Data security is both the most critical element of modern cybersecurity, and in some ways the most neglected. Simply put, data security consists of protecting data from unauthorized access, whether by hackers or company personnel, in order to prevent theft, corruption, misuse, regulatory compliance violations, and other risks. The importance of data security can’t be overstated; as Gartner states in its report on Top 2022 Risks, “the majority of the most important enterprise risks center on data and technology.” In this light, and given the critical role of data in the digital era, one would expect its protection to be the top priority for security professionals. Yet for all the talk of “protecting what matters,” the evolution of data security strategies and solutions has often lagged far behind measures focused on infrastructure and applications. Organizations have plenty of ways to manage access to resources, but not to manage permissions for the data they contain.
As data increasingly moves to the cloud, organizations need more effective ways to manage access, authentication, and authorization for data wherever it resides.
Data security is identity-centric and granular
Data security starts with identity: ultimately, organizations need to understand who (or what) can access and control what data. Tools for application and infrastructure security can use identity to authenticate and authorize users on a system level, but they can’t provide the more granular control needed for data security. After all, data entitlements are rarely an all-or-nothing proposition; a database will often contain both highly regulated data such as personally identifiable information (PII) or financial records, and other less sensitive data. A given user or service may be authorized to access some rows or columns of a table, but not others. They may be able to read more data than they’re allowed to write or delete.
To leverage their data effectively while limiting risk, organizations need a way to manage the exact data each identity can access as well as what it can do with it. And to support a zero trust security model, they need a way to discover and remove excess privileges at the same granular level.
Cloud-native data systems have intensified the data security challenge
When data lived in the data center, it was relatively simple to manage who could access and control what data. Now, in the second wave of enterprise cloud, organizations are moving vast amounts of data to the cloud. As solutions like Snowflake, Redshift, and Databricks transform the data ecosystem, organizations need to be able to extend consistent data security and access governance across a multi-vendor mix of cloud environments, data warehouses, data lakes, and data lakehouses, as well as on-prem servers and databases. This means enabling users and services to access the data their role requires, wherever it resides; managing cloud entitlements while mitigating the risk of cloud misconfigurations; monitoring and auditing these entitlements to enable compliance and support zero trust, and doing all of this as efficiently as possible to keep your business healthy and productive.
Zero trust data security depends on authorization
To address the data security challenges posed by the cloud, it’s not enough just to manage access and authentication. Organizations also need to be able to see and manage what people and services are allowed to do with the data they can access, across their entire hybrid and multi-cloud environment, through a single pane of glass. The continuous verification and least privilege access called for under the zero trust security model is beyond the capabilities of data loss prevention tools, which offer a layer of protection for shared documents and content but can’t manage permissions for sensitive data on the level of individual database tables, rows and columns. Similarly, multifactor authentication (MFA) can help prevent unauthorized access to applications and infrastructure—but as noted in the Verizon 2021 Data Breach Investigations Report, the vast majority of data breaches today are “predominantly driven by unapproved or malicious use of legitimate privileges.” More is clearly needed.
Consider the implications of authentication and authorization for ransomware. In order to succeed, attackers must be able to not only access data, but encrypt it as well. According to zero trust, the permission to encrypt data should be granted to a smaller subset of privileged accounts than the broader set with read-only permissions. To date, most organizations still can’t determine which accounts actually have encryption permissions, or whether they should, leaving them at greater risk of a ransomware attack.
Most hackers aren’t after your application. They’re after the data in that application. Securing that data has become more challenging than ever in today’s multi-cloud world—and more critical. By prioritizing data security, organizations can protect what matters while leveraging the full value of enterprise data.
Ben Doyle || CIO, ATN International
Data security in practice
By moving beyond infrastructure and application security to a mature data security capability, implemented through a centralized platform with a single pane of glass across the data ecosystem, organizations can gain the visibility and control needed to fully leverage their enterprise data without undermining security or compliance. The value of this approach can be seen across a broad set of benefits.
- Simpler data discovery, visibility, and classification – With a full understanding of who has access to what data across the entire hybrid or multi-cloud data ecosystem, and a comprehensive view of all data activity, organizations can reduce security risks and more easily complete tasks such as audit and compliance reporting.
- More effective data access controls – By consolidating authorization data from disparate systems into a single identity-to-data map, organizations can be more confident that enterprise rules and security protocols are being applied consistently across data sources, and safely supply, manage, and remediate permissions as needed.
- Least privilege access – By using a data security platform to identify unnecessary, outdated, or inappropriate entitlements, organizations can limit exposure to attack and improve compliance without posing undue barriers to productivity.
- Timely and accurate data – The value of data often relies on its freshness. With a better way to manage data governance across multi-cloud systems and solutions, organizations can grant the authorization required for regular updates while maintaining strict visibility and control to prevent excess privileges from increasing risk.
- Comprehensive entitlement management – Regular entitlement reviews are essential to identify users with outdated privileges, but completing them across a multitude of data stores throughout the hybrid, multi-cloud environment can be a time-consuming and onerous task. By taking a centralized, platform approach to data security, organizations can manage entitlements across disparate data stores more easily and efficiently with full identity context across cloud identity, service accounts, and local users.
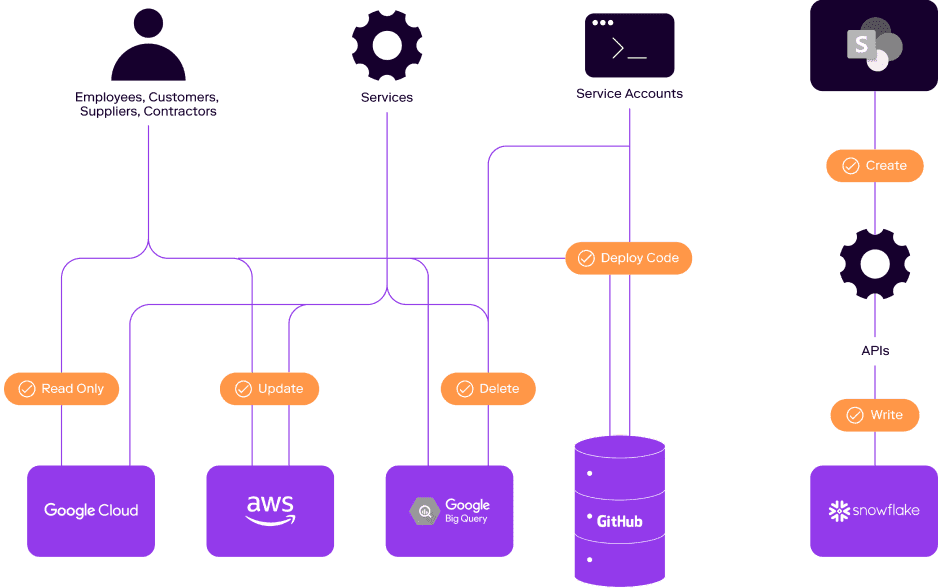
Meet Veza
Veza is the first cloud data security platform built on the power of authorization. With Veza, organizations answer the critical question of “who can and should take what action, on what data.”
Our solution extracts system-specific authorization metadata from key enterprise tools – identity providers, cloud IAM, apps, and data systems, and parses this metadata in a single control plane, all delivered through the easily understandable language of effective permissions. With Veza, organizations master the complexity of authorization and confidently unlock the value of their data.
Veza is here to help your organization move beyond the limits of infrastructure-centric security and start fully leveraging data, securely. To learn more, sign up for your free demo hhttp://veza.com/schedule-demoere.





