When Kojima Industries, a Tier1 supplier of plastic parts, was crippled by a ransomware attack, Toyota was forced to temporarily shut down manufacturing across Japan earlier this spring. Like many suppliers in and out of the auto manufacturing vertical, Kojima enjoyed a level of digital access to their client’s ecosystem. As the ransomware attack unfolded, and it became clear Kojima would have to pause production of critical parts at its plants, Toyota itself was forced to shut down operations for 24 hours.
One day may not sound like much, but that translated to a 13,000-vehicle output loss.
Cloud interconnectivity provides game-changing business advantages, but it presents a host of new security challenges. Even if your company has a strong zero trust security stance, if you’re permitting third-party access your safety depends in part on the resilience and the security practices of your least-secure partner or supplier. So it’s worth taking a closer look at what happened to Toyota, and what can be done to harden defenses against supply chain attacks like this one.
There were 623.3 million ransomware attacks in 2021 worldwide—more than double the number that occurred in 2020.
https://www.techradar.com/news/ransomware-attacks-saw-a-huge-rise-in-2021
First, Some Context: The Rise in Ransomware
Ransomware is a particularly devastating form of malware. Malicious actors that find a way into your network first encrypt files, to render them unusable, then demand money in exchange for decrypting them again—essentially holding them hostage until you pay up. And backing up your data isn’t sufficient to keep these threat actors at bay. In a diabolical, but already common twist, they threaten to leak or sell your company data or authentication information, promising a catastrophic loss of revenue and reputation. Ransomware attacks are swift, punishing, profitable…and increasing at an alarming rate.
Forward-thinking companies have accelerated their digital transformation over the past few years, increasing their reliance on remote access to cloud environments. For all the obvious advantages, this shift also expands an organization’s attack surface quite dramatically, providing more and more opportunities for sophisticated ransomware teams to infiltrate your ecosystems. In the rush to cloud, an enterprise’s existing IT infrastructure almost always fails to properly protect this expanded, complex digital landscape, where millions of human and non-human identities require anytime, anywhere access to enterprise assets.
Cybercriminals are only too happy to exploit cloud vulnerabilities wherever they find them, and one such vulnerability is supply chains, where a less secure supplier or partner who has privileged access into a protected network can potentially act as a Trojan horse by which the attackers can infiltrate the better-protected organization.
Ransomware payments reached over $400 million globally in 2020 and topped $81 million in the first quarter of 2021
The White House Briefing Room || https://www.whitehouse.gov/briefing-room/statements-releases/2021/10/13/fact-sheet-ongoing-public-u-s-efforts-to-counter-ransomware/
The Cyberattack: What Happened to Kojima
Awareness of the cyberattack began when Kojima, which provides plastic parts and electronic components to Toyota, discovered an error at one of its file servers. After rebooting the server, Kojima admins confirmed it had been infected with a virus, accompanied by a threatening message written in English. The system failure crippled Kojima’s operations and halted its shipping capabilities, forcing Toyota to pause 128 production lines across 14 factories.
Toyota is no stranger to supply chain challenges. A typical automobile has around 30,000 parts, and storing and managing spare parts can be expensive for manufacturers. Toyota was an early proponent of the “lean principle” of manufacturing, giving up the expensive comfort of stockpiling spare parts and supplies in favor of an organized, efficient, just-in-time approach, saving significant money but increasing vulnerability to supplier shortfalls. After the March 2011 earthquake and tsunami in Japan caused a widespread shortage of parts that shut down production for weeks, Toyota developed a massive, comprehensive database of supplier information, detailing vulnerabilities and parts information across over 650,000 supplier sites.
Ransomware adds another layer of complexity to supply chain issues. If a supplier can’t provide necessary parts, it could disrupt your production. But if a supplier is compromised in a ransomware incident, and they have access to your network, their problems can quickly become your problems. Just after President Biden’s announcement this spring that the United States would issue new sanctions on Russian banks and elites, a senior FBI cyber official warned businesses and local governments that the moves would increase the potential for ransomware attacks. The global supply chain is already quite strained, and the potential for devastating supply chain ransomware attacks has never been higher.
Zero Trust: Staying Efficient while Minimizing Exposure
The ransomware attack that affected Toyota is a frightening reminder that ransomware can very quickly exacerbate supply chain issues. Most large-scale enterprises, like Toyota, grant partners and suppliers some kind of access to their networks, running the risk of inheriting security vulnerabilities as well as production challenges.
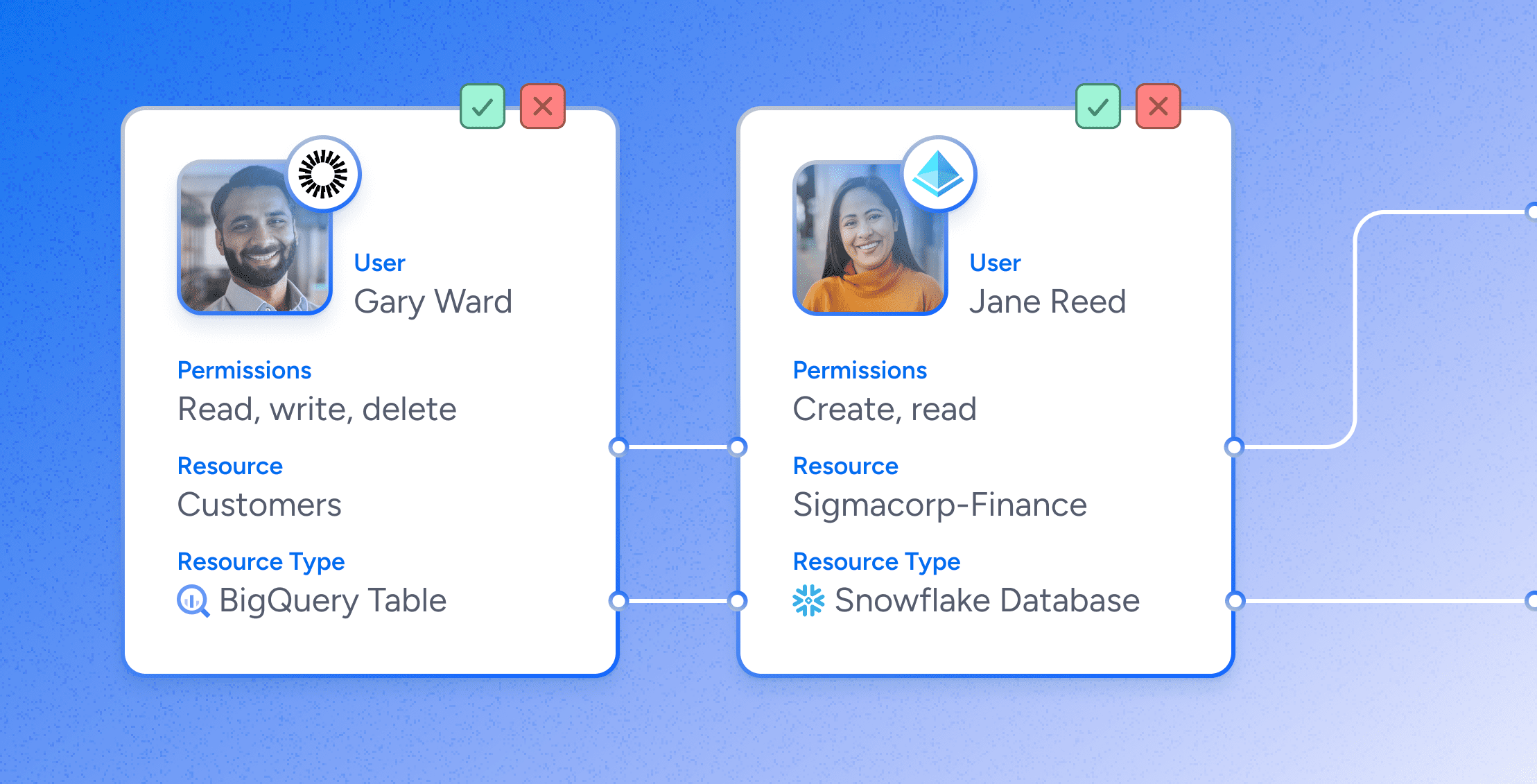
There may be no good way to eliminate the threat of ransomware completely, but there are powerful tools available to limit the threat. Suppliers and partners may need access to certain apps, data, and workspaces, for example, but they don’t need blanket, VPN-style access to your network. With a thoughtful and careful authorization structure, third parties can access the specific resources they need without permitting lateral movement across the system that could put the enterprise at risk. An enforceable zero trust security posture lets organizations protect users and resources from threat actors without inhibiting normal productivity.
Minimizing Supply-Chain Attack Risks with Veza
Veza’s authorization platform for data gives organizations the deep visibility they need to understand the true state of authorization across the board. With Veza, security and IT teams can understand, manage and control authorization for every enterprise identity (humans, service accounts) and any enterprise resource (databases, applications, cloud services).
Global manufacturers can’t manage the security posture of every company in their supply chains: Toyota alone reportedly works with 60,000 different suppliers. But Veza’s single source of truth for authorization across all enterprise data systems gives organizations the insights they need to enforce zero trust and least privilege principles, and keep a ransomware attack in their supply chain from spreading to their own systems.
The need for solid ransomware protection grows more urgent every day, but Veza gives network security professionals the tools to thwart bad actors and prevent crippling cyberattacks that threaten our strained supply chains. For more information, see Modernize Data Security to Protect Against Ransomware