Picture yourself waiting in the security line at the airport. The line moves slowly, because specially trained officers have to stop every would-be passenger, and validate their identity based on physical proofs: typically a driver’s license or passport. They compare your face to the face on your documents, and because you are who you say you are, you can now pass through the security checkpoint. Mission accomplished!
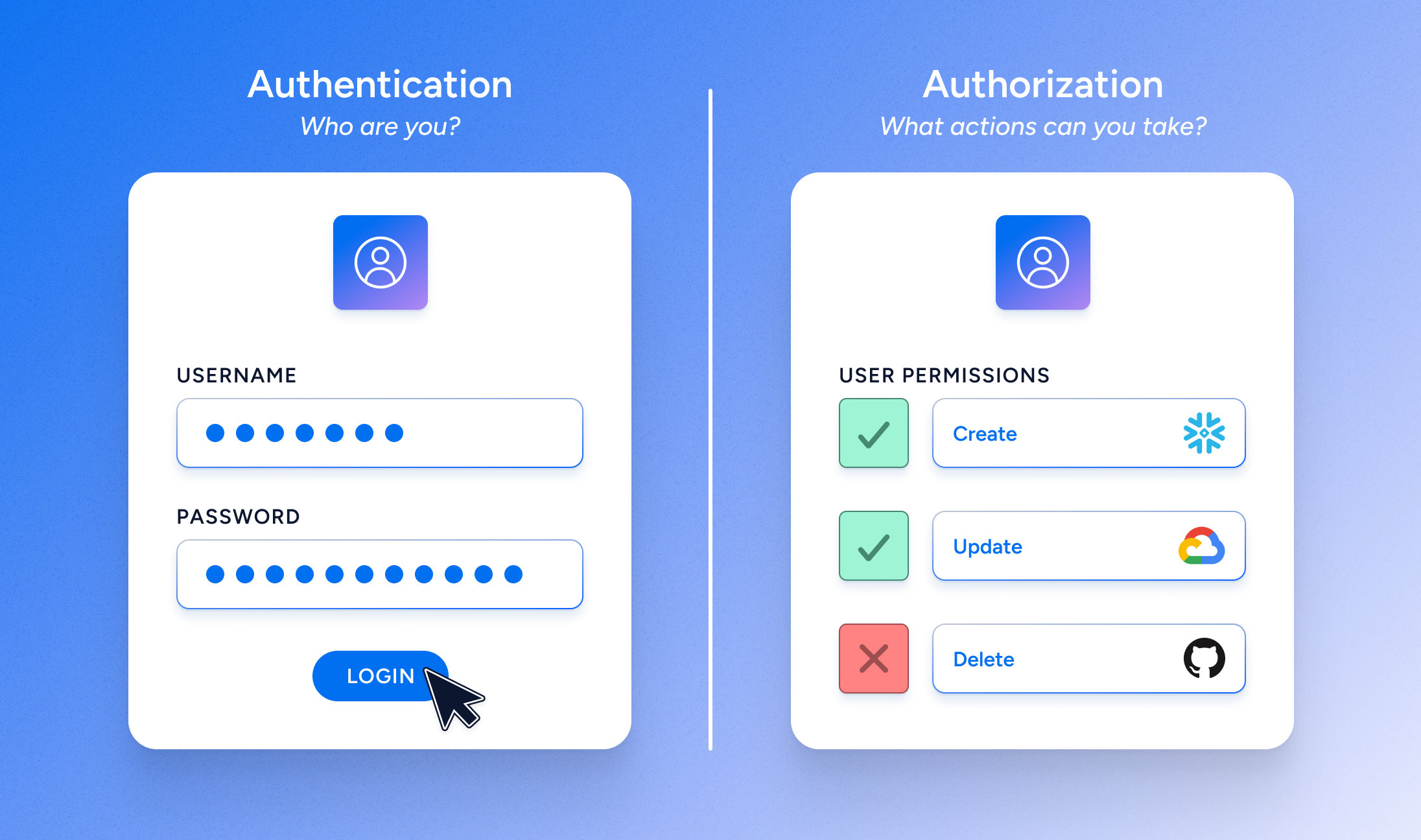
This is authentication. But your journey has only begun.
After all, you can’t just hop on any plane, now, and sit in any seat. Your ticket only allows you on a certain flight, at a certain time, that travels a specific route. Your next step is to find the specific gate guarding the one plane in the airport that your ticket actually permits you to board. And as you step onto the plane, your actions are restricted yet again. You can’t just sit in one of those big comfy first class seats, for example, and you certainly can’t go into the cockpit and control the aircraft. Your designated seat is 37B.
This is authorization—the specific action or actions that you’re permitted to take after successfully authenticating. And if authorization sounds more complicated than authentication, that’s only because it is.
Authentication and Authorization in the Workplace
In a modern, cloud-first workplace, authentication is a necessary first step in security, making sure that identities like employees, partners, and contractors can safely gain access to company systems. Once an identity has been authenticated, authorization takes over, dictating exactly how those authenticated users can and can’t interact with company resources and data once they’re inside the network.
After all, offshore contractors clearly shouldn’t have the same level of permissions as your IT administrators. But should they be able to create new files in a shared folder, or view potentially relevant, but proprietary, data? Should they be able to modify or delete that data? Fine-grained authorization offers the promise of gaining real control over access to all company resources, without impeding your workforce from doing their jobs. But it’s not an easy challenge to solve.
An authentication evolution has taken place over the past decade, and stronger passwords, multi-factor authentication, password-less validation, and biometrics are nearly universal now. We’ve come a long way in improving enterprise authentication, spearheaded by cloud identity solutions from Okta and Microsoft. Now it’s time for the authorization revolution to begin.
And the stakes couldn’t be higher. Every year, another round of high-profile breaches and data leaks prove yet again that an organization’s data is its most valuable asset, and a prime target for threat actors.
Strong Authorization vs User Provisioning
So what does a necessary authorization system look like? Ideally, to support the least privilege principle, permissions would be fine-tuned to specify the user, the specific asset, the actions permitted, and a limited, project-based timeframe. (When authorization is open-ended, “orphaned” identities can retain permissions indefinitely, making them prime targets for opportunistic credential thieves.) Strong authorization can be fine-tuned in this way to supply least privilege access to different groups and resources without restraining productivity.
Authorization to data can also be restricted based on the sensitivity of a data store, or data type, or granted to specific roles within a project group. Permitted actions can be limited as well, with some users restricted to read-only access while their managers are granted full permissions to Create, Read, Update, or Delete that content (CRUD).
Clearly, authorization needs can vary widely across roles, projects, resources, and time, which is why there isn’t a “universal authorization system” equivalent to SSO for authentication. However, because SSO typically does not take authorization-based access into account at the time of login, attempting to achieve fine-grained authorization through SSO will result in over-privileged access. Authorization is contextual in nature, and that context is the key in maintaining least privilege. Identity providers recognize the complexity of the authorization challenge, and many will put forward a user provisioning product as their solution. This can work well for birthright apps, and saves IT time in creating new accounts in every target system. But it’s not a failsafe solution for authorization for many reasons, including the following:
- User provisioning doesn’t immediately account for managing changes and ad-hoc requests from employees for new access.
- If changes are made directly in an application, bypassing the provisioning structure, user provisioning can fail to function properly within that app.
- User provisioning can’t automate some authorization functions that unburden IT and decrease risk (for example, ensuring that a person who transfers out of a department instantly and automatically loses access to the department’s databases).
- User provisioning doesn’t work for systems like AWS, that base authorization on roles rather than managing users directly.
But the biggest downside of user provisioning as a wholesale authorization solution is that it doesn’t allow for a consistent view of permissions across enterprise systems. Authorization rules can differ from system to system, and your teams can’t intelligently manage authorization everywhere in real-time without actionable insights founded in comprehensive visibility.
Today’s cloud-first companies need new tools to understand and manage enterprise access and governance at a finer level of detail than ever before, so they can demonstrate to regulators and customers that they are well-equipped to protect sensitive data, guard against leaks, and share information responsibly. And there’s only one data security platform born in the cloud and purpose-built to fully leverage the potential of strong authorization: Veza.
Veza: The Data Security Platform Built on the Power of Authorization
We firmly believe that authorization is the truest form of identity. So, we built a comprehensive solution to support the strong authorization today’s organizations need in order to manage key security initiatives across least privilege, data access governance, entitlement management, and more
We provide our clients with deep, detailed visibility into how all their identities are currently related to the enterprise’s apps, cloud permission systems, infrastructure, and data systems. This comprehensive, granular permissions map doesn’t simply tell you how your cloud infrastructure is configured, and it goes far beyond users, groups and roles. Rather, it clarifies the often obscure “authorization truth” across all systems, regardless of how the authorization was obtained. With Veza, organizations can confidently answer who can and should take what action, on what data. Our platform understands the complexity of permission structures across key enterprise technologies, normalizes those permission structures, and present all identity-to-data relationships in easy-to-understand business language of CRUD (Create, Read, Update Delete).
With Veza in place, you’ll finally be able to centrally understand, manage and control who can and should take what action on what data, and enforce the fine-grained permissions that keep your enterprise safe and running smoothly.
Veza integrates easily with the tools you already have, getting you up and running quickly. Your teams gain end-to-end visibility into data access across your ecosystem, from identity providers to cloud permissions systems to infrastructure to apps and data stores. And your enterprise will be able to confidently automate authorization rules: easing the burden of manual provisioning, helping maintain continuous compliance, and protecting the enterprise from today’s modern, evolving security threats.
The Foundation for Modern Security: Zero Trust
If the rules around data access are too restrictive, they can seriously impede workforce productivity. On the other hand, if you grant authenticated identities overly broad access or permissions across your network, then a single compromised identity can put all your enterprise assets at risk.
Granting users access only to the specific resources they need to perform their jobs—and no more—is known as the Principle of Least Privilege, and it’s a powerful way to limit the ability of a successful credential thief to move laterally and compromise other parts of your network. But to get there, you need to shift to a zero trust security posture, which provides the necessary foundation to safely automate fine-grained access permissions for authenticated identities.
More and more organizations are moving beyond the limitations of VPNs to adopt the Zero Trust security model, in which each access request is re-evaluated each and every time, no matter who’s asking. Zero Trust enables a critical shift in security posture. Instead of acting as a central access point for employees to gain unfettered entrance to your network—a threat actor’s dream scenario—you instead bring authentication and authorization to the forefront of every system.
At Veza, we think the best statement of the vision behind Zero Trust came back in 2014, in Google’s BeyondCorp research paper. “As companies adopt mobile and cloud technologies, the perimeter is becoming increasingly difficult to enforce,” the company wrote. But with a Zero Trust security posture: “All access to enterprise resources is fully authenticated, fully authorized, and fully encrypted based upon device state and user credentials. We can enforce fine-grained access to different parts of enterprise resources.”
Authorization and permissions are much more complex than authentication, and weak or improper authorization procedures can quickly lead to compliance violations, leaks of personally identifiable information, data breaches, and other disastrous outcomes. But with the right tools and systems in place, you can centrally control data access permissions, even at scale.