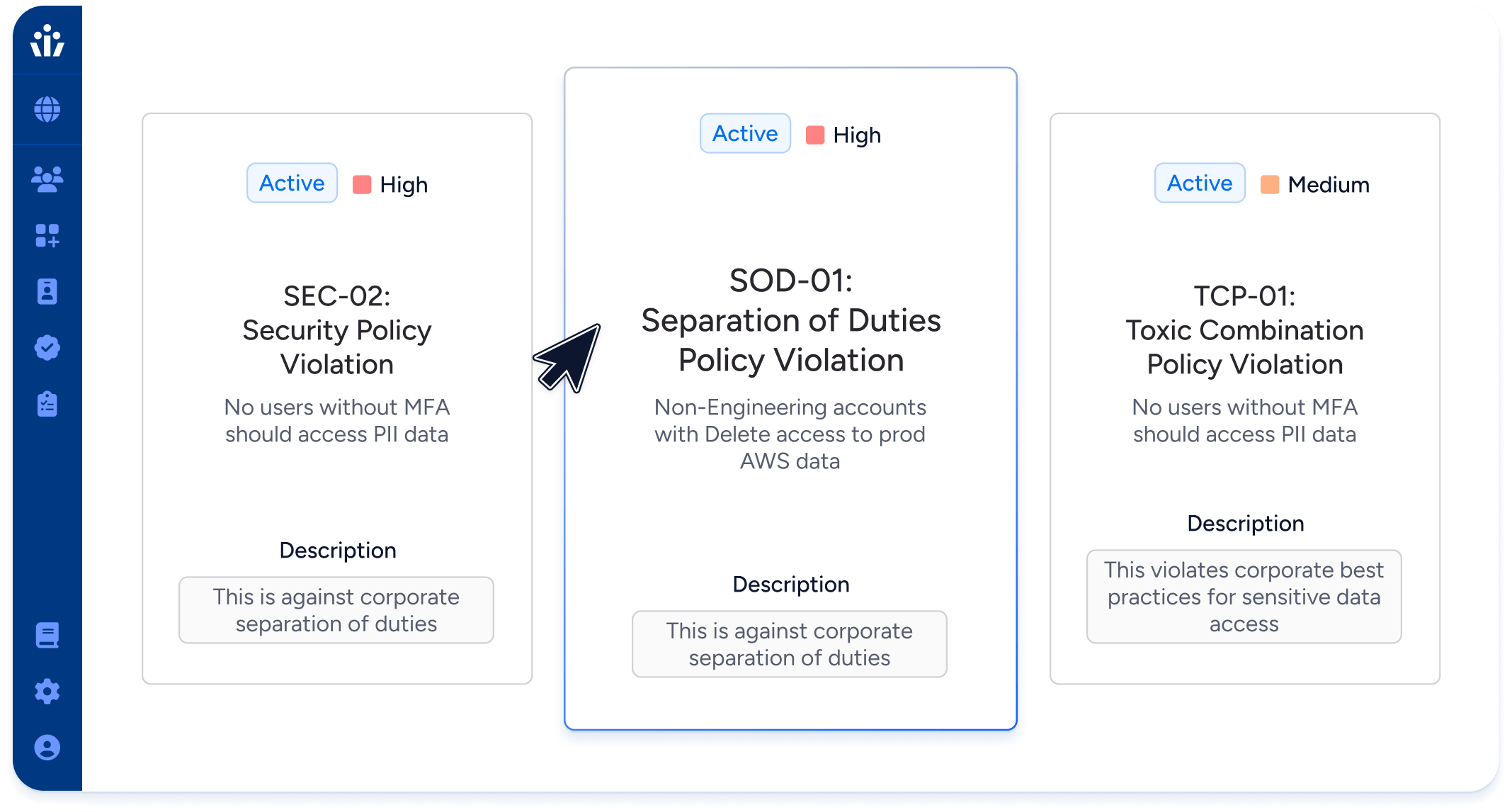
- Automate scans for policy violations related to SOX, SOC 2, NIST, GDPR
- Quickly assess the detailed access of compromised identities to prioritize incident response.
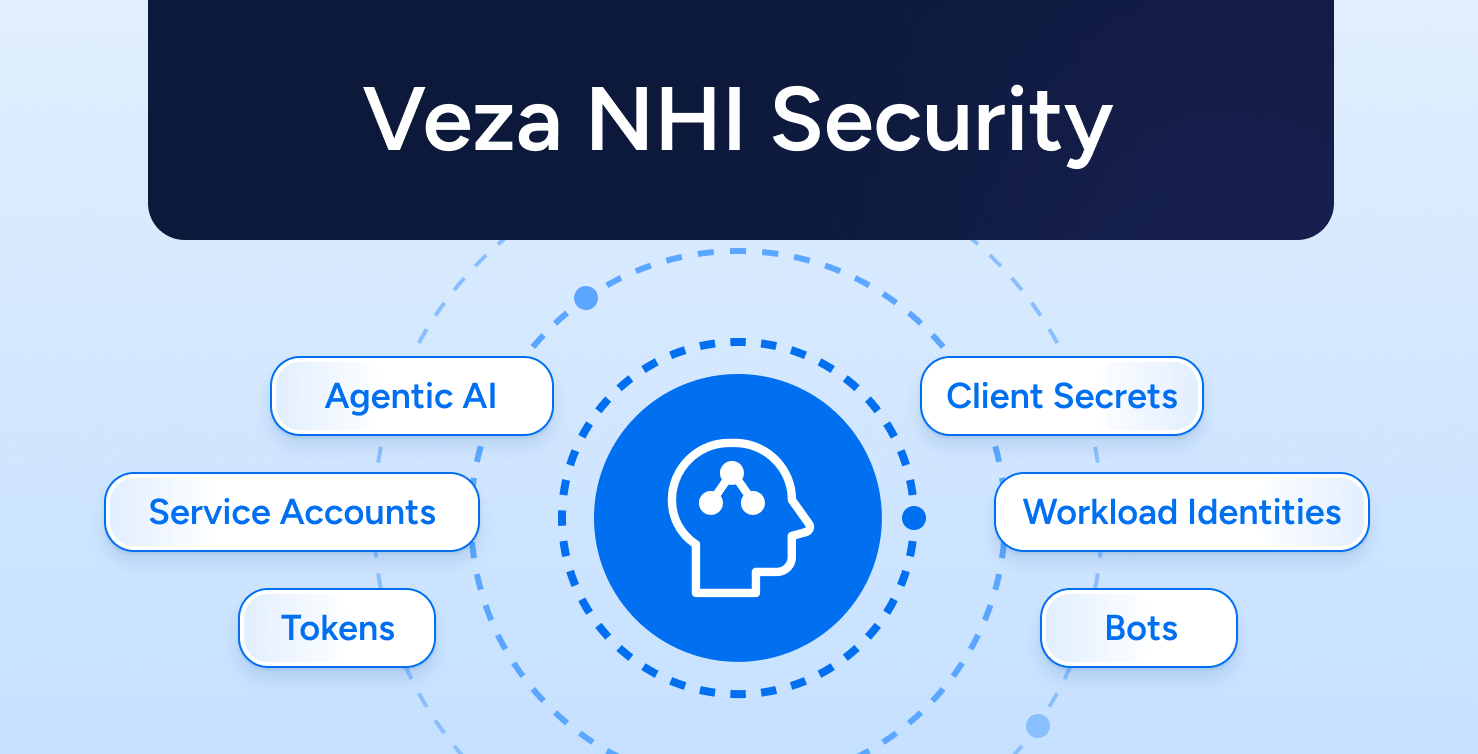
Non-Human Identity Management
Hackers are attacking NHIs because they know they can avoid human-focused security tools like MFA, so your security and compliance strategies must adapt to secure NHIs as first-class citizens.
- Discover NHIs efficiently across on-prem, SaaS apps, custom apps, and cloud infrastructure.
- Analyze permissions and activity of NHIs to identify and remove unneeded privileges, including admin permissions, without disrupting business-critical processes.
- Enforce security policies like key rotation for NHIs, and provide useful context to access reviewers, like “Time last rotated” and “Time last used”.
- Create a single streamlined provisioning processes for both human and non-human identities that maintains least privilege.
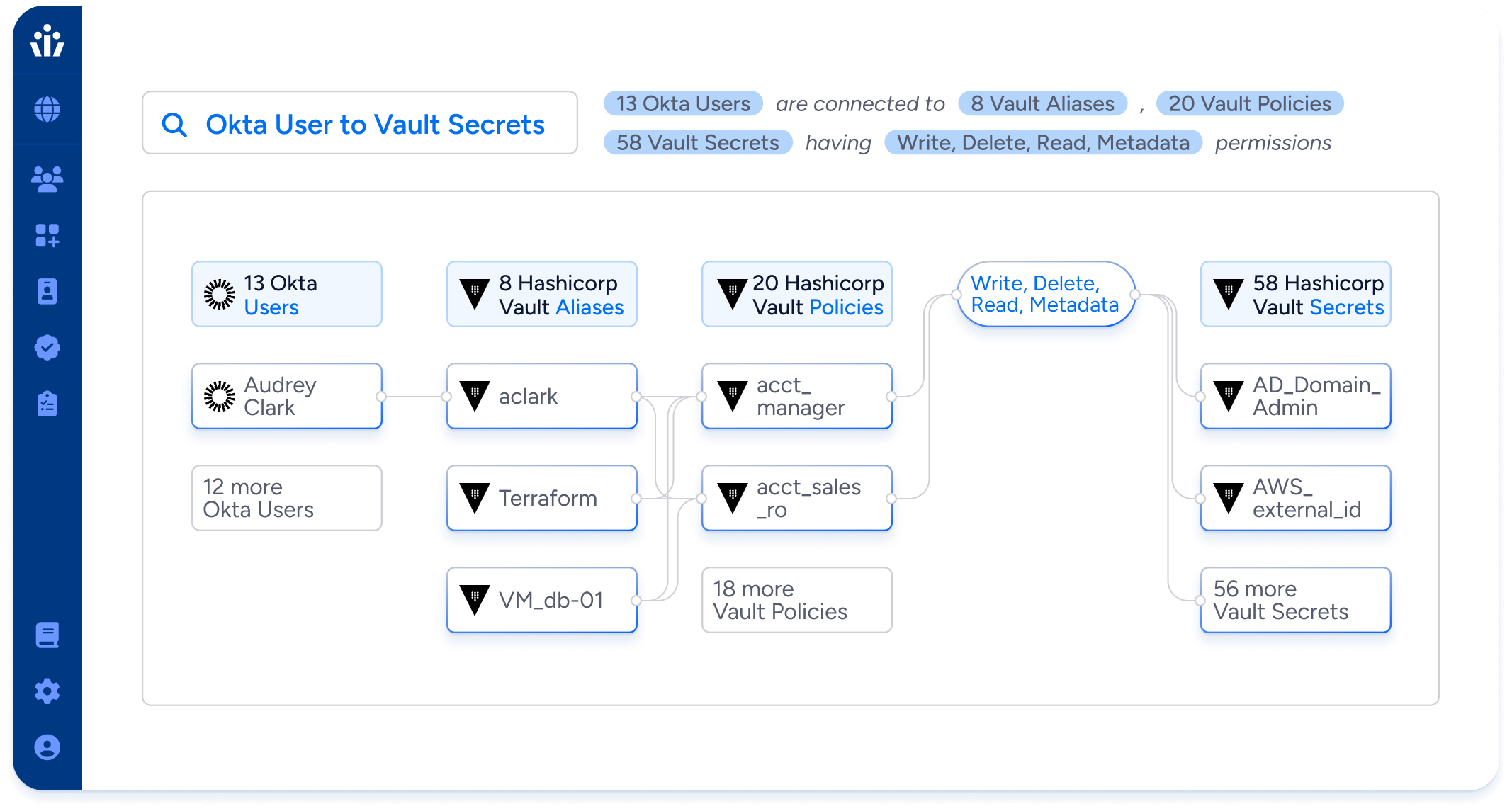
Cloud Access Management
Untangle the complex web of cloud IAM to know exactly who can do what across AWS, Google, Azure, and Oracle.
- Find and fix cloud IAM misconfigurations that enable privilege escalation and lateral movement.
- Root out inactive IAM users, dormant service accounts and ungoverned local users.
- Fix your top cloud access risks before they can be exploited.
- Identify your high blast radius users: identities with broad access to cloud resources and represent the greatest risk if compromised.
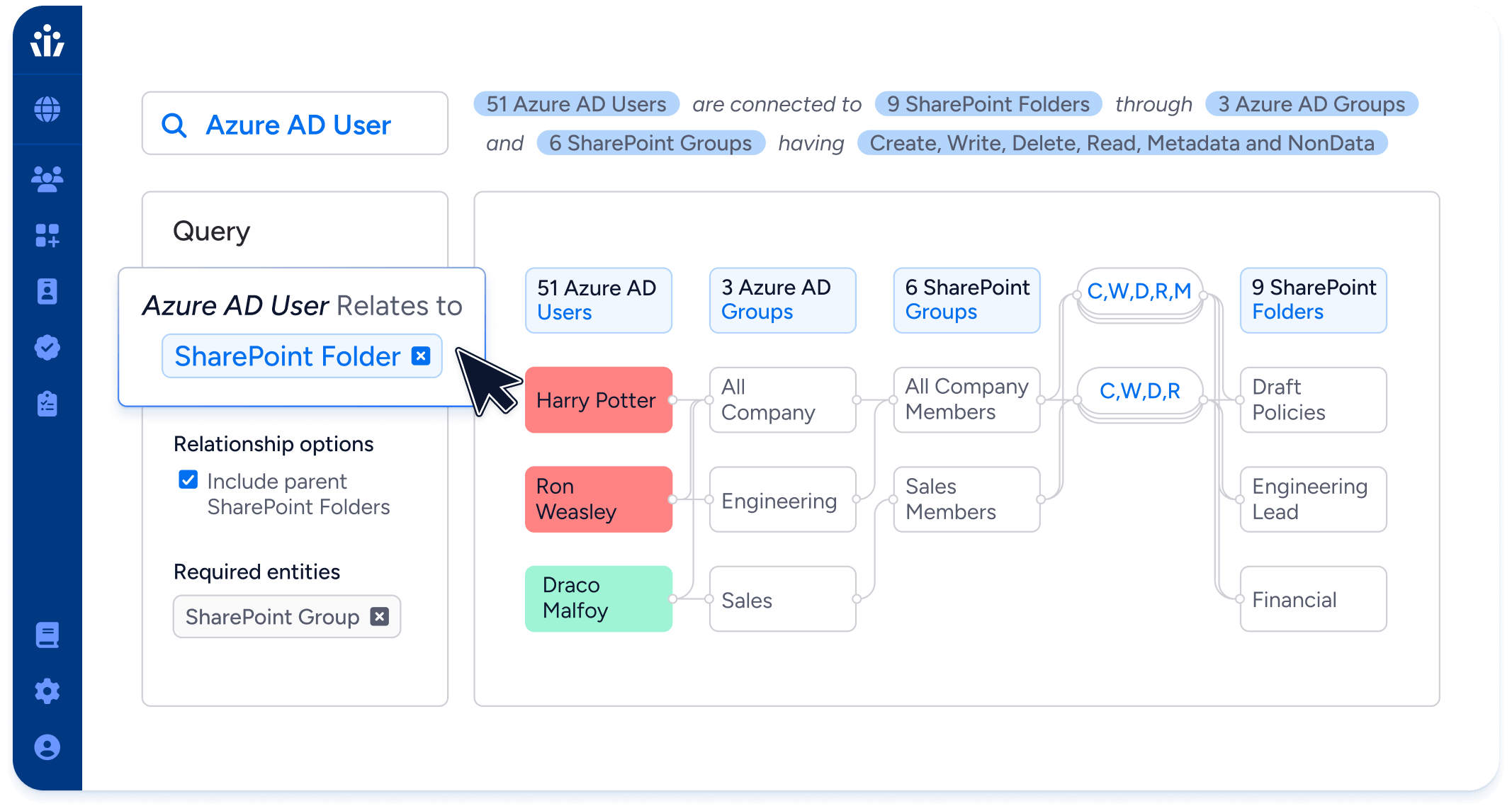
Data System Governance
Understand and control access to unstructured data, in your data lakes, ML datasets, shared drives, and cloud storage.
- Integrate with data tagging and classification tools to build sophisticated access queries. For example, can identities outside the finance team access any resources containing PCI data?
- Continuously monitor for new access to sensitive data in storage buckets, fileshare systems, and data warehouses.
- Assess blast radius by finding users with unnecessary or broad access to Sharepoint sites, data lakes, and shared drives.
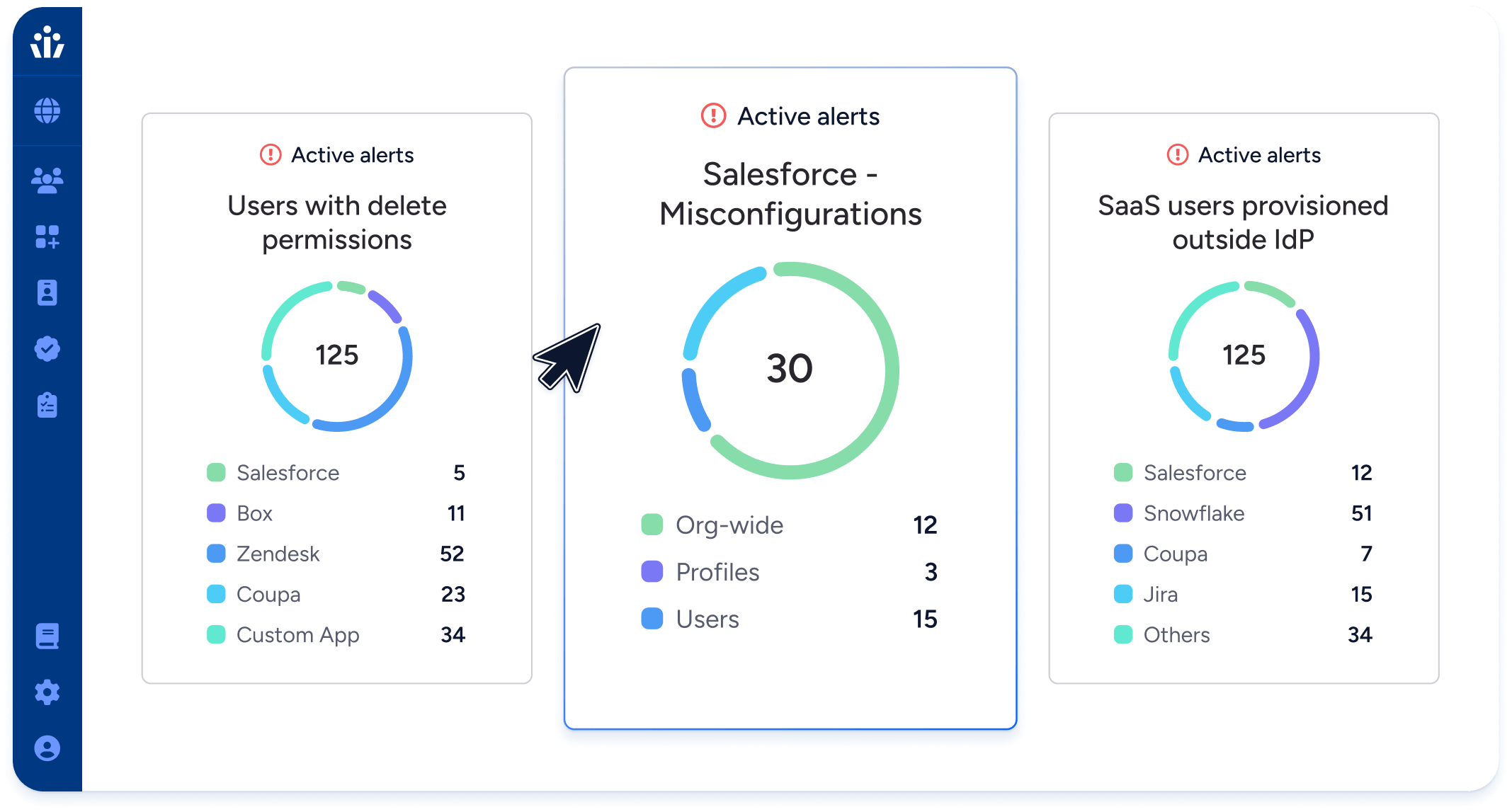
SaaS Access Security
Visualize and control data access across all systems, proactively mitigating risks for both human and machine identities.
- Control permissions, identify unused access, and manage privileged accounts.
- Automate scans for policy violations related to SOX, SOC 2, NIST, GDPR
- Quickly assess the detailed access of compromised identities to prioritize incident response.
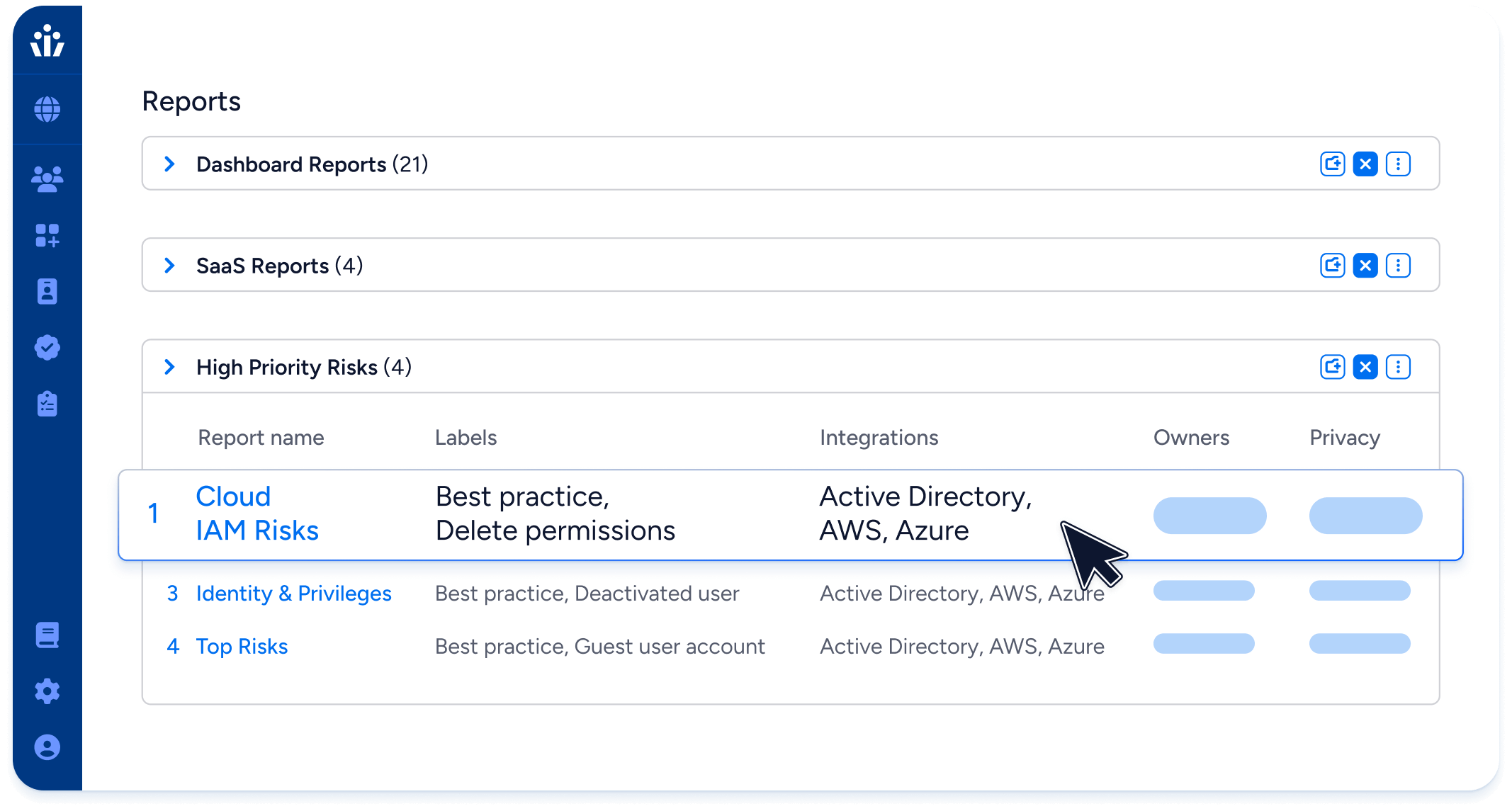
Next-Gen IGA
Enforce least privilege & compliance with access reviews based on the effective permissions of identities.
- Automatically compile review and certification campaigns covering your cloud environments, on-premise systems, and SaaS apps.
- Integrate with SOAR and ITSM systems like ServiceNow and Jira to implement access review decisions consistently and fast.
- Demonstrate compliance with SOX, ISO 27001, GDPR and other frameworks, 7x faster than with manual reviews
Agentic AI Security
Secure access to LLMs, AI-powered applications, and the infrastructure they rely on. Gain visibility and control over AI agents and the identities they act on behalf of, ensuring responsible and governed use of AI across the enterprise.
- Enforce least privilege for AI models, applications, and compute resources across AWS Bedrock, OpenAI, Microsoft Copilot, and more.
- Leverage GenAI-powered search to answer complex access questions across all identities, systems, and permissions – powered by Veza Query Language (VQL)
- Rapidly build secure integrations for Enterprise systems using GenAI.
- Stay audit-ready and compliant with AI-driven access reviews, role reviews, and policy validations.