Critical business discussions are increasingly taking place in online spaces, including Slack. This is true even if most of your employees work in the office. By removing friction from collaboration and decision-making, Slack can be a powerful productivity boost, but it also introduces new vulnerabilities and new challenges for security and governance teams. The informality and speed that makes Slack so valuable also makes it easy to forget with whom you’re talking at any given moment, and what is or is not appropriate to share.
For this reason, your company’s Slack workspace can be an attractive target for an attacker. All kinds of sensitive information is potentially available in Slack channels, including:
- Intellectual property and company strategy
- Confidential customer information
- Credentials to other systems and data
- Shared confidential files
Organizations should treat Slack as they would any other sensitive asset. We recommend you establish best practices for access, like multi-factor authentication (MFA) for all users, including guests. Create policies for what information is appropriate to share in Slack, and how. Most importantly, you need to be able to understand and control who has access to what information via Slack.
This post will share three tips for collaborating securely and effectively in Slack:
- Know who your admins are
- Know who your external users are, and what they can access
- Ensure that you have visibility and control of all accounts provisioned to Slack
We’ll also show you how integrating your Slack instance with Veza can help you achieve all three. To see a demo of Slack and Veza in action, check out the video at the end of this post.
1 – Know who your admins are#
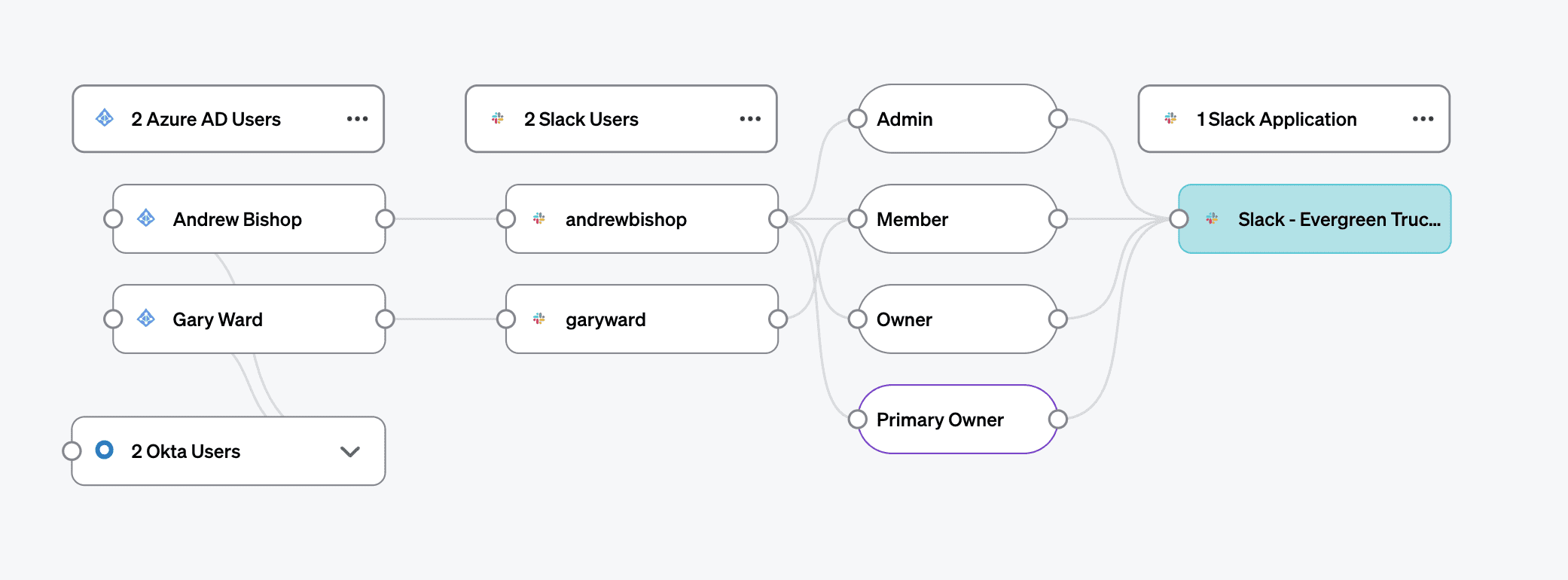
There are three highly-permissioned roles in relation to a Slack workspace: Workspace Admin, Workspace Owner, and Primary Owner. While only the Primary Owner can delete the workspace itself, all three roles can manage guests and add or delete public channels. In addition, depending on how your workspace is configured, Workspace Admins and Workspace Owners may be able to read and delete private channels. Don’t forget that deleted workspaces or channels in Slack are unrecoverable.
Any of these roles can also create more Workspace Admins, making it difficult to keep a lid on the total number of admins across a large organization.
How to stay safe#
While there can only be one Primary Owner, it’s important to keep track of who in your organization has the Workspace Admin and Workspace Owner roles. Implement an approval process for appointing new admins in accordance with the total number of Slack users in your organization.
The Veza way#
By integrating your Slack workspace with Veza’s authorization platform, you can:
- Search for all users with admin privileges in Slack and create a report to track trends in the number of admins
- Audit Slack permissions as part of your periodic access reviews for all employees
- Set up an automated Rule that creates a ticket in your ITSM (such as Service Now) if you exceed your ideal number of admins
Check out the video below to see how Veza helps you manage and control admin privileges in Slack.
2 – Know who your external users are, and what they can access#
The ability to collaborate frictionlessly with external users, like contractors, partners, and customers, as well as internal employees, is a key benefit of Slack. This frictionless communication, however, carries risks as well as benefits. Since Slack is predominantly an internal communication tool, many users assume that all users on Slack are internal. When sensitive information is discussed in public channels, it’s easy to forget that it may be seen by people outside the organization.
Individual contributors—especially contractors—may also use personal identities (like Gmail addresses) for Slack, making it difficult to know who they are, why they were originally given access, and if they still need to be around. For these reasons, the presence of guest users requires extra caution.
There are two types of guest users in Slack:
- Single-channel guests are limited to membership in a single Slack channel, usually one explicitly named and labeled as containing external users
- Multi-channel guests can be invited to more than one channel, and thus present a higher level of risk. Multi-channel guests can be invited to private channels by any channel member, and to public channels by any admin (another reason to keep a lid on the number of admins you allow)
Without looking closely at the membership list, it may not be obvious that a particular channel contains external users.
How to stay safe#
Wherever possible, and if your Slack plan allows it, consider using Shared Channels instead of inviting guest users. Shared channels help to limit the scope of access for external users, so they don’t end up in unexpected places.
When you need to invite guests, make it a policy to set up guests as single-channel guests wherever possible and apply a naming convention, like an #external- prefix to any channel that includes guests. Create a process to ensure guests are removed when access is no longer needed, for example, when their contract is complete.
If you do need to create multi-channel guests, make sure you are always aware of who they are, and record the business reason for granting multichannel access.
Finally, make sure that guests use similar security precautions to internal users, such as implementing multi-factor authentication.
The Veza way#
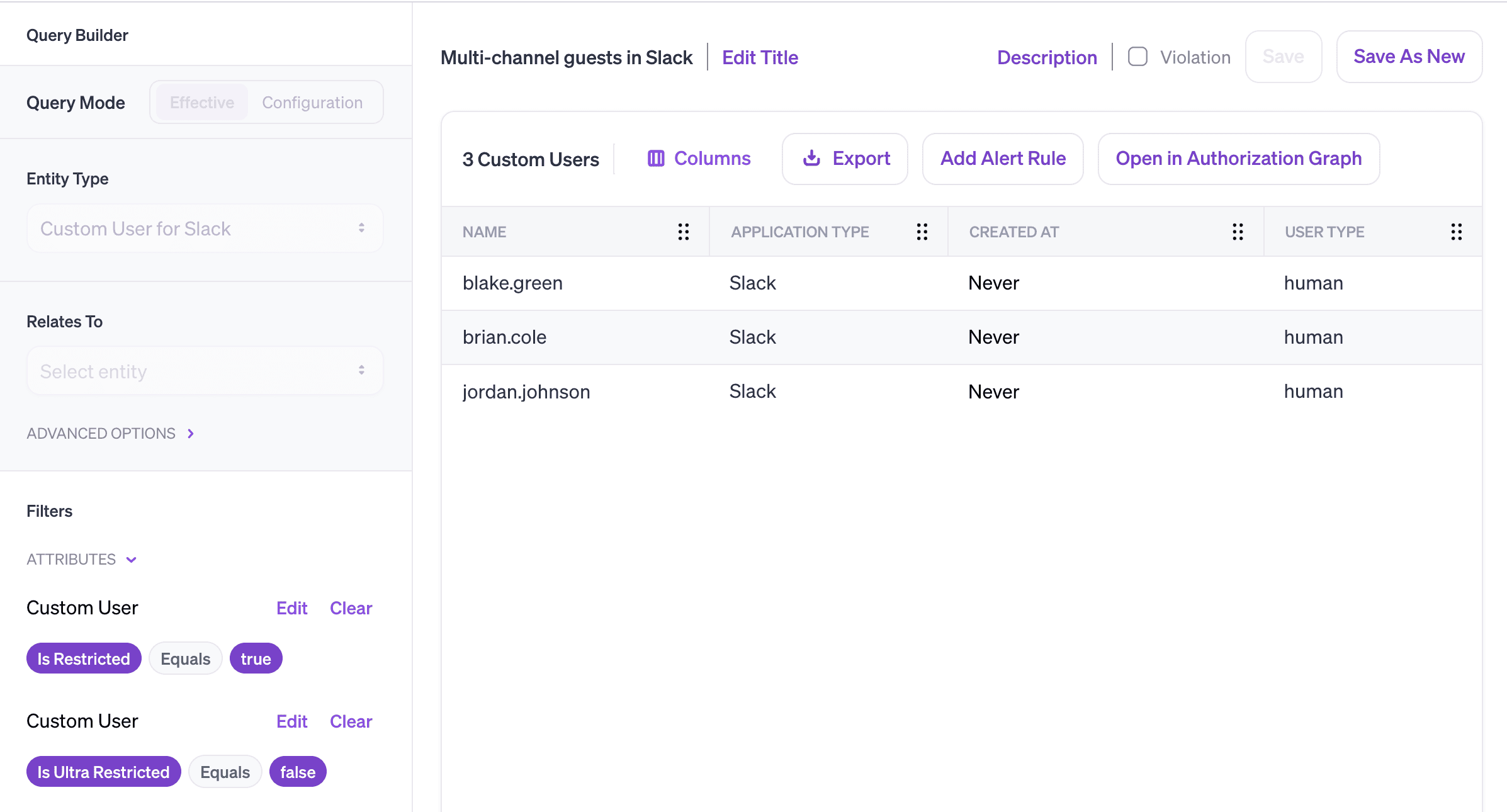
Veza can help you safely integrate guest users into your Slack instance:
- Identify all single- and multi-channel guest users in your workspace
- Automatically create a ticket in your ITSM any time a new multi-channel guest user is created. Your ops team can either remove multi-channel access, or record and approve the business need for multi-channel access, creating an audit trail
- Alert whenever any user—internal or external—is not protected by MFA
3 – Ensure that you have visibility and control of all accounts provisioned to Slack#
If you’re using an identity provider (IdP) like Okta or Azure AD to manage identities in your organization, it’s important to ensure that all access to Slack is provisioned and deprovisioned via your IdP, and not granted directly. Circumventing the approved provisioning process happens all the time. Without proper visibility and alerting, it can lead to vulnerabilities such as orphaned accounts and incomplete offboarding. For instance, if an employee leaves the company, you might delete their accounts in Okta, but leave their Slack access intact. You now have an ex-employee active in Slack. Not great!
How to stay safe#
Ensure that you have a means to track all users in Slack—both those provisioned by the approved process and any other process. Watch out for orphaned local Slack users and check that access to Slack is properly removed as part of your offboarding process.
The Veza way#
Veza ingests metadata from both your Slack instance, and your identity provider, so you can:
- Surface existing local users in Slack with no relationship to an account in your approved provisioning process
- Automate workflows to remediate any future Slack access that circumvents your approved provisioning process
Conclusion#
Slack can supercharge productivity by allowing for fast and frictionless collaboration with both internal and external collaborators. But that rapid pace and informal tone makes it easy to forget that your Slack workspace is a critical data store that holds all kinds of sensitive information. Safely managing collaboration in Slack requires granular visibility into the permissions of users and the ability to automate best practices so that they’re consistently followed.
With Veza and Slack, you can:
- Always know who your admins and external users are, and ensure that they’re correctly configured
- Constantly monitor for misconfigurations and best practice violations, like unnecessary multi-channel guests
- Create clear audit trails for security decisions through integrations with ITSM tools
To find out more about how Veza and Slack can work together, schedule a demo or sign up for a free trial.