Many of us remember the days of the Nigerian Prince email scams. Well, social engineering hasn’t gone anywhere, and techniques are only growing more sophisticated. In fact, in 2021, over 85% of companies reported that at least one employee clicked on a phishing email. Since the days of mass email scams, phishing has branched out into newer categories, including spear phishing, a targeted form of social engineering focused on making highly convincing outreach to a few individuals instead of blasting communications to as many recipients as possible. Whale phishing or “whaling” attacks are a form of spear phishing that specifically target high-level executives in the hope of exploiting their privileged identities to compromise sensitive data, plant ransomware, or steal money.
Whaling attacks employ a highly personalized approach that can be extremely effective in building credibility with targets and exploiting their access. However, these threats require substantial investment from the cyber criminal due to the research, time and capital required to create believable phishing outreach.
More sophisticated attacks will approach a potential “whale” on several devices or applications at once. A target may receive a credible looking phishing email, for example, followed up by a fraudulent text from the same impersonator to build further credibility. Spear phishing attempts often expand into full campaigns rather than single outreach attempts, making them more difficult to detect.
Whaling attacks can present themselves in two ways:
- Threat actors send personalized, believable scam communication to high-level executives. This outreach may cite time-sensitive business operations as an excuse to drive urgency, or reference a current project to build credibility.
- Targeting employees by impersonating high-level executives who are requesting sensitive information including financial intelligence, PII or access credentials.
The impact of Whale Phishing
Threat actors are investing more effort in phishing attacks than ever before, because it works. On average, companies incur costs of $120,000 per phishing attack, but the damage can range well into the millions if the attackers successfully hook a whale.
Whaling attacks, in particular, are on the rise, putting sensitive data at risk and costing organizations billions of dollars across the globe. There was a 131% increase in whale phishing from Q4 of 2020 to Q1 of 2021, and that number has continued to rise since, with total phishing attempts up by 350% since 2020.
Not if, but when
As rates of whale phishing continue to rise, the question organizations face changes from “what happens if we fall for a phishing attack,” to “when?” However, this change in mindset isn’t simply pessimism—it’s a strategic shift in the way organizations approach security. Many people think only the technologically inept are susceptible to phishing attacks, but if whale phishing has shown us anything, it’s that people of all levels of technological savvy can be swindled.
When phishing outreach is personalized correctly, or employs a two-pronged approach where the threat actor impersonates an additional “legitimate” third party, even the most sophisticated employee or organization can be fooled. In fact, the fast pace and strict hierarchical structure of some organizations can play to the attacker’s advantage. Employees that have never spoken to executives are less likely to realize when someone is impersonating their executive team. Additionally, individuals accustomed to last-minute demands are less likely to think critically before obeying an attacker’s instructions.
Cyber criminals: 1, Enterprise: 0
One of the most famous examples of an effective real-world whale phishing scam occurred in 2015 when a 125-year old agricultural supply chain company wired over $17 million dollars to an offshore bank account in the name of business-as-usual.
When a financial controller was asked by someone impersonating the chief executive to wire money to complete the acquisition of a China-based company, he didn’t think twice. Why? The company really was in the process of acquiring China-based affiliates at that time, and the attacker had done adequate research to know about and speak to that ongoing project. Additionally, the attacker asked their victim not to discuss the acquisition outside of their email thread, saying, “This is very sensitive, so please only communicate with me through this email in order for us not to infringe SEC regulations.” To make a fairly believable play even more credible, the attacker was also able to impersonate the company’s outside legal team. It’s difficult not to feel empathy for the victim: a competent individual in the wrong place at the wrong time—and, following the wrong procedures. The famous scam serves as an outstanding lesson for the rest of the world: phishing happens – and, if we’re not extremely vigilant, it’s an extremely effective method of cyber crime.
You’re probably being phished, already
Have you received texts or emails from high ranking members of your organization that seemed suspicious? These messages may have included language designed to build credibility or establish a relationship with you. Some of the words used may insinuate that the executive needs help for a project that is highly “sensitive” or “urgent.” Every day, employees of all levels are being targeted with texts, emails and sometimes, even voicemails, as threat actors try to access data and capital. Here are a couple of phishing examples reported by Veza’s own team. Do these look familiar?
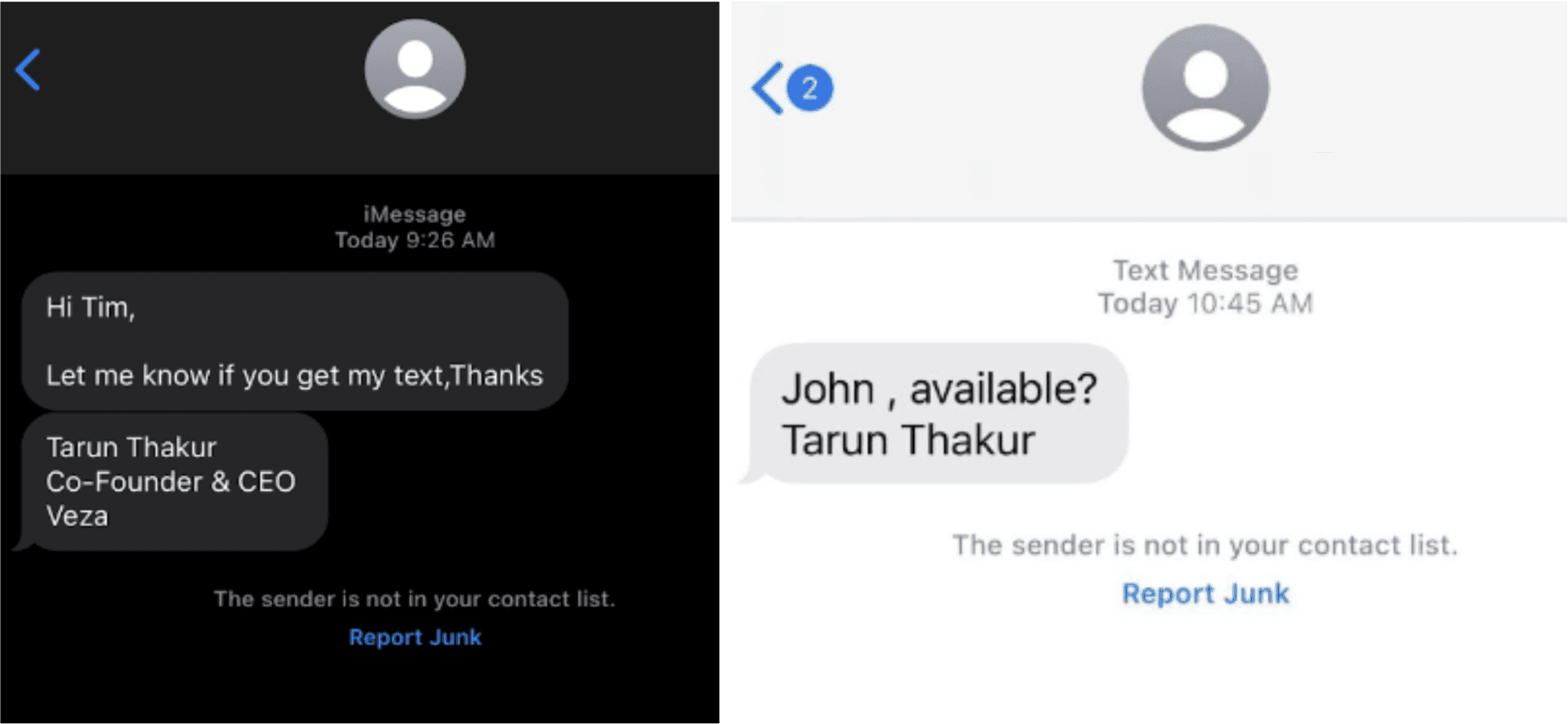
How to stay safe from phishing
Evolve security procedures
As employees are bombarded with text messages like the above, as well as more specific, personalized outreach, organizations are putting safety measures in place. Some enterprises have developed “panic” channels, for example, where employees can submit suspicious communication and quickly receive confirmation as to whether the activity is fraudulent or not.
Many businesses also require that employees practice other basic security measures to stay safe from both phishing attempts and other types of cyber threats including:
- Always using multi-factor authentication (MFA)
- Double checking suspicious or urgent requests via other channels including email, Slack message, or phone call
- Using unique, strong passwords for every site and service, and never reusing them
- Where possible, opting for new authentication technology that allows organizations to get rid of passwords altogether, in favor of passwordless or other phishing-resistant authentication
Most organizations also have implemented other security measures like using single-sign-on (SSO), conducting quarterly or annual permissions reviews, or requiring employees to participate in recurring training on how to identify phishing attacks and other cyber threats.
Instill a communicative culture
These procedures are excellent steps in the right direction, but ultimately an organization’s long-term security is most dependent on overhauling culture from the top-down. It is up to leadership to create, enforce and emulate a communicative and healthily skeptical culture. The safest teams encourage team members to ask questions and communicate without fear of criticism.
The employees most likely to be susceptible to whale phishing attempts are those who treat executive interactions like fire drills. Staff members that are under a lot of pressure, or who are used to jumping on new, high priority tasks at the drop of the hat, are less likely to suss out fraudulent outreach from threat actors.
One of the key ways organizations can save employees from this fate is through building relationships. High-level targets should make an effort to engage with employees through approved channels, and to instill validation policies for expensive or confidential requests when they legitimately arise. Most importantly, companies should reward employees for being vigilant. Similar to the expression, “there are no stupid questions,” organizations should implement “there are no stupid verifications.”
Plan to fail
Even with the best security processes in place, it is still very difficult to prevent social engineering. No matter what else your organization may be doing to defend itself, you should still plan for attackers to succeed in compromising key identities some of the time. For this reason, your efforts to prevent phishing need to be complemented by a plan to limit the damage that will result from a compromised identity.
Double down on least privilege
The best damage prevention measure you can exercise is taking a hard look at how well you are employing the principle of least privilege. Ask yourself: would whale phishing be as effective if there weren’t so many “whales”?
The targets of whale phishing are typically C-suite or other highly visible executives, but this observation is indicative of a flaw in most enterprises’ provisioning. Threat actors assume that high-level executives have the most privilege, and they often do—but, why?
The principle of least privilege requires that identities only have the permissions necessary to do their work. When was the last time your Chief Technology Officer actually needed to delete customer data from your data warehouse? Executives often only need visibility on company information to do their jobs effectively; they rely on teams to whom they can delegate operational activities. If permissions more closely mirrored team structure, your organization would be safer.
Audit your most visible team members and ask: what permissions do they really need? Can executives get the visibility they need without direct access to sensitive data? Consider creating dashboards in business intelligence (BI) tools like Looker, or using data warehouse features like Snowflake Views to gather the information needed for oversight, rather than giving direct access to sensitive data.
Taking a more strict approach at applying the principle of least privilege, especially at higher levels, will decrease the number of available targets for whale phishing attacks within your organization.
Save the whales: identify and protect whale identities with Veza
Veza is the authorization platform for data security that helps you answer the question of who can, and should, have what access to what data. Veza helps you to effectively enforce the principle of least privilege to reduce the potential damage of a phishing attack.
Understand the effective permissions of identities.
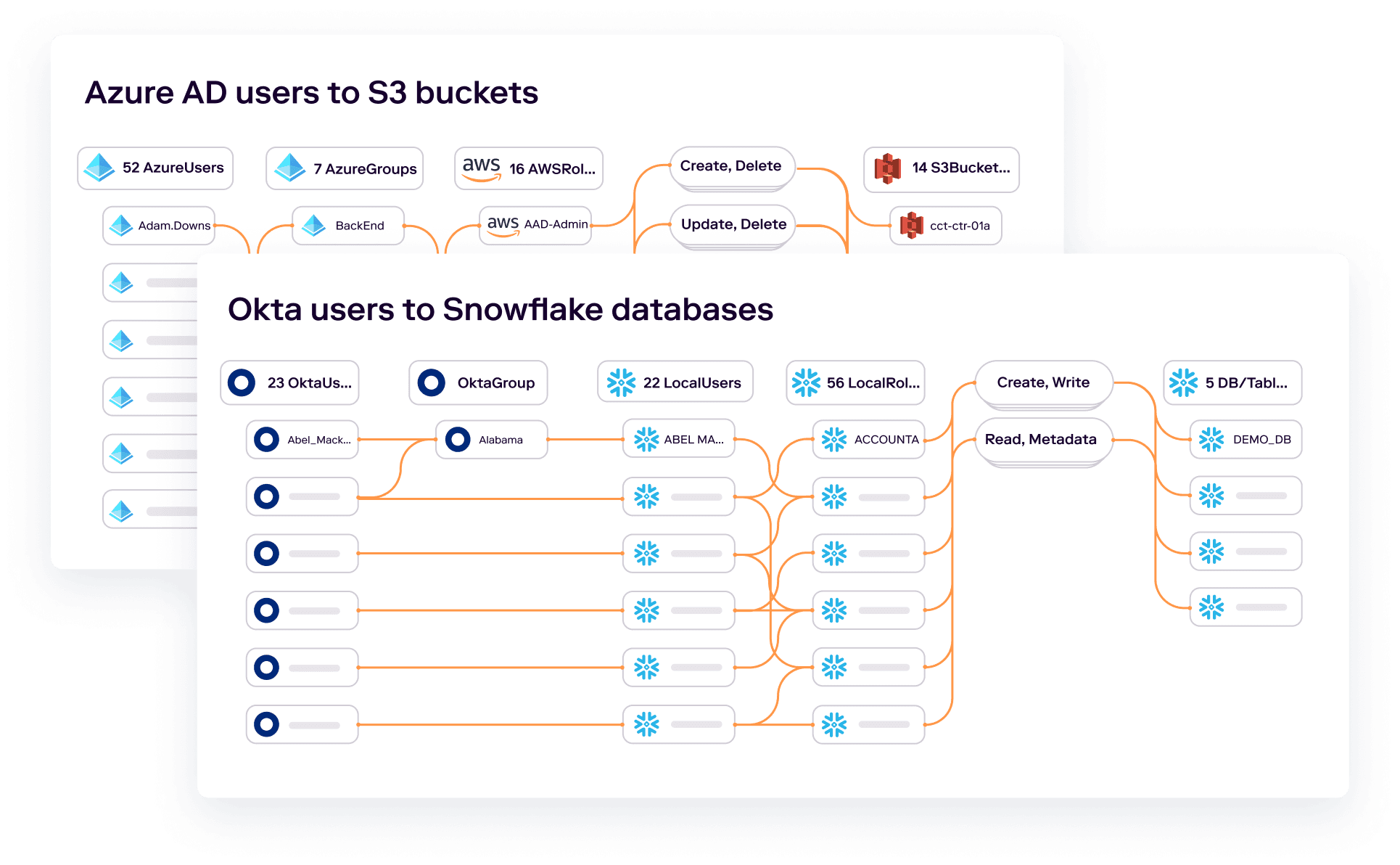
Veza integrates with your identity providers, cloud providers, apps, and data systems to capture authorization metadata. By connecting all these systems together, Veza can visualize and clearly help you understand direct identity-to-data relationships. We also standardize permissions across different systems into simple language: Create, Read, Update, and Delete. With Veza’s Authorization Graph, you can perform a deep dive into all the permissions of your highly visible employees and make sure your “whale” identities don’t have more privileges than they need.
Monitor continuously for access misconfigurations
Veza continually monitors the state of authorization across all your systems. You can create alerts to automate responses or remediation if key permissions change. For example, Veza can alert you to new users with delete privileges to crucial tables in your data warehouse, new users with full admin access to any system, or new users with write access to production on your source code repositories. This continuous compliance approach allows you to maintain least privilege over time and eliminate misconfigurations of highly-privileged identities before an attacker can exploit them.
Conduct Intelligent Access Reviews
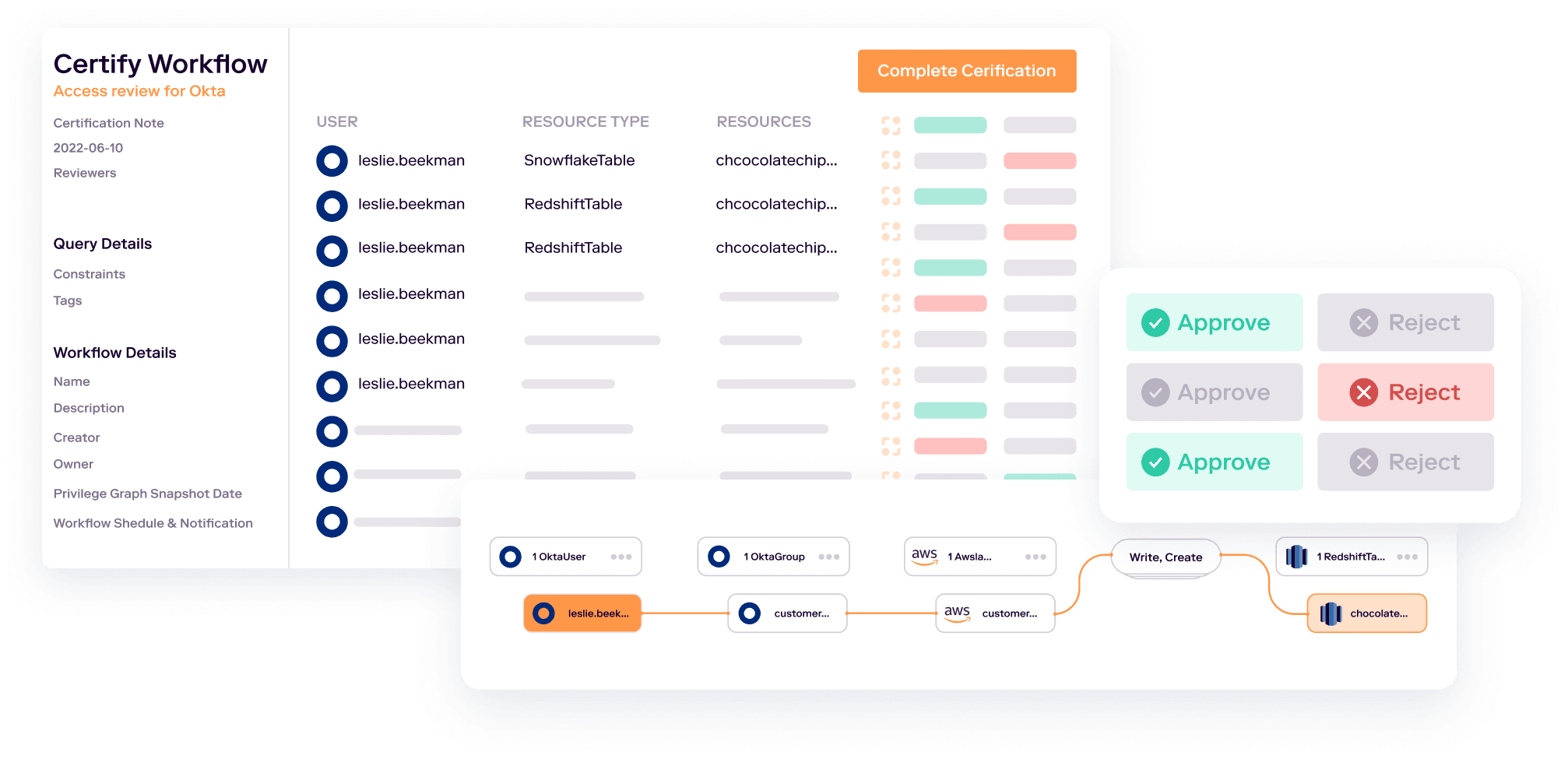
If your organization handles sensitive data, you probably already conduct some kind of regular access review, especially of highly-privileged users, like your executive team. But traditional access reviews often don’t help you to enforce least privilege.
By showing exactly what permissions an identity has, and how those permissions are granted, through groups, roles and the role-based access controls of each data system, Veza lets you conduct intelligent access reviews that can actually curb excess privilege.
Learn more
For more information on how your organization can leverage Veza, request a free trial or schedule a demo today.