Next-Gen IGA
Veza reinvents access reviews and certifications with automation and access intelligence, to help managers make informed decisions.
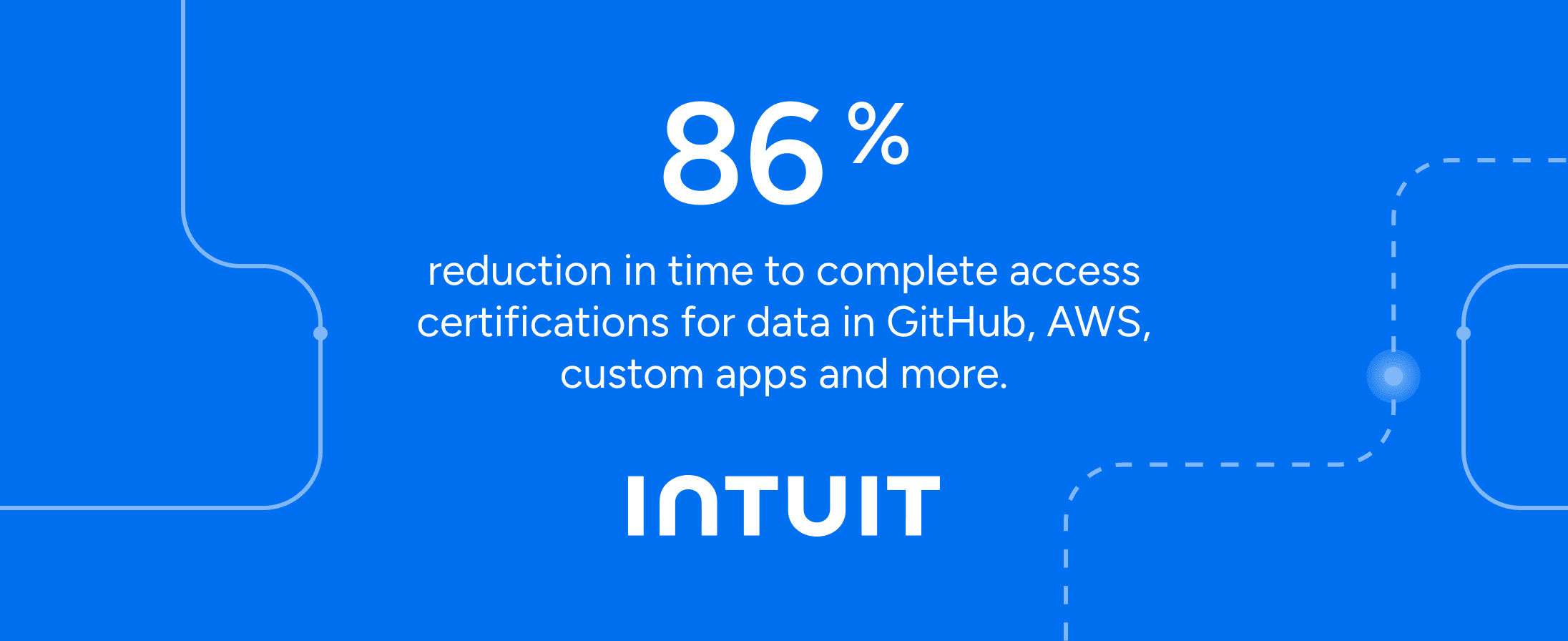
7x faster than manual reviews
For all your identity security teams
Identity & Access Management (IAM)
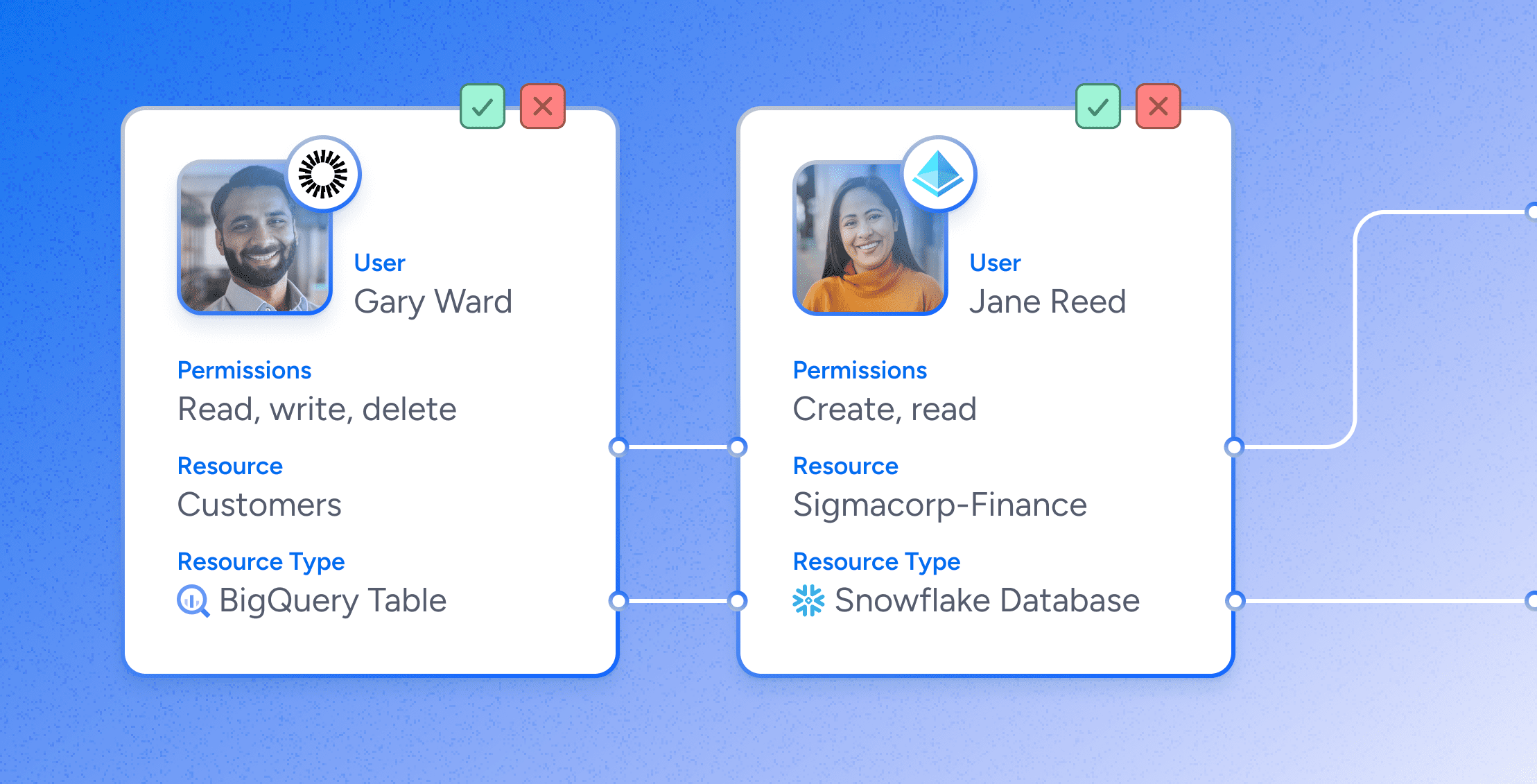
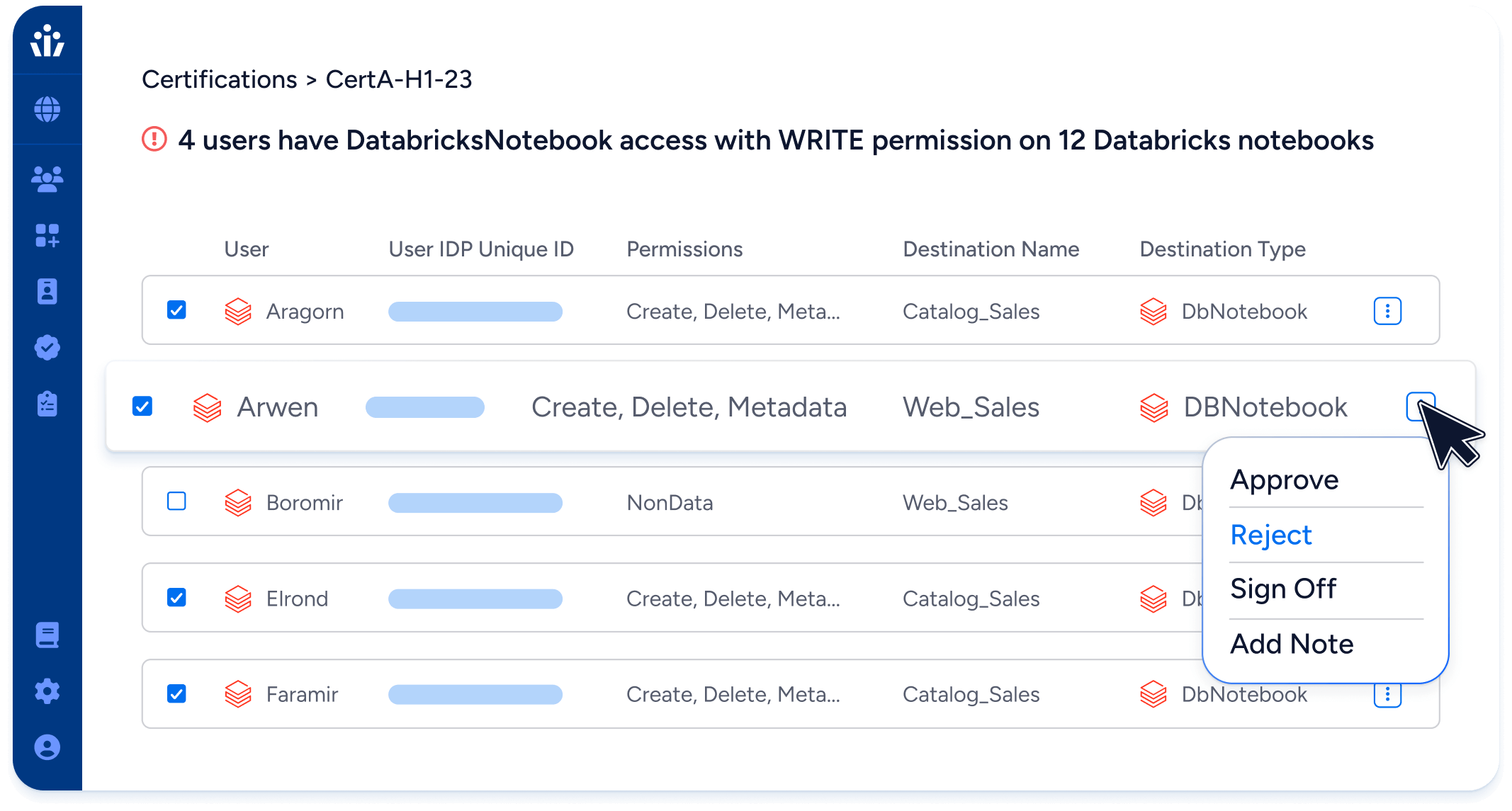
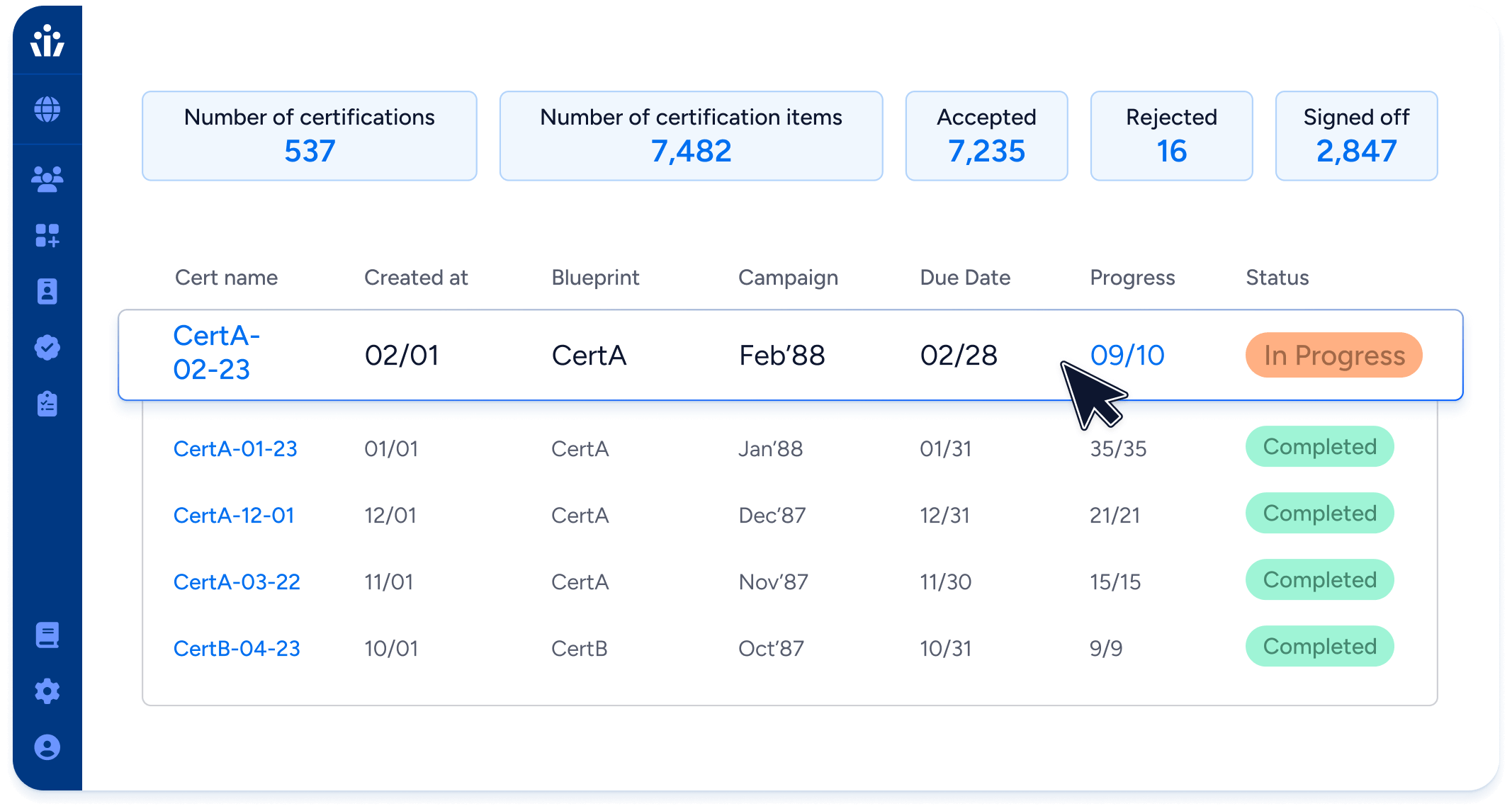
- Orchestrate end-to-end access reviews from certification to renewal in a unified workflow, delegating decisions to LOB managers.
- Remove excessive or dormant permissions during certification.
- Prioritize reviews of privileged accounts, including local users and admins who might fall through the cracks of SSO and IGA tools.
- Automate evidence collection for ongoing audits.
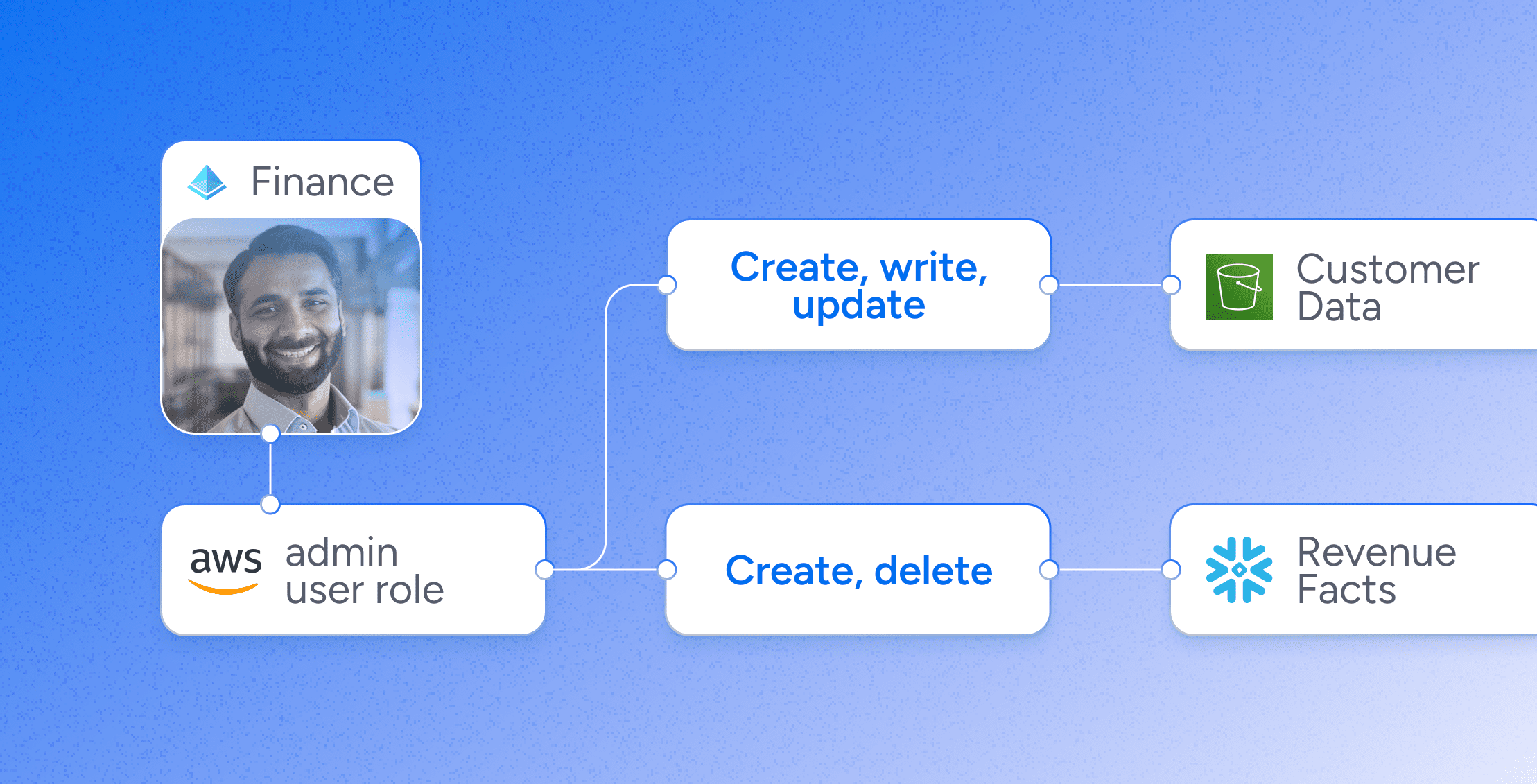
Governance, Risk & Compliance (GRC)
- Define and enforce separation of duties policies.
- Validate entitlements for sensitive resources outside the purview of SSO and IGA.
- Create governance workflows to prevent self-reviews and comply with industry regulations like SOC 2 Type II, ISO 27001, PCI DSS, and HIPAA.
Compatible with all frameworks
Veza’s Next-Gen IGA solution is compatible with all major compliance frameworks, including Sarbnes Oxley (SOX), SOC 2 Type II, ISO 27001, PCI DSS, GDPR, HIPAA, and more.

Sarbanes Oxley (Sox)

SOC 2 Type II

ISO 27001

GDPR


“As a fintech company, our customers rely on us to maintain a strong compliance posture to keep their data secure. Veza helped us implement governance standards within our Snowflake deployment by giving my team visibility to manage all identities and their access to data in Snowflake. Veza empowers my teams with the insights they need to manage and mitigate risks.”
Steven Hadfield | Senior Staff Product Security Engineer


“Our current user management is federated across multiple systems, and that makes it very tricky for us to manage and understand who has access to what. So looking at a system like Veza, it allowed us to really understand that in a very simple and easy way. And honestly, the first time we plugged it in, we knew we needed to get this product.“
Stephen Cihak | Senior Director, Cloud Platform & Site Reliability


“Veza has given our team unprecedented visibility to manage all identities and their access, enforce policies, and mitigate risks. We appreciate Veza’s flexibility in adding new integrations for both common and industry unique applications.”
Brad Lontz | SVP of IT & CIO