Featured Resources
-
 Report
ReportAI. Visibility. Machine Identity. The Latest Market Guide for IGA.
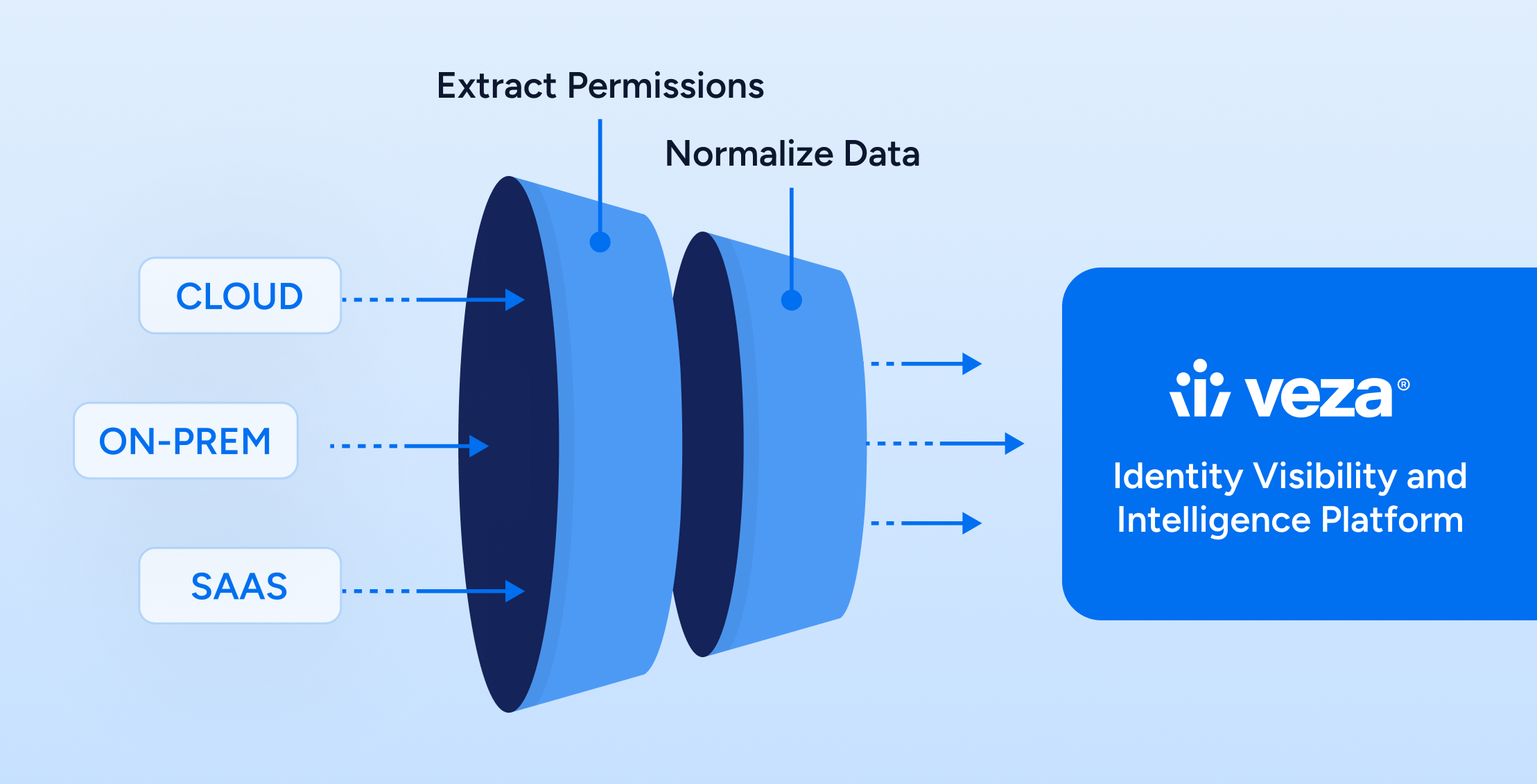
Gartner defines identity governance and administration (IGA) as the solution to manage the identity life cycle and govern access across on-premises and cloud environments. To accomplish this, IGA tools aggregate and correlate disparate identity and access rights data, and provide full capability controls over accounts and associated access. Download the report to learn how leading […] -
 Report
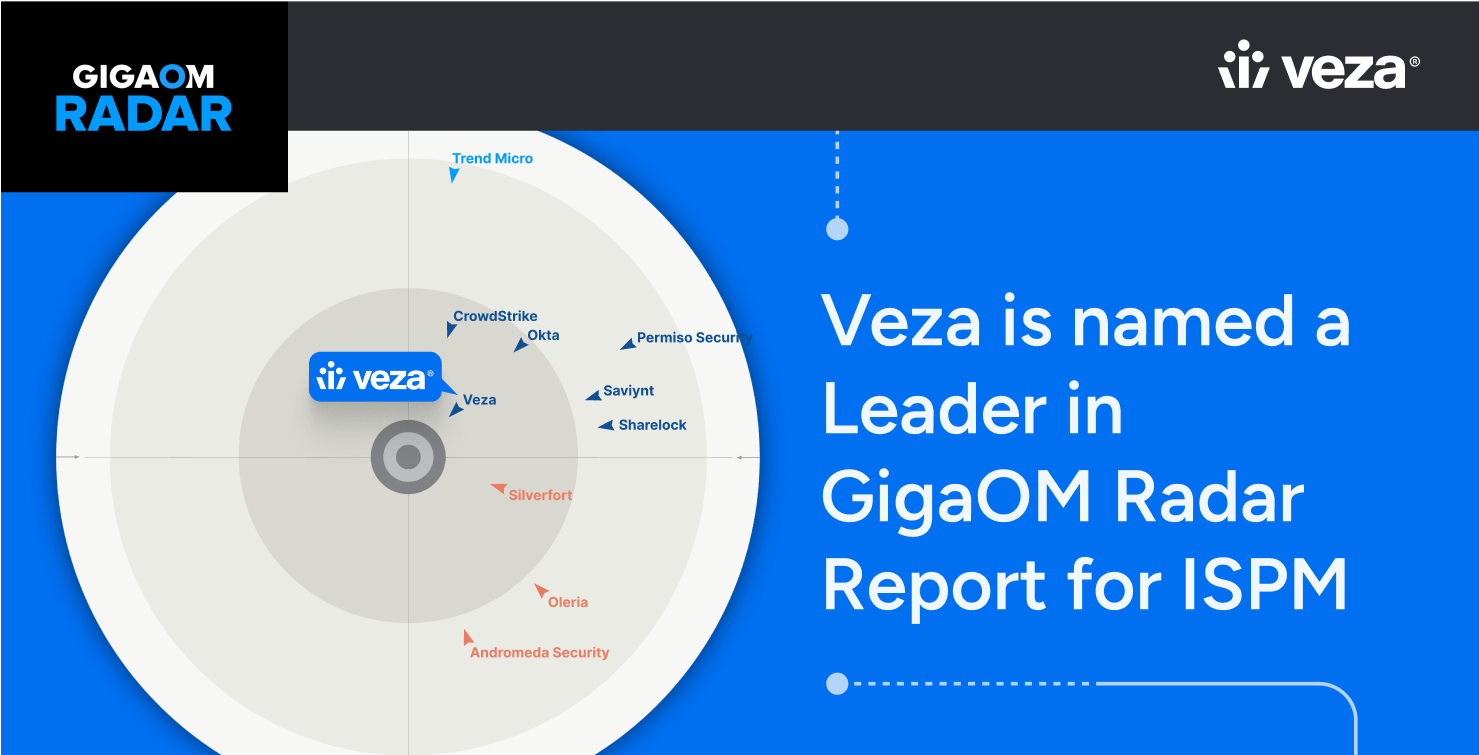
ReportGigaOm Radar for ISPM
The #1 attack vector in cybersecurity? Identity.This GigaOm Radar shows how top ISPM platforms help you close identity gaps before attackers exploit them. Traditional IAM grants access. ISPM goes further—continuously monitoring and reducing identity risk across users, service accounts, cloud roles, and SaaS apps. What You’ll Learn: Download the report by filling out the form. […]
Explore our resources
-
 Whitepaper
WhitepaperEnsuring Insurability: How to Strengthen Your Cyber Insurance Posture
Learn more -
 Guide
GuideVeza for Insider Threat
Learn more -
 Guide
GuideIntelligent Access Guide for Microsoft Azure: Security, Access Control, Compliance, & Roles
Learn more -
 Guide
GuideIdentity Security IS the Foundation for Zero Trust
Learn more -
 Solution Brief
Solution BriefOpenAI Identity Governance | Veza for OpenAI Solution Brief
Learn more -
 EBook
EBookISPM Buyer’s Guide | Identity Security & Zero Trust
Learn more
-
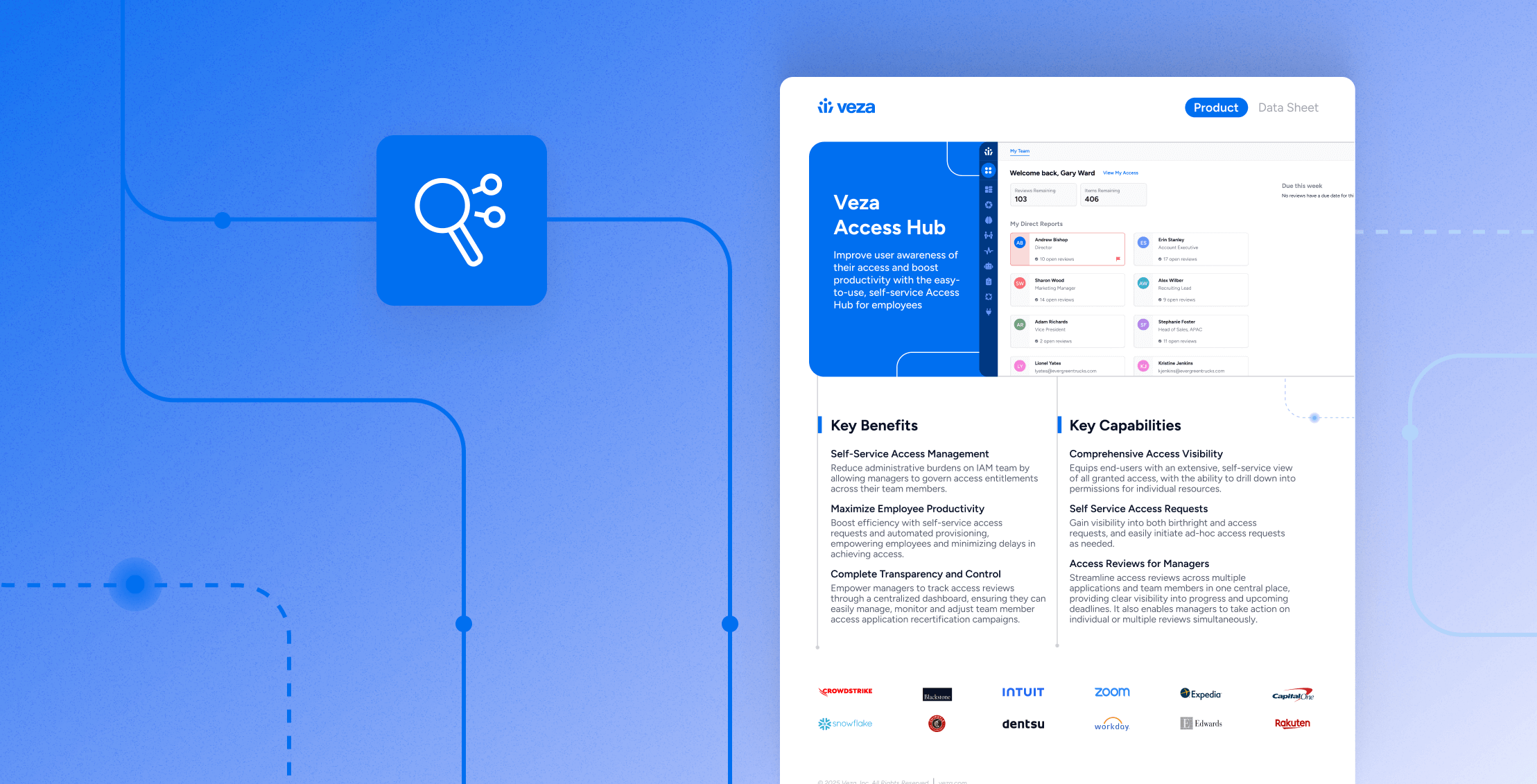 Data Sheet
Data SheetAccess Hub Data Sheet
Learn more -
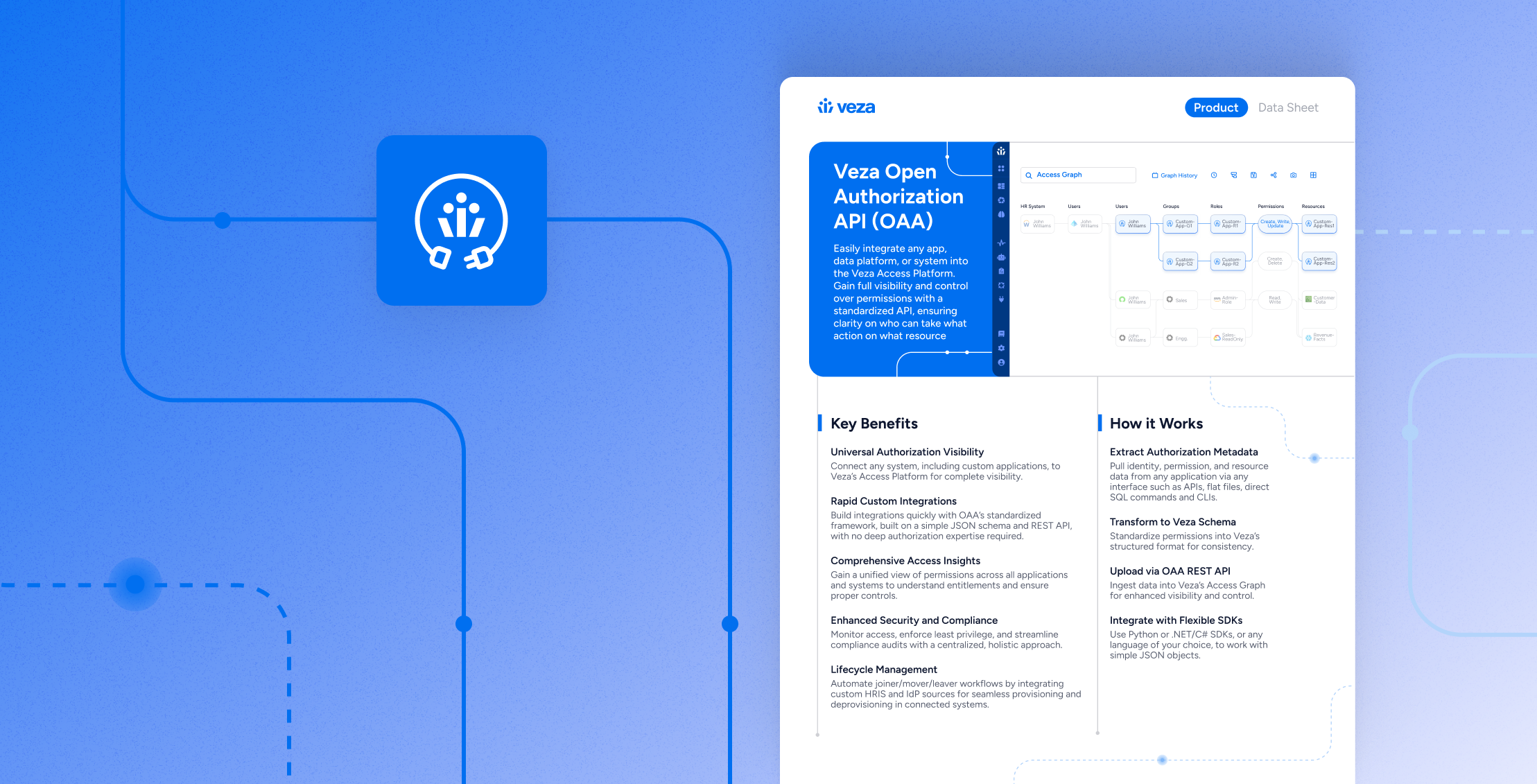 Data Sheet
Data SheetOpen Authorization API – Data Sheet
Learn more -
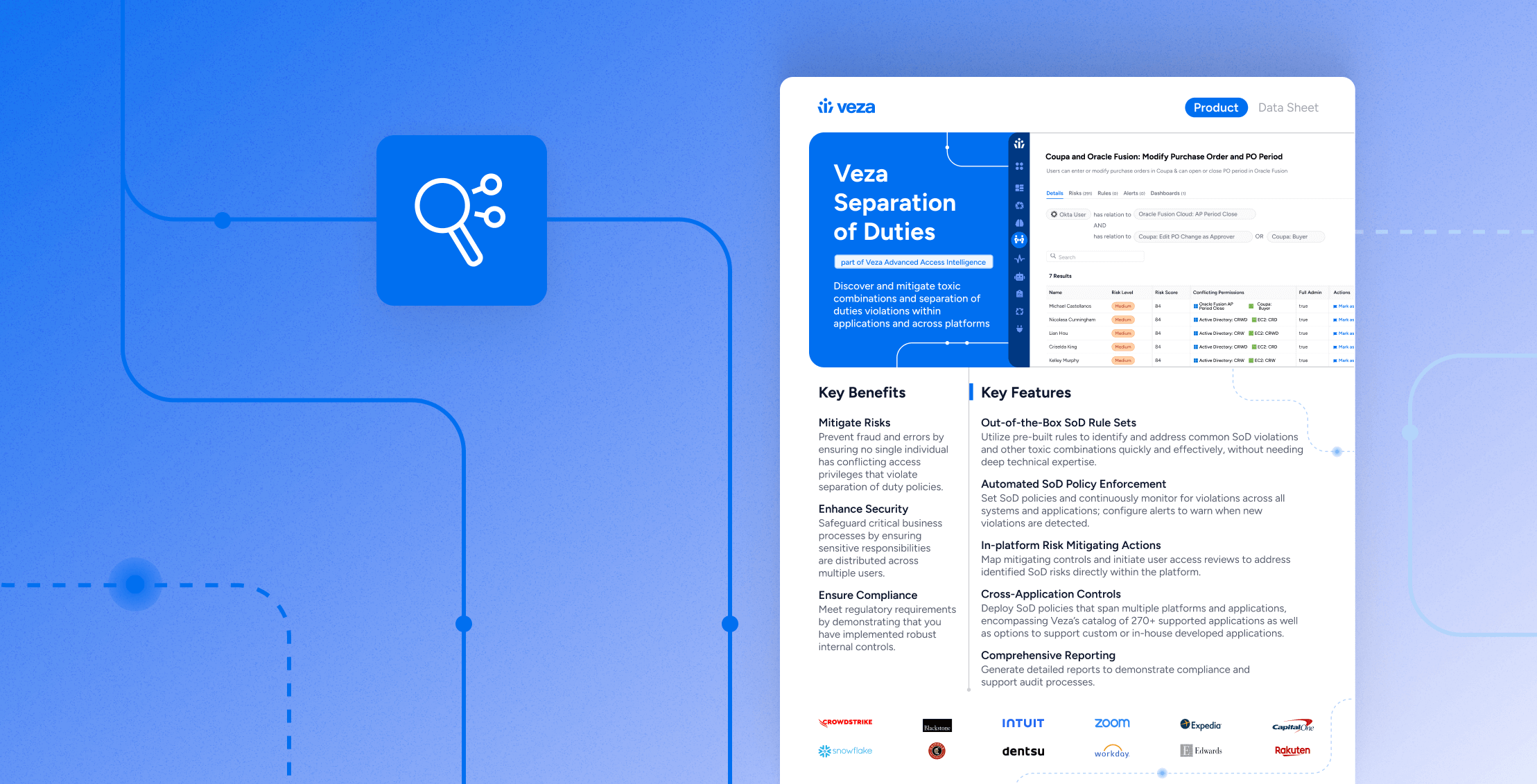 Data Sheet
Data SheetSeparation of Duties (SoD) Data Sheet
Learn more -
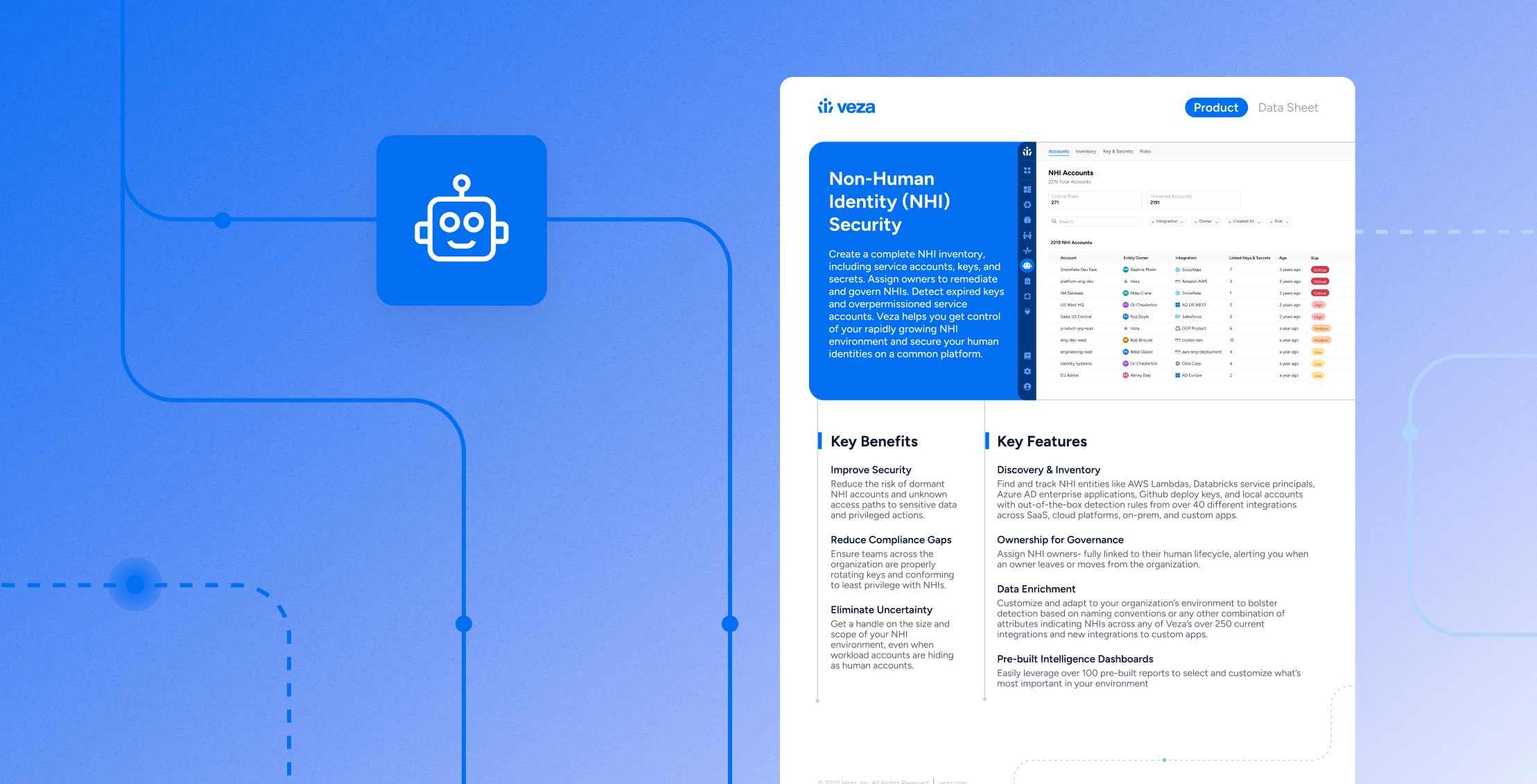 Data Sheet
Data SheetNon-Human Identity (NHI) Security Data Sheet
Learn more -
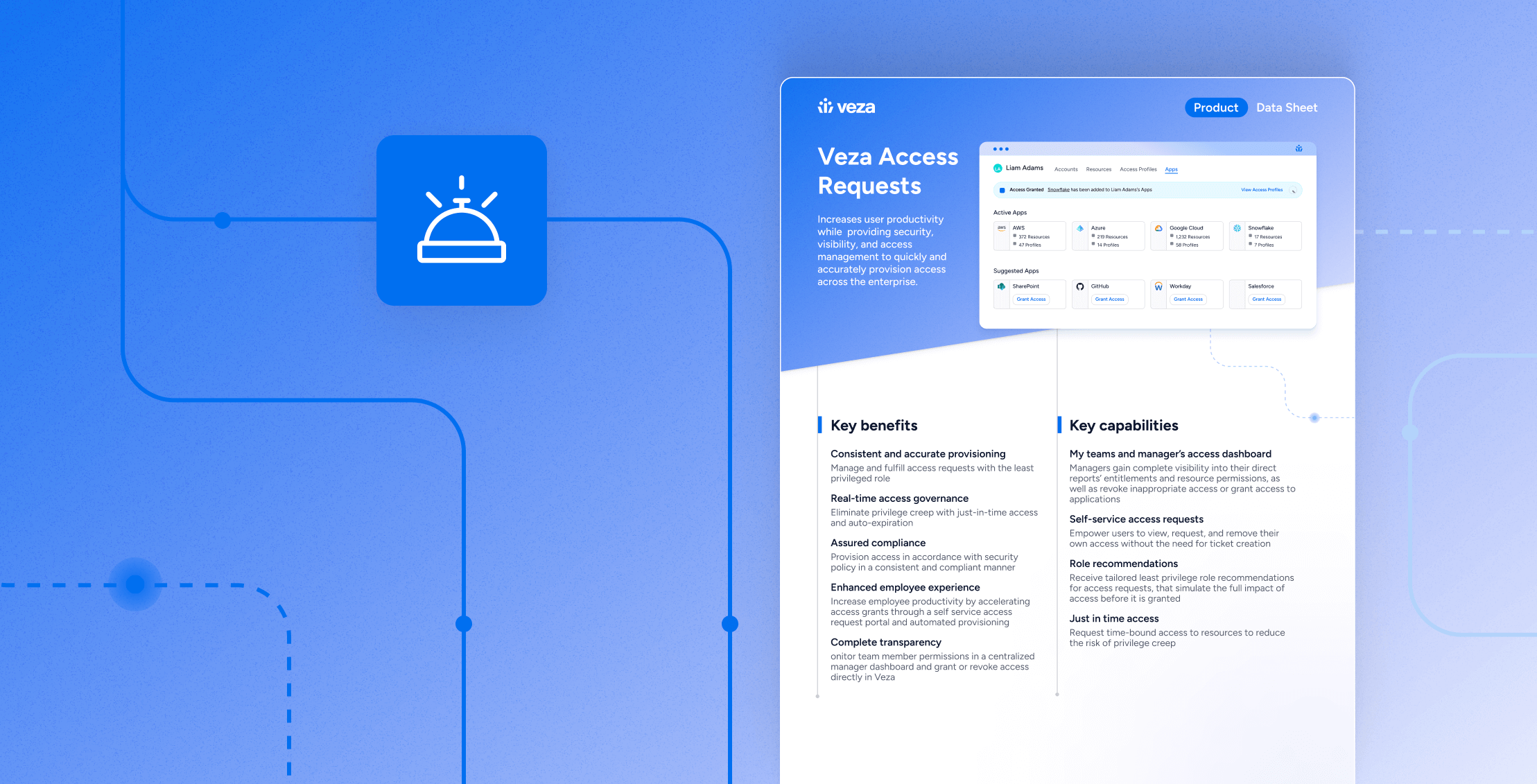 Data Sheet
Data SheetAccess Requests Data Sheet
Learn more -
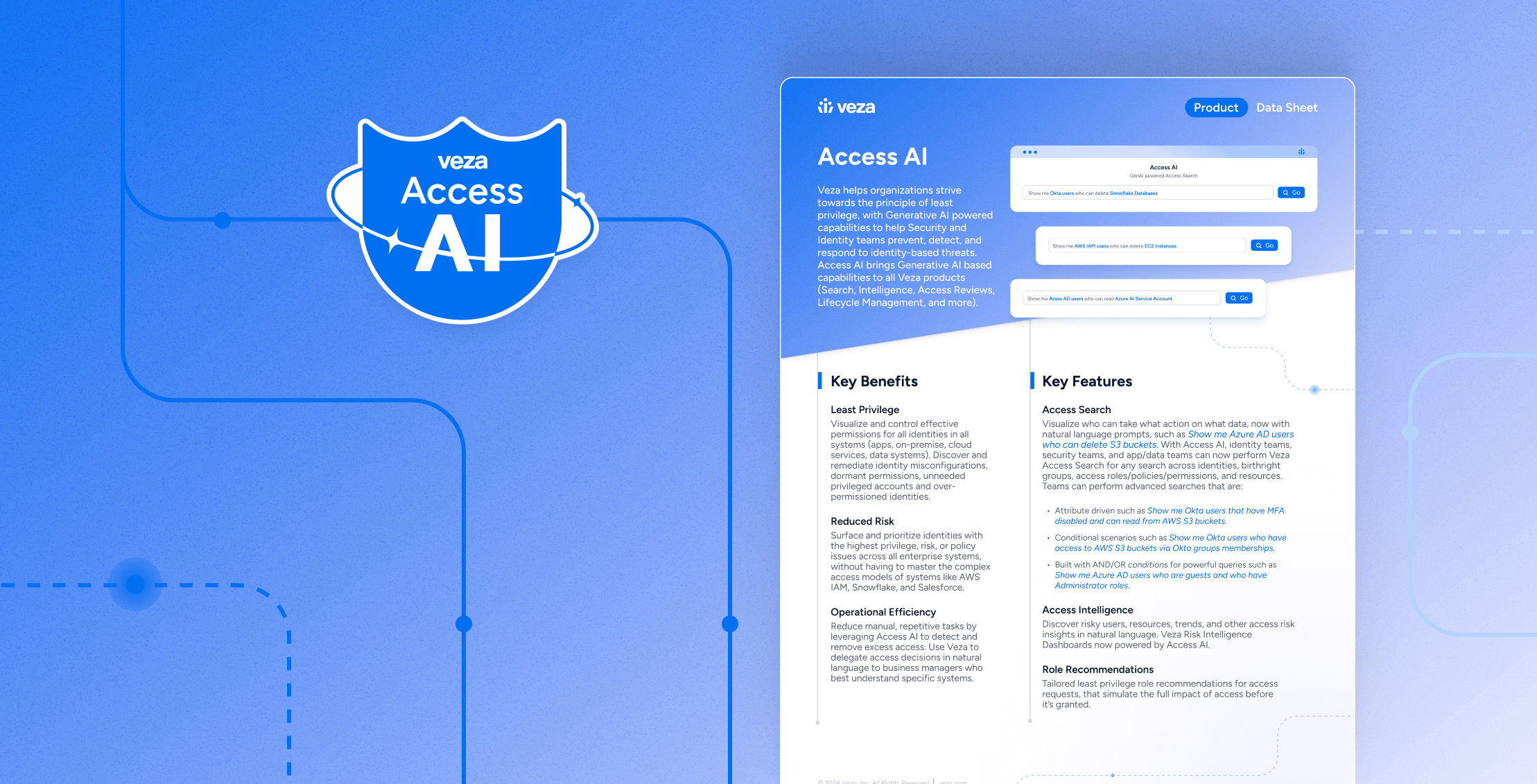 Data Sheet
Data SheetAccess AI Data Sheet
Learn more
-
 Solution Brief
Solution BriefOpenAI Identity Governance | Veza for OpenAI Solution Brief
Learn more -
 Solution Brief
Solution BriefVeza + Salesforce: Simplifying Access Control & Protecting Sensitive Data
Learn more -
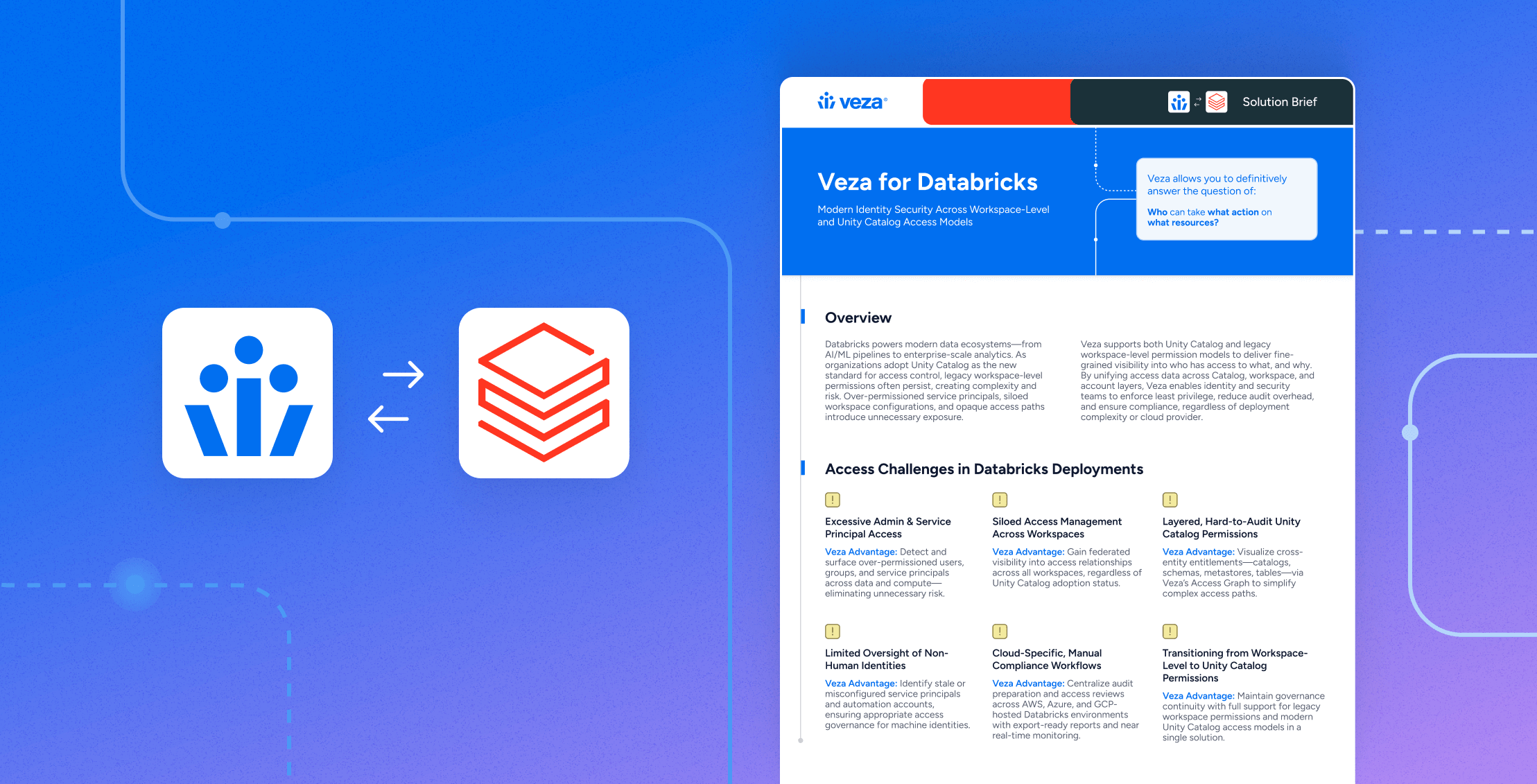 Solution Brief
Solution BriefVeza for Databricks | Access Governance for Unity Catalog & Workspaces
Learn more -
 Solution Brief
Solution BriefNonhuman Identity Management (NHI) | Veza
Learn more -
 Solution Brief
Solution BriefVeza for Oracle
Learn more -
 Solution Brief
Solution BriefVeza for HashiCorp Vault
Learn more
-
 Case Study
Case StudyStreamlined compliance and least privilege at Sallie Mae
Learn more -
 Case Study
Case StudyVeza for Identity Security at Snowflake
Learn more -
 Case Study
Case StudyUnlocking Automation & Compliance: CopperPoint’s Journey with Veza
Learn more -
 Case Study
Case StudyHow the City of Las Vegas safeguards the data of 42 million visitors a year with Veza
Learn more -
 Case Study
Case StudyHow Genesys runs access reviews 3x faster with Veza
Learn more -
 Case Study
Case StudyCybersecurity leader transforms access reviews with Veza, making an unmanageable process manageable
Learn more
-
 Video
VideoVideo – Google Ventures | Veza – why authorization matters, why now
Learn more -
 Video
VideoMaking Sense of Authorization – Before & After with Veza
Learn more -
 Video
VideoDemo – Veza’s Open Authorization API
Learn more -
 Video
VideoMeet Veza – The Data Security Platform Built on the Power of Authorization
Learn more -
 Video
VideoDemo – Veza for data lake security
Learn more
-
 Whitepaper
WhitepaperEnsuring Insurability: How to Strengthen Your Cyber Insurance Posture
Learn more -
 Whitepaper
WhitepaperNavigating Separation of Duties (SoD) Challenges
Learn more -
 Whitepaper
WhitepaperTransforming Access Lifecycle Management with Veza’s Access Profiles
Learn more -
 Whitepaper
WhitepaperThe Veza Advantage – Product Whitepaper
Learn more -
 Whitepaper
WhitepaperVeza for PAM
Learn more -
 Whitepaper
WhitepaperReport: Trends for Securing Enterprise Data
Learn more
-
 EBook
EBookISPM Buyer’s Guide | Identity Security & Zero Trust
Learn more -
 EBook
EBookIntelligent Access: Modernizing Identity with Just in Time Access
Learn more -
 EBook
EBookIntelligent Access: Strategies for Achieving Least Privilege in the Modern Enterprise
Learn more -
 EBook
EBookA Practitioner’s Guide to Intelligent Access
Learn more -
 EBook
EBook3 Essential Access Governance Strategies for AWS
Learn more
-
 Guide
GuideVeza for Insider Threat
Learn more -
 Guide
GuideIntelligent Access Guide for Microsoft Azure: Security, Access Control, Compliance, & Roles
Learn more -
 Guide
GuideIdentity Security IS the Foundation for Zero Trust
Learn more -
 EBook
EBookISPM Buyer’s Guide | Identity Security & Zero Trust
Learn more -
 Guide
GuideVeza Brings Identity Security to Your Existing Directory Systems
Learn more
-
 Guide
GuideVeza for Insider Threat
Learn more -
 Guide
GuideIntelligent Access Guide for Microsoft Azure: Security, Access Control, Compliance, & Roles
Learn more -
 Guide
GuideIdentity Security IS the Foundation for Zero Trust
Learn more -
 EBook
EBookISPM Buyer’s Guide | Identity Security & Zero Trust
Learn more -
 Guide
GuideVeza Brings Identity Security to Your Existing Directory Systems
Learn more