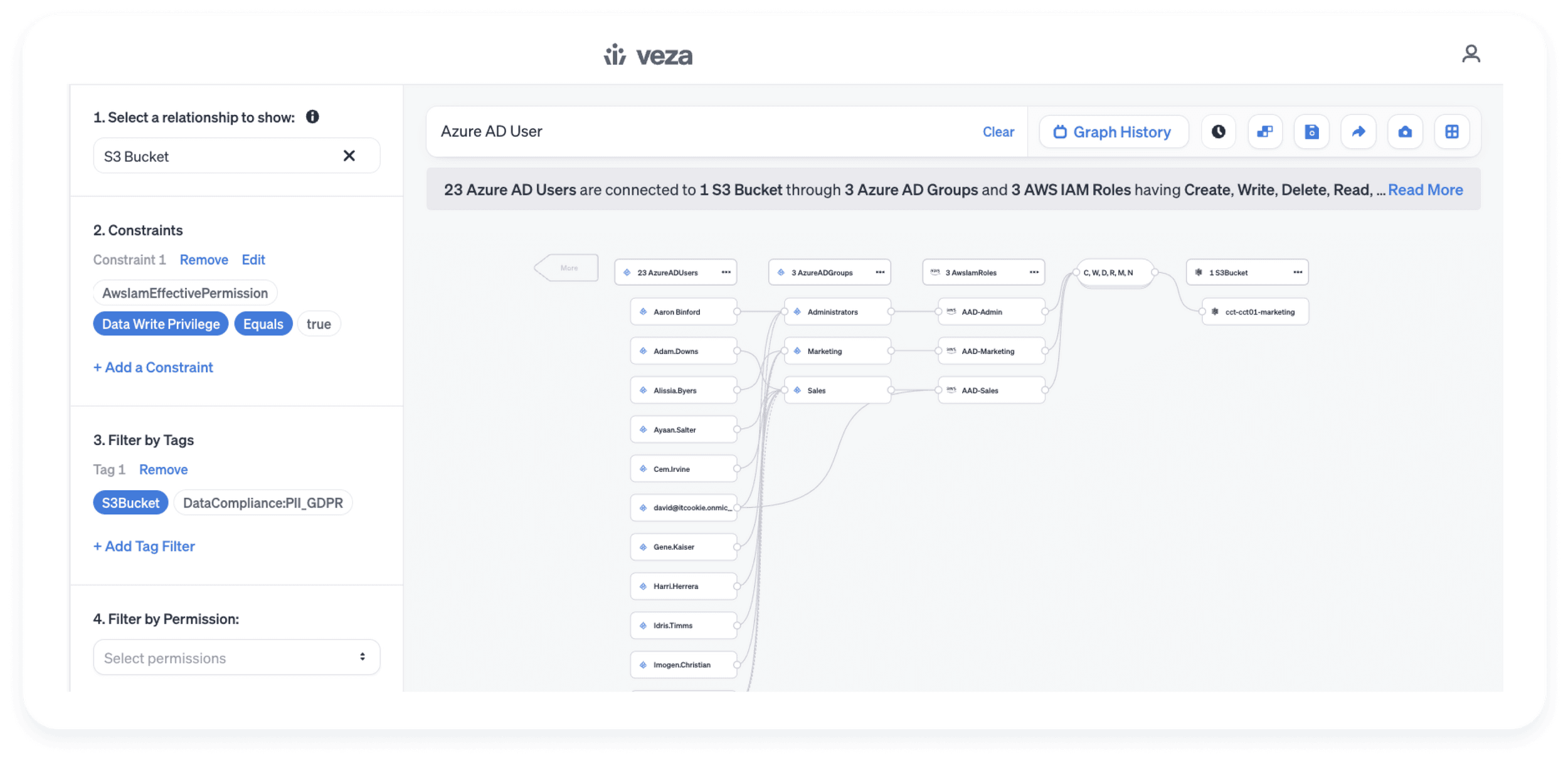
Discover true permission levels as a result of all layers of access controls and IAM policies, across identities and cloud data resources
- Okta or AWS IAM Users with access to Redshift tables and further filter for those who have delete permissions on sensitive Redshift tables
- Misconfigured Okta or Azure AD Groups granting broader than intended access to privilege account roles into AWS
Pre-built and customizable reports for cloud data security
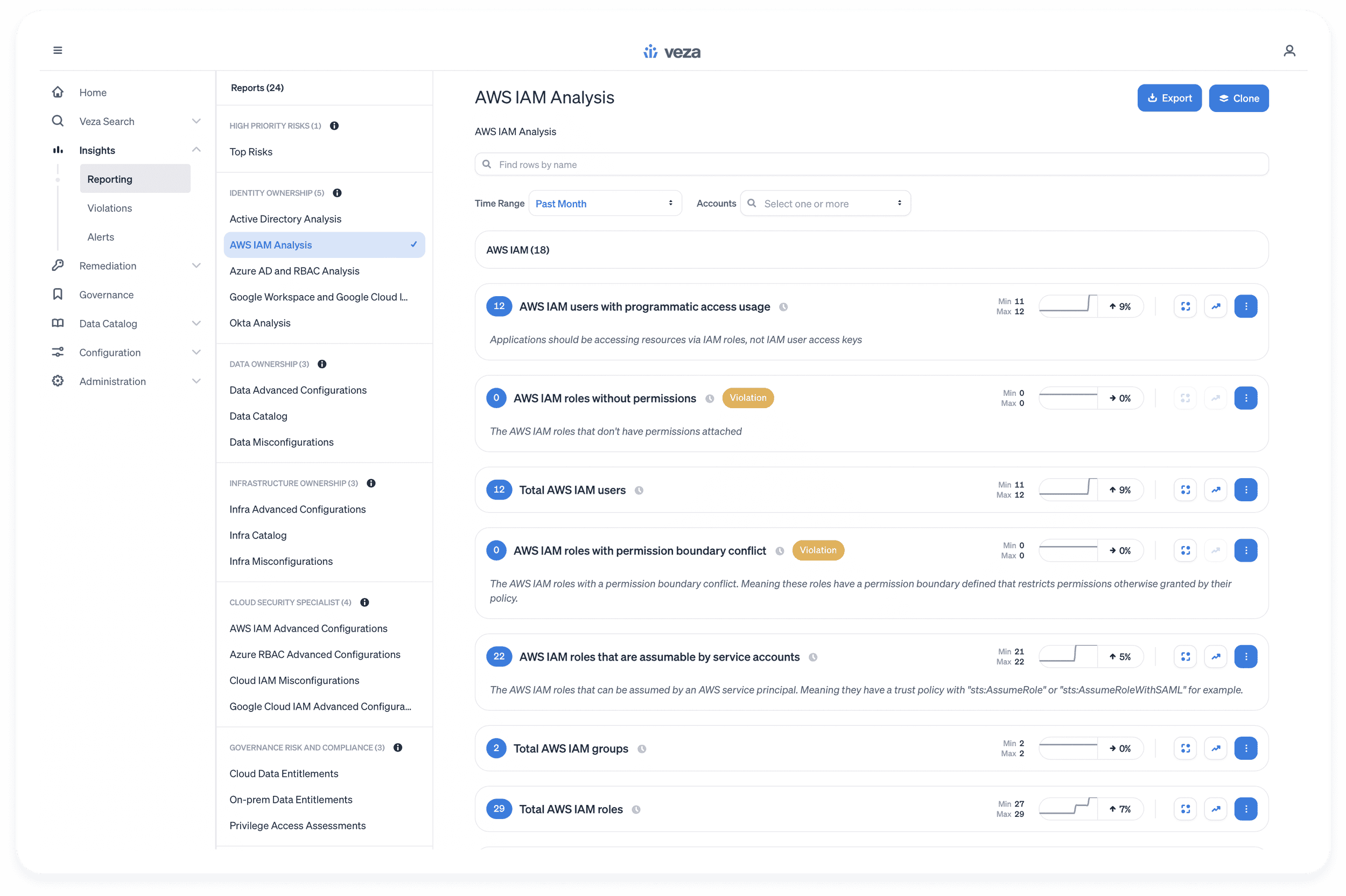
Instant visibility and actionable intelligence for privilege management. Identify users with excessive privileges, perform groups and roles analysis, and collect metrics out of data sources.
- Permission Boundary: AWS IAM roles with permission boundary conflicts
- Privilege Escalation: AWS IAM roles with iam:AttachGroupPolicy permission
- Lateral Movement: AWS IAM roles with iam:PassRole permission on all resources
- Shadow Admins: AWS IAM users or roles with iam:CreateAccessKey permission
Quick visibility into data authorization misconfigurations and anomalies
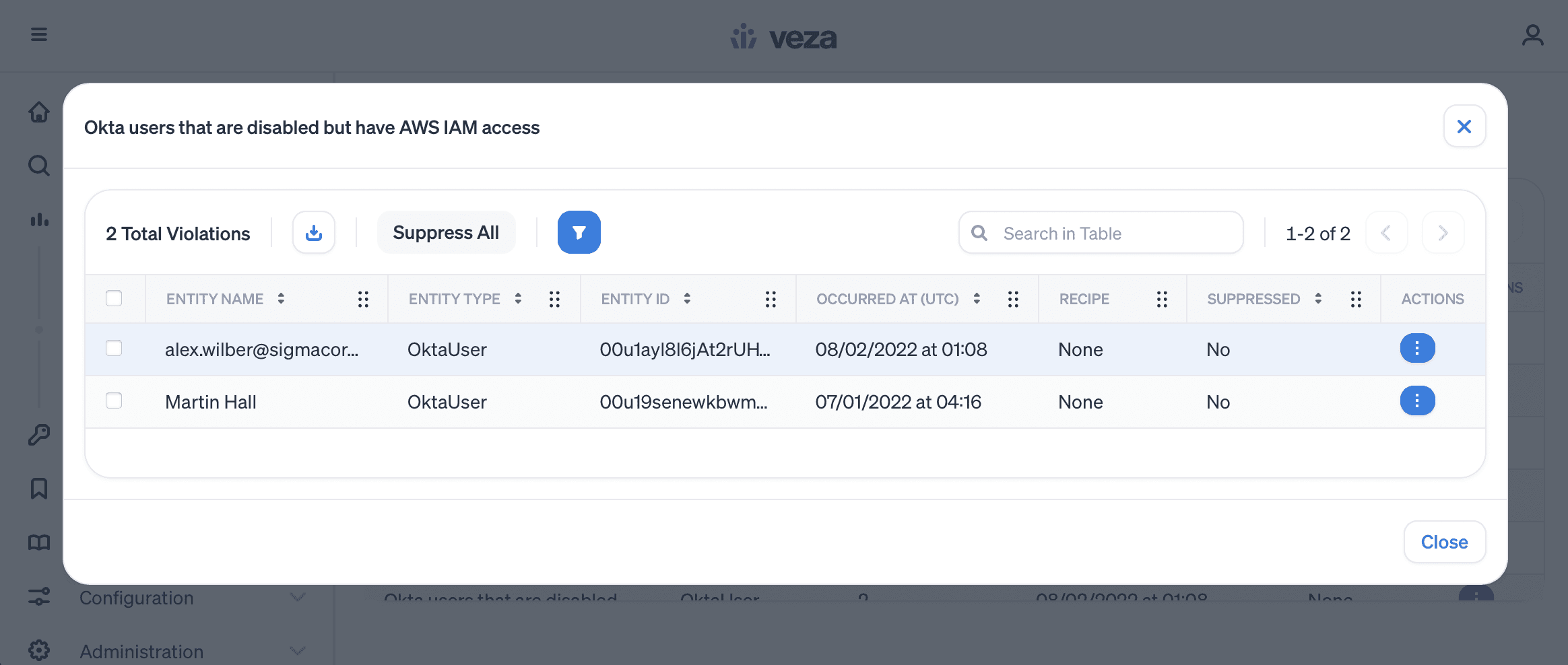
Continuously scan the identity-to-data relationships using saved queries categorized as violations to find deviations from industry and organization best practices.
- AWS IAM unused customer-managed policies
- Okta or Azure AD users who are no longer at the company but have lingering access to AWS resources
- Okta or Azure AD users whose MFA is turned off but can change and delete sensitive data in S3 buckets.