Privileged Access Monitoring
Don’t let unauthorized users and privileged users slip through the cracks of your IGA or PAM tools. Use Veza to find and fix privilege violations with your data systems, SaaS apps, and cloud services.
Take charge of high-risk identities
For all your identity security teams
Identity & Access Management (IAM)
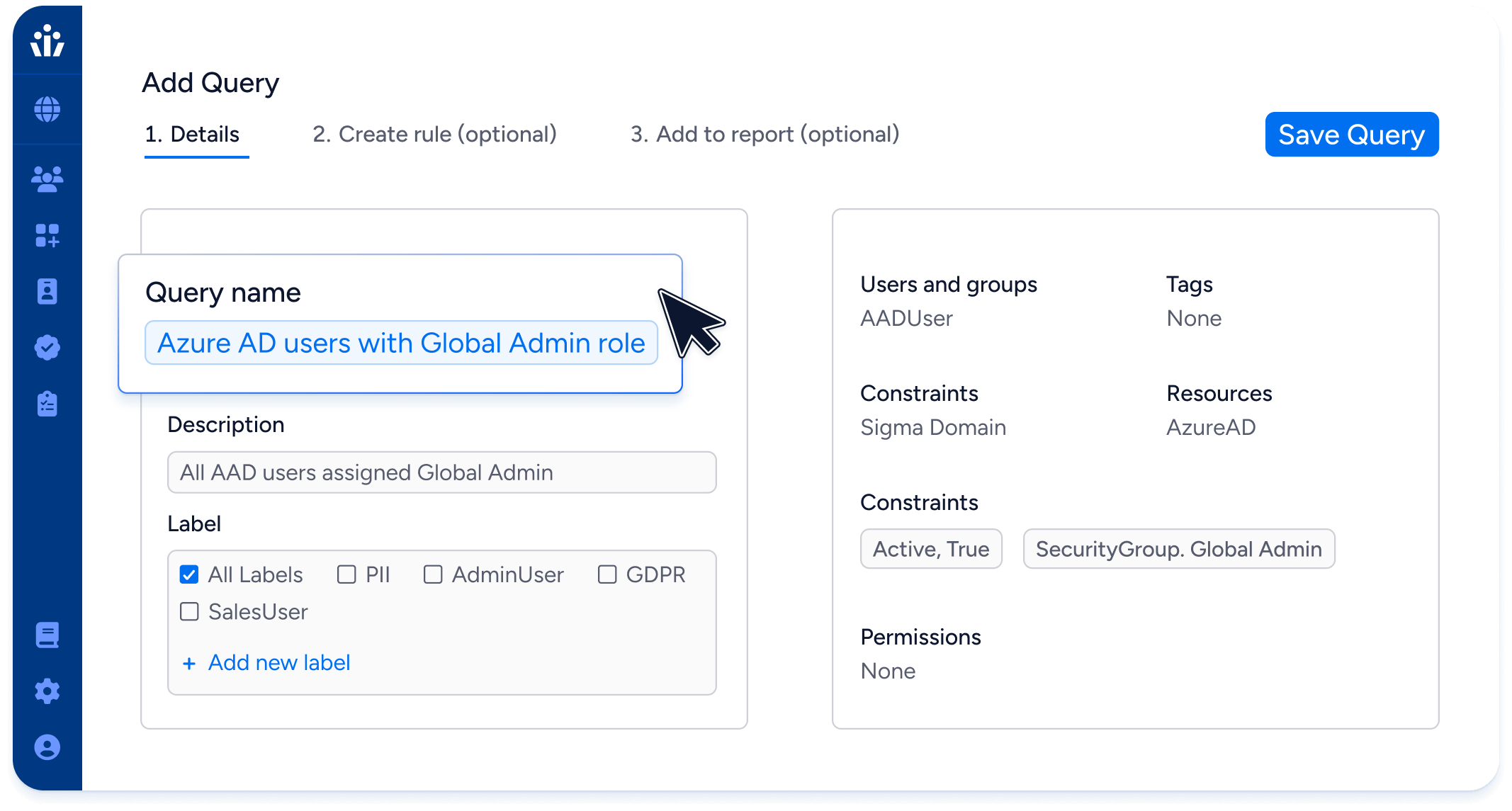
Ensure complete onboarding & offboarding of privileged accounts—human or machine—by checking all cloud and on-prem apps, data systems, and cloud IAM systems.
Automatically trim dormant privileged access.
Trim access to individual objects like Snowflake tables or GitHub repositories based on usage.
Assign the least permissive role possible for ad hoc access requests to any resources.
Security and Risk Management (SRM)
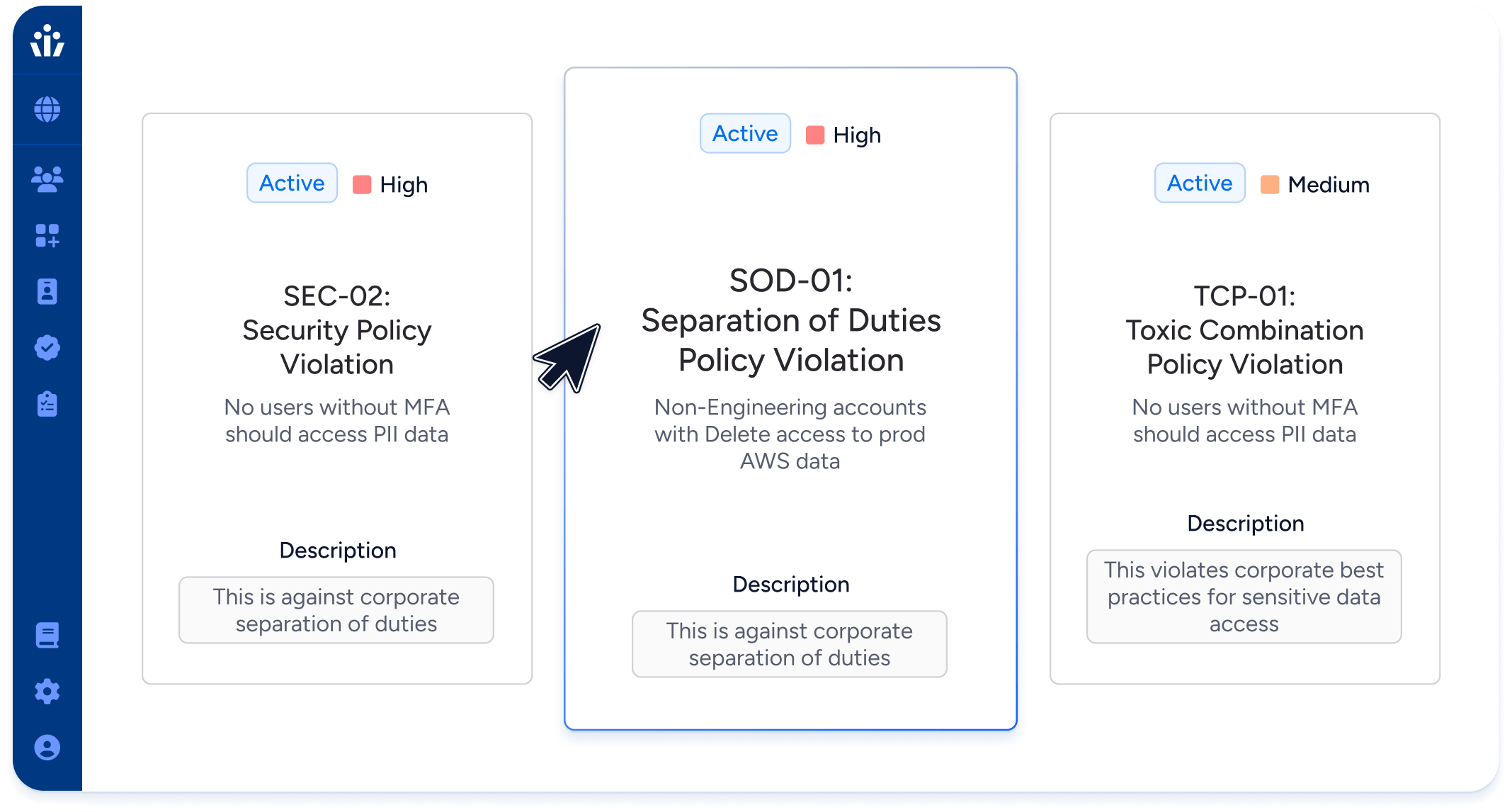
Provide reports to auditors that don’t miss privileged local users
Enforce policies for identity security posture such as requiring MFA
Enforce policies for toxic combinations or separation of duties (SoD)
Provide access reviews with privileged monitoring information and intelligence
Security Engineering & Security Operations
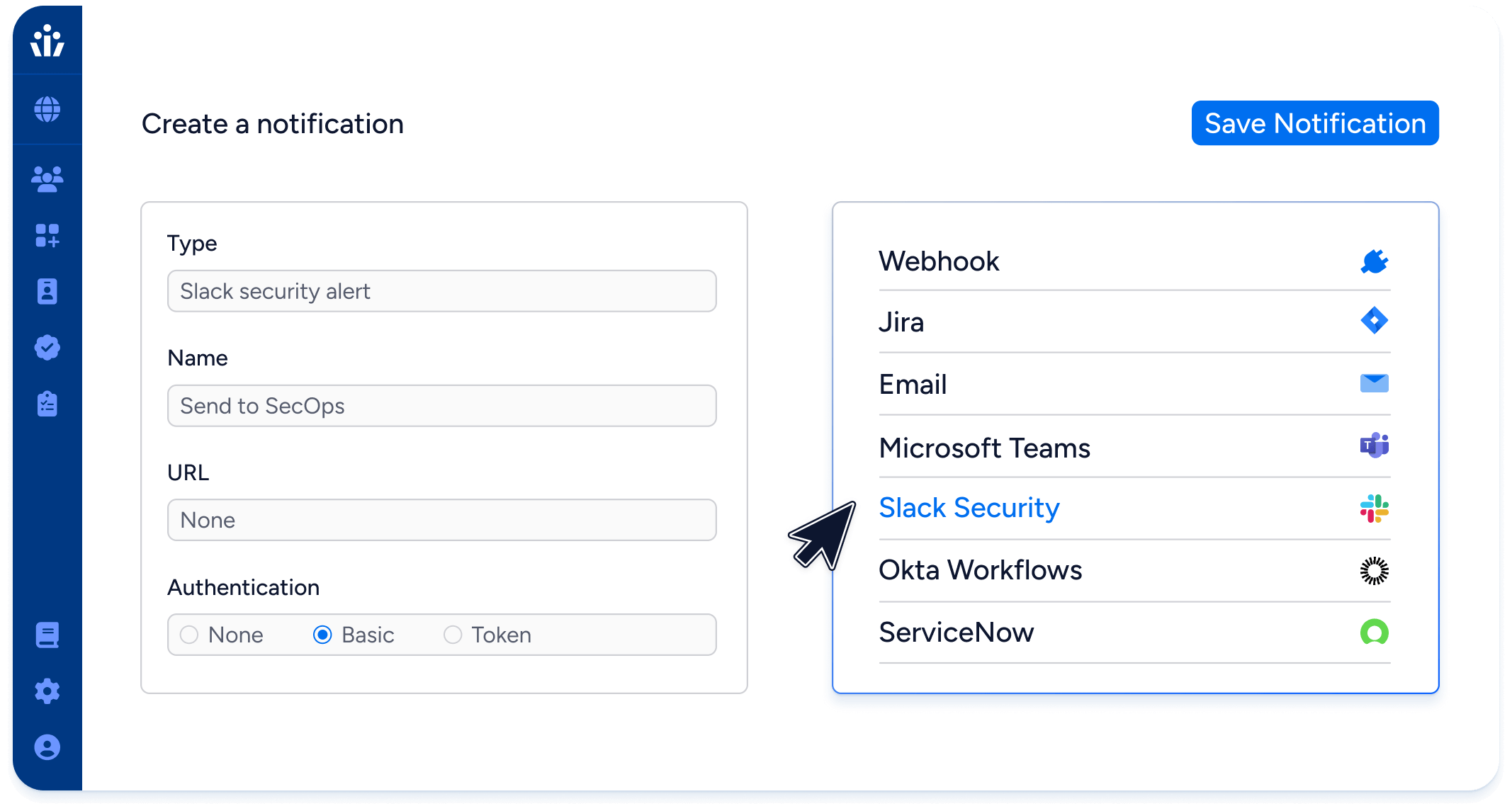
Remediate risks and violations in real-time with alerts or ITSM tickets in ServiceNow, Slack, or JIRA.
Analyze historical access and blast radius to detect and respond to any compromised account.
Pinpoint unused permissions to remove privileged accounts without impacting user experience.
Leading enterprises trust Veza for Privileged Access Monitoring






With Veza, we have end-to-end visibility over our cloud data access footprint; we’re able to quickly identify excess RBAC control and manage privileged access – and that gives us the confidence to adopt new cloud technologies and migrate from on-prem to cloud at lightning speed.
Matt Paull | Managing Director, Technology Management





