As organizations gain a deeper understanding of the full value of their data, they often want to increase utilization and sharing of that data. Shifting data stores to the cloud offers the promise of making data more available, so remote teams can extract, intelligently parse, and share information across data stores everywhere. But traditional infrastructure-centric security solutions do not adequately secure multi-cloud data, leaving organizations struggling with increased friction, a heightened risk of security breaches and compliance headaches.
To fully leverage their data without putting their organization at risk using a zero trust approach, teams need to recognize that data authorization needs to become a fundamental pillar of their overall security strategy. They need to align their security approach with the priorities of the business: the “crown jewels” are clearly the data, such as customer information, financial transaction records, and source code. Infrastructure, identities, systems, and apps are important to secure as well because they touch the data. And teams need to evolve from siloed solutions to comprehensive data security platforms. The time to make the shift is now, as leveraging data is becoming ever more critical to business acceleration and success.
60% of the Fortune 1000 employ Chief Data Officers—up from only 12% in 2012—and these companies substantially outperform their peers in McKinsey’s growth and profitability studies.
McKinsey
The Data Sharing Imperative
Business leaders no longer need to be persuaded that investing in initiatives to modernize how they use and store data will pay off. Fully 96% of companies responding to the NewVantage Partners 2021 State of Corporate Data Initiatives survey report that implementing modern cloud data architectures has resulted in improved business performance. Just five years ago, that figure was only 48.4%.
A key marker of success for these solutions is data sharing. Based on this year’s Gartner Chief Data Officer Survey, those who successfully accelerated their data sharing efforts reported that they were 1.7 times more effective at showing verifiable value to their stakeholders. Gartner is forecasting that by 2023, organizations that continue to prioritize data sharing will outperform their peers on most business measures.
But for companies still focusing on infrastructure-centric security, accelerating the practice of data sharing poses serious challenges. Providing frictionless access to cloud-based stores of personally identifiable information (PII) and other highly sensitive data, while relying on incomplete and legacy data security solutions to protect that data, dramatically increases the risk of security and compliance breaches. It’s a nontrivial roadblock for many organizations: Nearly half of those participating in the HashiCorp State of Cloud Strategy Security Survey reported that security is still a top inhibitor to cloud migration.
The Gap in Data Security
Many organizations migrating to the cloud have implemented infrastructure-centric security tools like Cloud Security Posture Management, and most provide single sign-on and multi-factor authentication to secure employee access to infrastructure and applications. Yet the available options, to date, for effective cloud data security solutions have been limited.
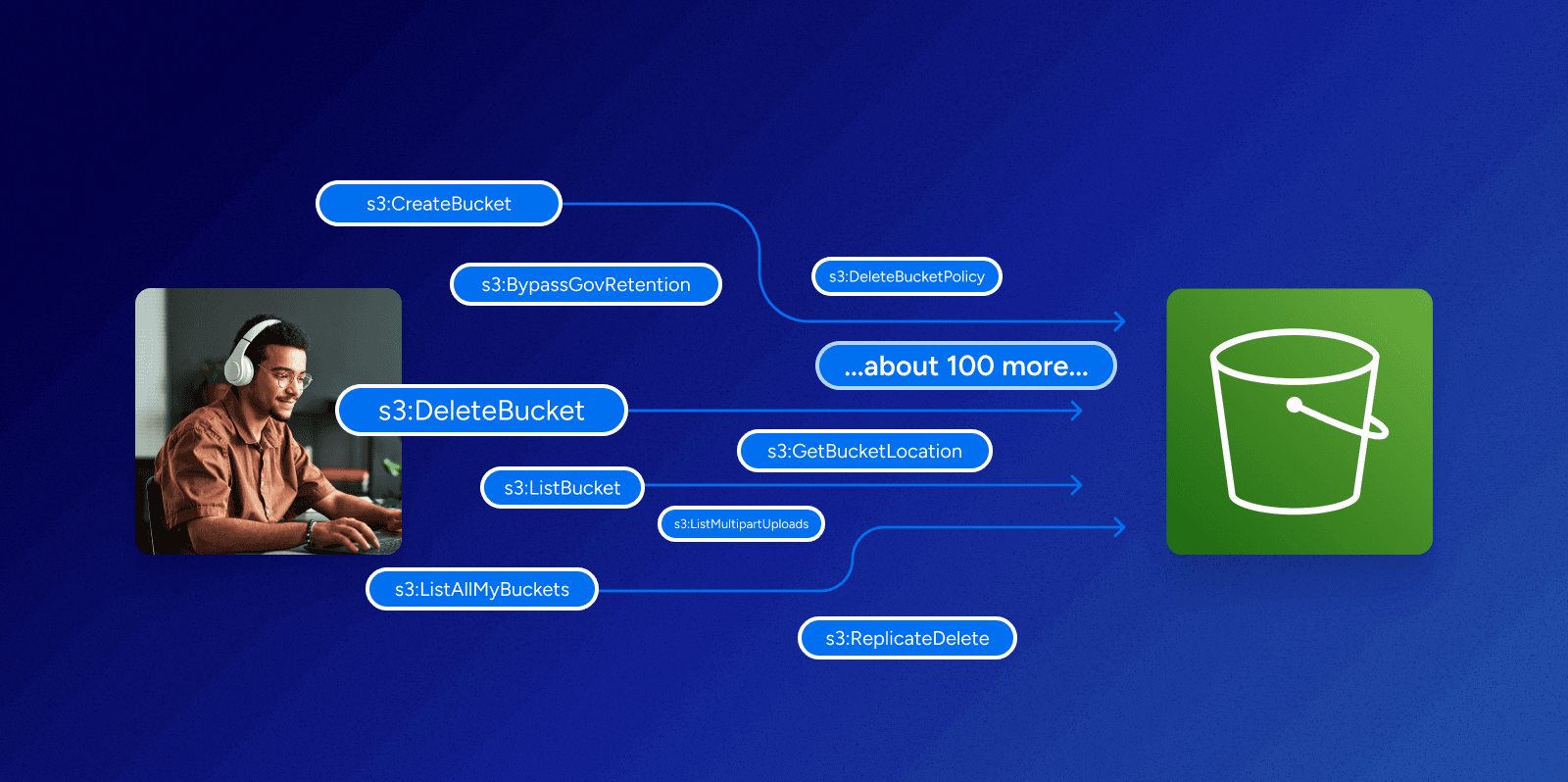
Why aren’t infrastructure-centric security solutions enough to cover cloud data? Because in focusing on the infrastructure, they are limited to the controls and information you have available for that infrastructure. The nature of the data authorization problem cuts across many different information silos that are owned by different teams.Current data governance, data catalog, data discovery and authentication tools cannot adequately secure modern, cloud-native data systems including cloud-based data lakes because those tools don’t go deep enough to truly understand and manage authorization or aren’t built for modern cloud systems.. Likewise, data loss prevention provides a layer of protection for the occasional instance of misplaced content, but those solutions don’t safeguard the massive amounts of valuable data that can be exposed through over-permissioning.
Here are just a few examples of questions that traditional data security solutions can’t answer:
- How many of my Okta users have delete permissions on Amazon Redshift?
- How can I map my Azure AD users to my Snowflake tables through Google Looker and a service account?
- Who has the ability to encrypt data in our DynamoDB tables and could be targets for ransomware attacks?
To fully leverage the power of data, enterprises need to provide permissions for those who need it quickly and without friction. It’s not just a nice-to-have; it’s the critical common denominator that makes modern organizations run. But you can’t simply cross your fingers and hope that Data Owners are always making informed, intelligent decisions about who gets access when they simply don’t have the tools to make those decisions.Until you have a unified, comprehensive data security solution, your data authorization can either be safe or frictionless—but not both.
Addressing the Gap
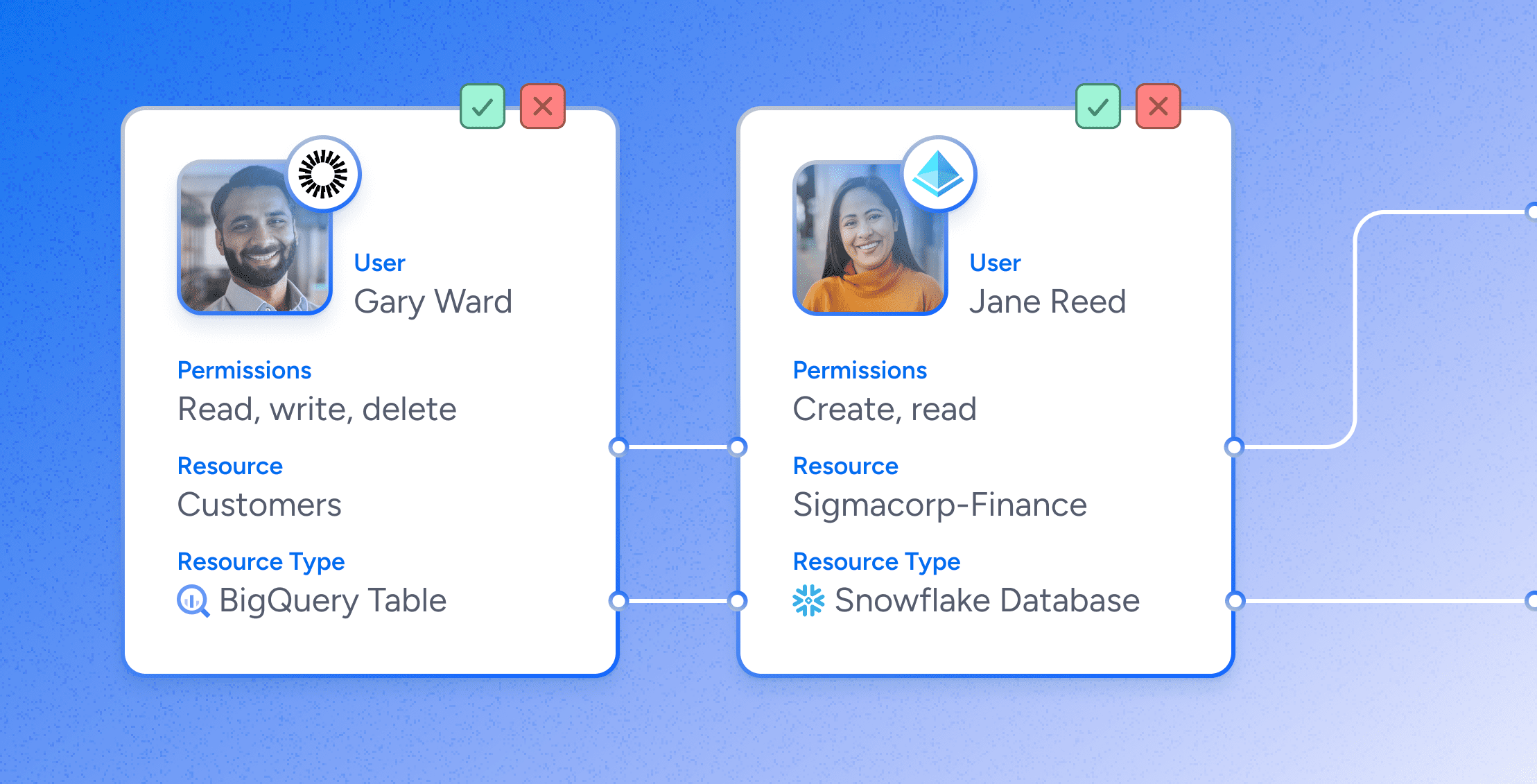
The language of authorization—defining and linking users, groups, roles, policies, objects, and allowed actions for users—is natively specific for each systems. It’s different from one system to another: for example, an authorization policy for Microsoft SQL Server isn’t the same as AWS Redshift.
That’s where Veza comes in.
Our solution extracts the authorizations of different end systems, then parses and correlates this system-specific authorization metadata with metadata from identity and access management systems. We make the results available via a powerful search interface coupled with enterprise features including rules, alerts, violations, insights into risky changes, and workflows to help the right people review the access permissions . Our comprehensive data security platform lets customers search, visualize and remediate authorization controls, so they can confidently determine who can take what action on what data, at scale, consistently across systems. Moreover, we’ve translated the permissions into regular language so that ordinary business users can understand what it all means, and what they are actually approving in the entitlement review process.
Conclusion
Veza has reinvented data security for the multi-cloud era with a comprehensive data security platform built on the power of authorization. With Veza in place, organizations can confidently enable the cloud-data-sharing they need to unlock growth, while simultaneously reducing the risk of data breaches and compliance nightmares. Put an end to the “security theater” of your current access review processes, and enable your teams to spend their time securing your data instead of just going through the motions of compliance. For more on how Veza can help your organization move beyond the limits of infrastructure-centric security and start fully leveraging its data, sign up for a free trial of our product here.