Welcome to the Veza Voice, our monthly customer email where we share our latest and greatest product updates, tips and tricks, events and news.
This month’s newsletter includes:
- Enhanced Insights experience
- Path Summaries for Google Cloud
- Tips for tracking how users access SaaS apps via Okta
- Upcoming Veza events
-Mike B.
Product Updates
Enhanced Insights
We’ve rolled out a series of enhancements to Veza’s Insights to make them more relevant, more actionable, and more usable. These product improvements will help you identify and eliminate your top priority risks and misconfigurations.
Customizable Authorization Risk Dashboard
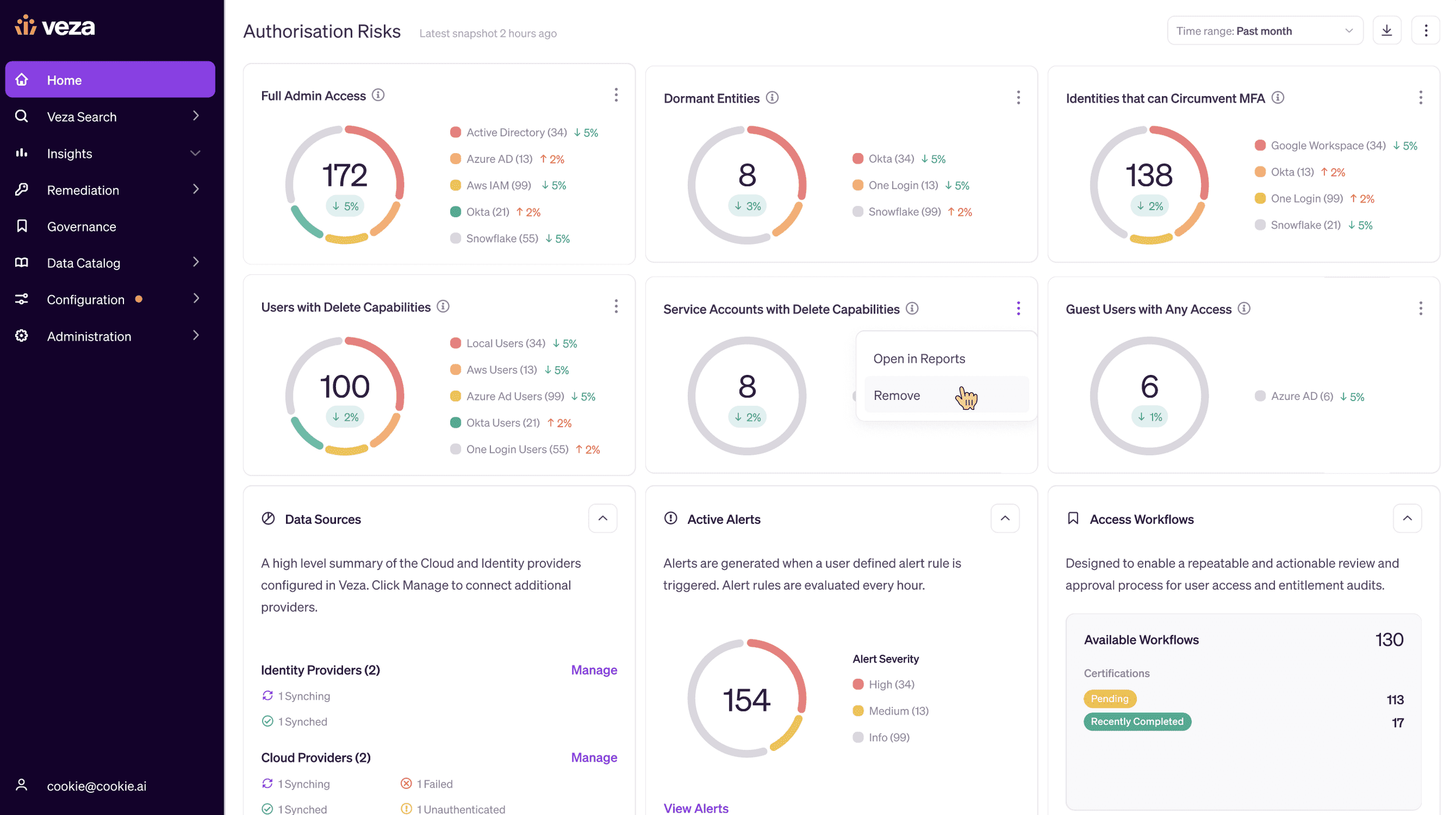
The Authorization Risk Dashboard on the main Veza dashboard is now completely customizable and each risk tile on the Dashboard maps directly to a report. You can remove default risk tiles that are less relevant for your organization, or turn any custom report into a risk tile. Each individual user can create their own custom top risks section of the Veza homepage to display at a glance your top priority risks.
Public and Private reports
Any user can now create private custom reports for their own use. Private reports can help to prevent overcrowding of your report library with specialized reports needed only by a few individuals. Report owners can publish their private reports to make them available to the entire organization. You can also clone any public report as a private copy to make edits or variations.
Improved custom report design
Admins can now edit Veza’s out-of-the-box reports. You can add filters or constraints to focus the reports on the resources you care about most. Meanwhile, custom reports can now be organized into sections to make them more readable. You can easily add, remove and reorder the sections of your report, and add or remove queries from any section.
Other improvements
- We’ve refined our out-of-the-box violations to prioritize 19 critical violations to reduce noise and allow you to focus on the highest priority issues.
- We’ve added new out-of-the-box reports for AWS, Google Cloud Platform, Snowflake, Okta, and more.
- From any report, you can now open up any query in the Authorization Graph, or the Query Builder with a single click, or view alerts for any query.
Path Summaries for Google Cloud
Veza helps you answer the question of who has what access to what data. However, to enforce best practices for access and entitlement management, it also matters how an identity has the access it has. We’ve released improvements to our Google Cloud integration to give you visibility into how identities gain access to Projects in Google Cloud.
Access reviews in Google Cloud now include a configurable Path Summary column to show how an identity comes to have access to a Project.
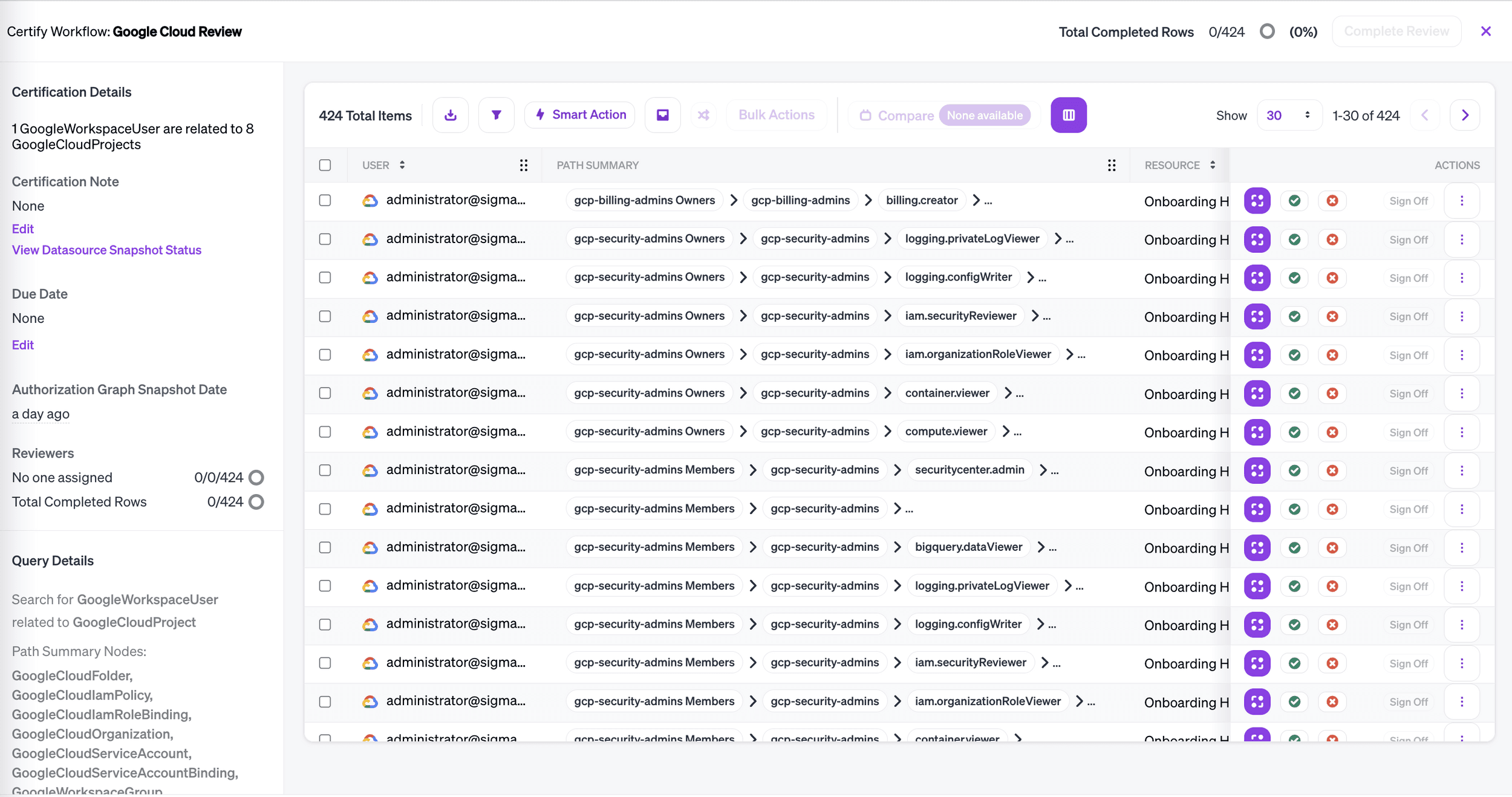
Use path summaries to scope your access reviews, and add constraints to identify misconfigurations.
Consolidate paths to access
The complexity of Google IAM means that there are multiple possible paths to the same access. Using Path Summaries, you can consolidate access into a single pathway that reflects your policy. For example, you can identify and remediate access for users who directly assume a role, rather than going through the appropriate group, or permissions granted directly to users, rather than through role. Additionally, you are able to form your workflows to include one, multiple or all possible paths to access: through groups and roles, or without them.
Distinguish between direct and inherited policies
The Path Summary column also covers organizations, folders, and projects. This allows you to know if a policy has been applied directly to a project, or if the policy is inherited from a folder or organization, and create Workflows that include only direct or only inherited policies.
Identify group membership types
Veza now shows the type of membership an identity has in a group, whether they are an owner, manager or direct member. This allows you to make sure your groups have an appropriate number of managers. You can also identify all group owners and managers for internal communications, and create Workflows that include only the types of group membership that you are interested in.
Veza Integrations
As we continue to expand the reach of Veza’s Authorization graph, our team is always easing new integrations. Newest additions include:
- Veza for Bitbucket Server
- Veza for Jira Server
- Veza for Box
- Veza for ServiceNow
Reach out to your customer service manager to get started.
Veza releases new features every week. Bookmark our release notes page to see the latest and greatest.
Tips and tricks: Track how users access SaaS apps
A cornerstone of Veza has always been to give our customers a complete view of who has access to what. A very important aspect of valuable visibility is not just who can access what, but how do they get that access. For February’s tips and tricks, we want to focus on a capability that many customers take advantage of: visualization of which identity provider (IdP) users have applications assigned directly to them vs. those who inherit access through group membership.
IdPs such as Okta and Azure AD recommend the best practice of adding users to groups and assigning applications to groups, not to individual users. This is because users’ roles within an enterprise can change over time, and they can be removed from groups when a role changes vs. hunting down every application that is assigned to them that they no longer need and removing that.
With Veza’s Query Builder, you can quickly and easily understand which users have been assigned to apps directly vs. those who have access to an app by virtue of group membership. Let’s use Okta as an example IdP. To see this feature in action:
- Query for a list of Okta Users and their relationships to Okta Apps.
- Click the “Advanced Options” menu, and click the “Exclude Entity Types” button. This will allow you to exclude results that have any of the selected entity types in their path.
- Check the Okta Groups option to filter your list down to just which Okta Users have Okta Apps assigned to them directly vs. based on group membership.
To see how it works, watch this short video:
Events
Meet the Veza team at these upcoming events:
- Chicago: Join us March 2nd for an exclusive dinner with founder and CEO Tarun Thakur at Gibsons Italia.
- SecureWorld East, March 2nd, in Charlotte, NC.
- Visit us at booth 635
- Veza Strategist Rich Dandliker, will be part of the “I Can See Clearly Now, the Threats Are Gone: Threat Intelligence: The State of Infosec Today” Panel at 1:15pm ET.
- Gartner IAM, March 20th-23rd, in Grapevine, Texas. Below is a preview of Veza’s activities during the conference; more details to come soon:
- Veza is a Premier Sponsor, Gartner IAM.
- Visit us at booth #117 in the exhibitor hall to hear the latest product updates and real-world customer stories.
- Watch Veza experts present on the Gartner stage.
- Network with Veza founders and executives during one of our intimate dinner events on 3/20. RSVP here.
- RSA, April 24-27 in San Francisco. We will be hosting a dinner on April 25th at The Monarch – watch for more details!
Email events@veza.com for more details.
News
Veza announced the launch of our Github integration to stop IP theft and enforce access policies on source repositories.