Veza Access Platform
Before Veza, it was practically impossible to see the truth of enterprise access. There was no way to unravel the web of identities and permissions spread across hundreds of systems. Only Veza enables identity and security teams to visualize and right-size access permissions, across all systems.
Products
Access Security
Access Search
Visualize and control who has access to data across all enterprise systems. Only Veza analyzes permissions to resources for all identities (human or machine), helping security teams reduce risk before and after attacks.
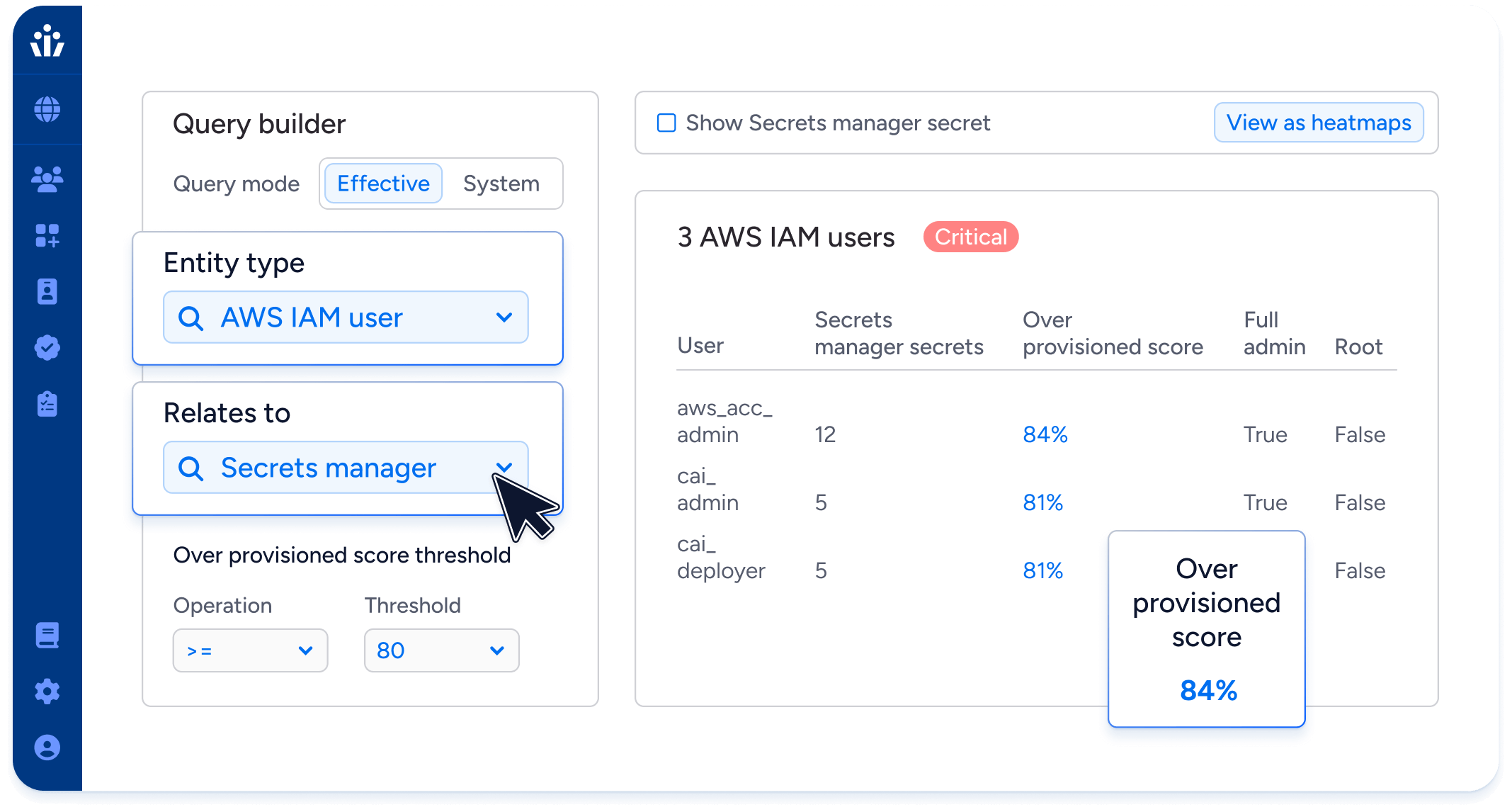
Access Intelligence
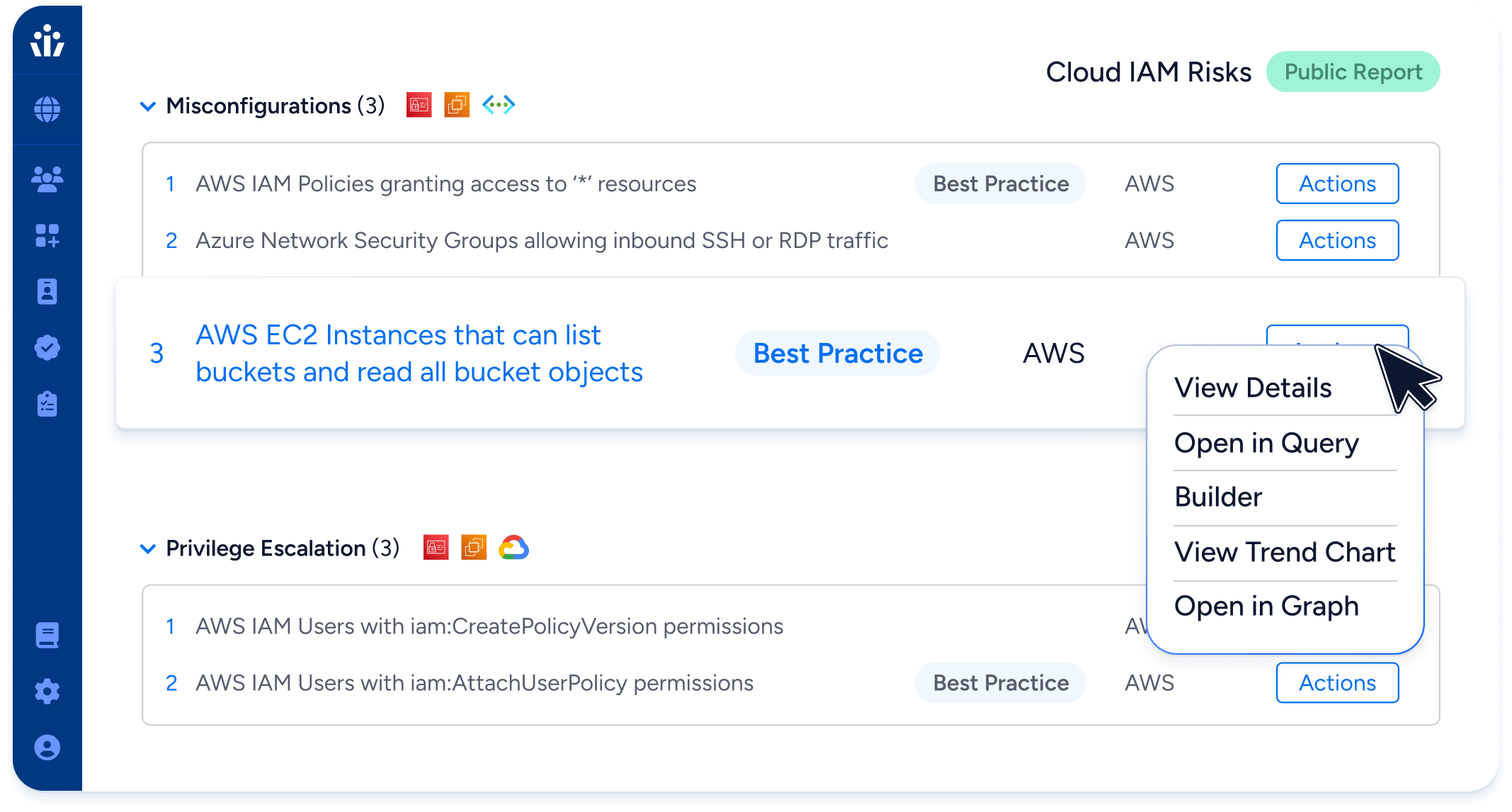
Detect privileged users, dormant permissions, policy violations and misconfigurations with Veza’s 500+ pre-built queries. Veza shows you where to focus for maximum impact, and it even creates tickets for remediation.
Access AI
Veza helps organizations strive towards the principle of least privilege, with Generative AI-powered capabilities to help Security & Identity teams prevent, detect, and respond to identity-based threats. Access AI brings GenAI based capabilities to all Veza products.
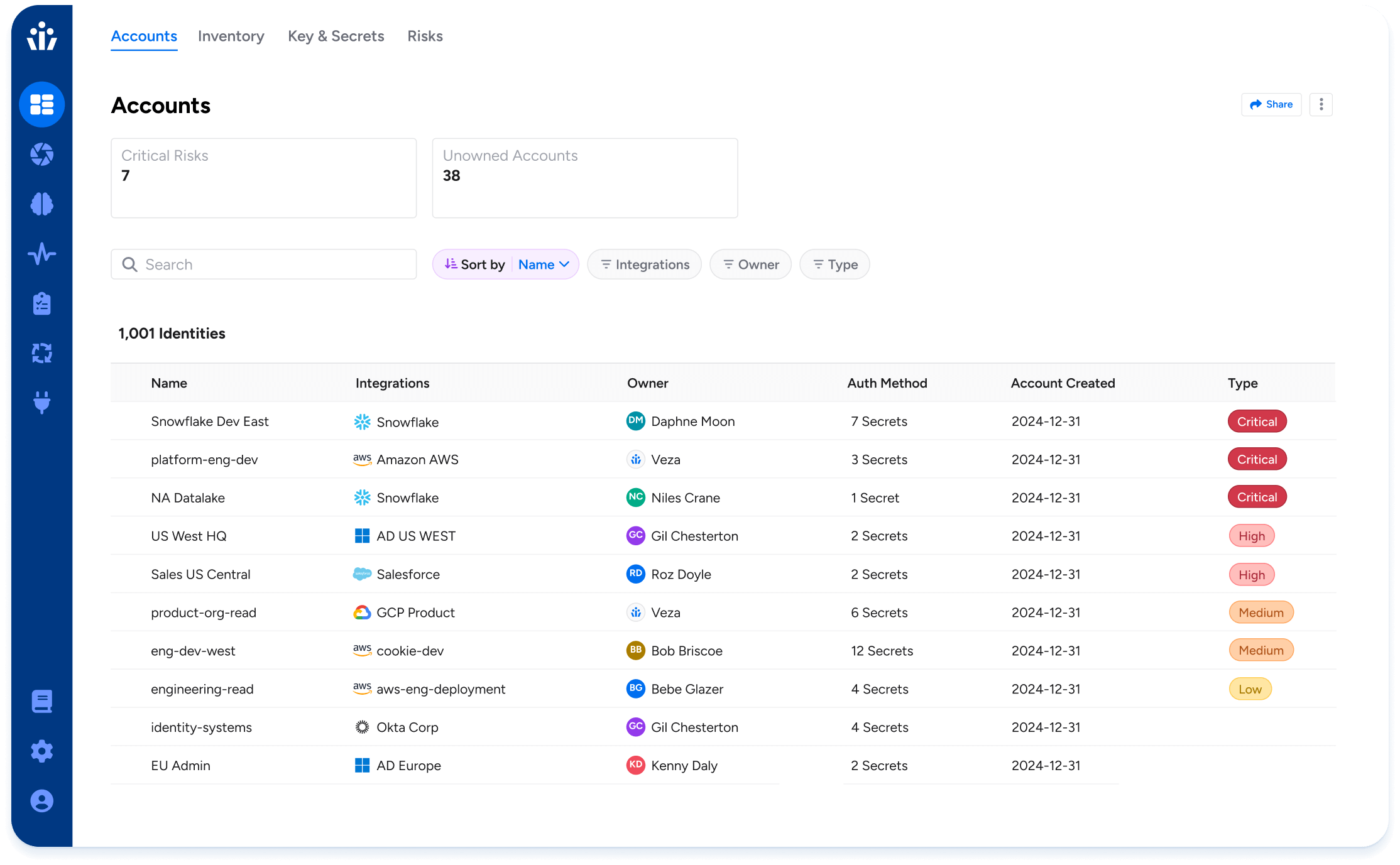
NHI Security
Gain full visibility and control over your Non-Human Identities (NHIs) with Veza. Create a complete inventory of service accounts, keys, and secrets. Assign ownership to drive governance and remediation. Detect expired credentials and over-permissioned accounts to reduce risk. Secure your NHIs and human identities together on a single, unified platform.
Access Governance
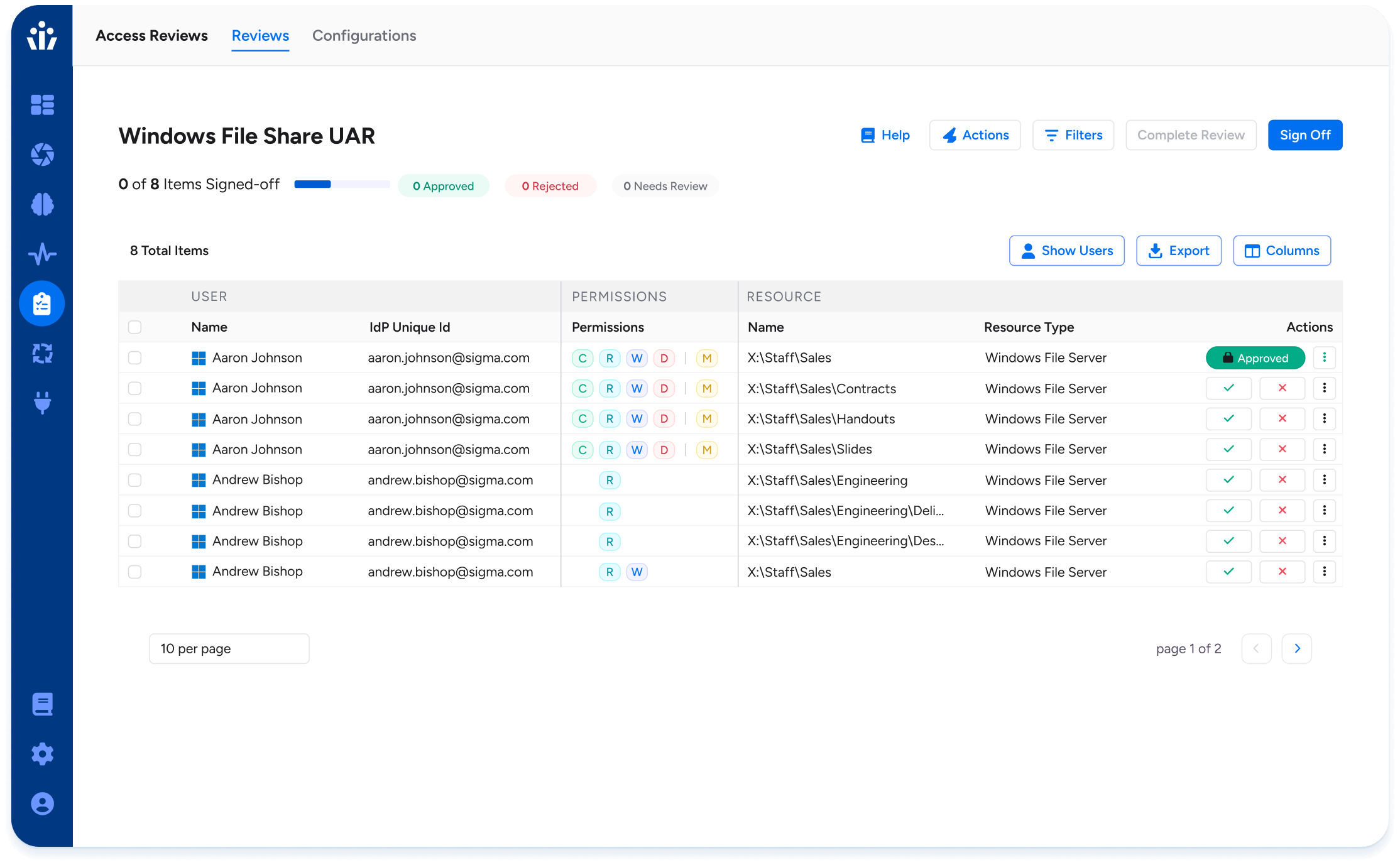
Access Reviews
Automate user access certifications, creating comprehensive campaigns in record time. Delegate with confidence by prioritizing risky access first and giving reviewers the context they need to approve or reject.
Lifecycle Management
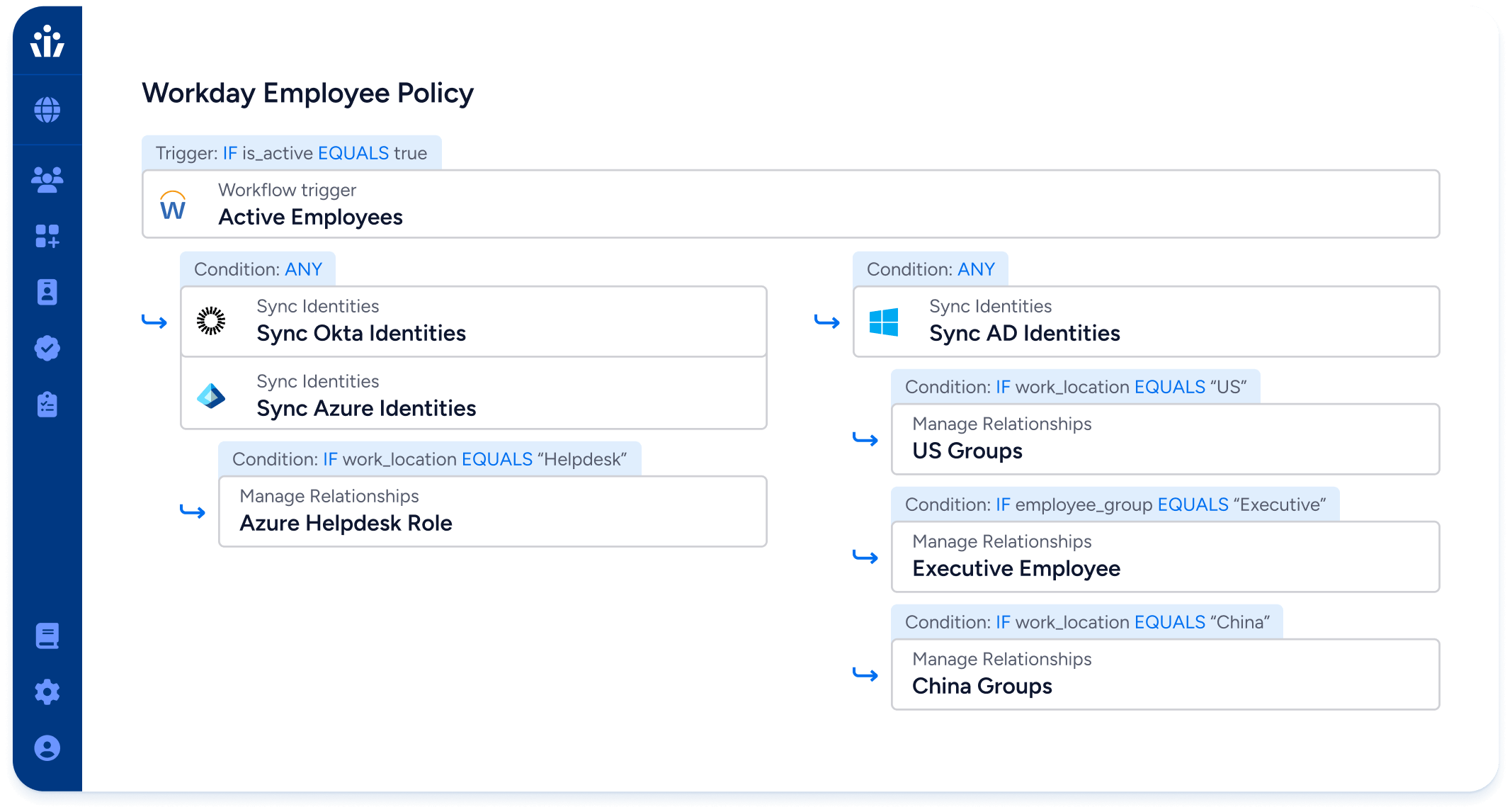
Automatically grant and revoke access when a user joins, changes role, or leaves. Only Veza can dry-run your changes to prevent access mistakes and policy violations before they happen.
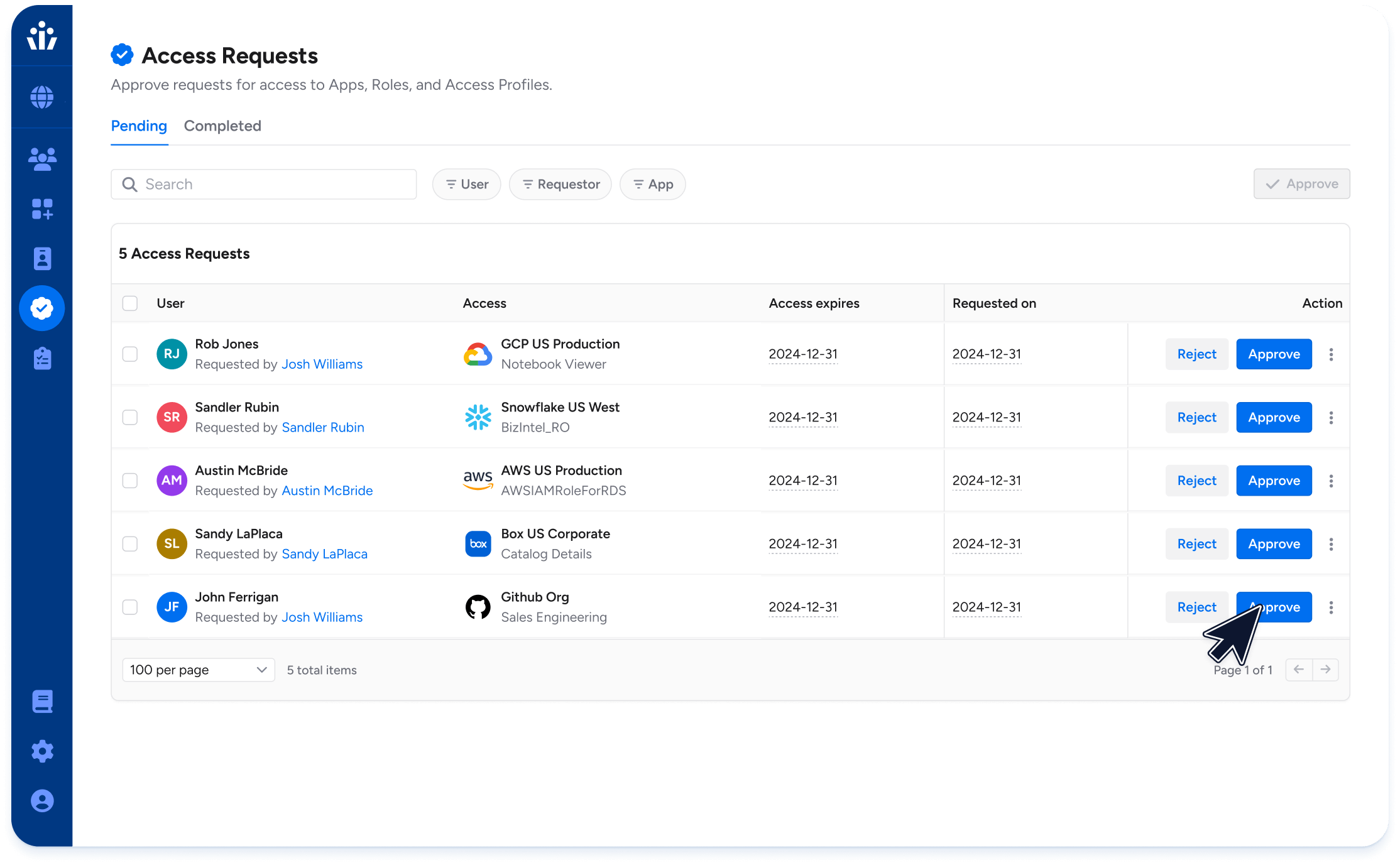
Access Requests
Increases user productivity while providing security, visibility, and access management to quickly and accurately provision access across the enterprise.
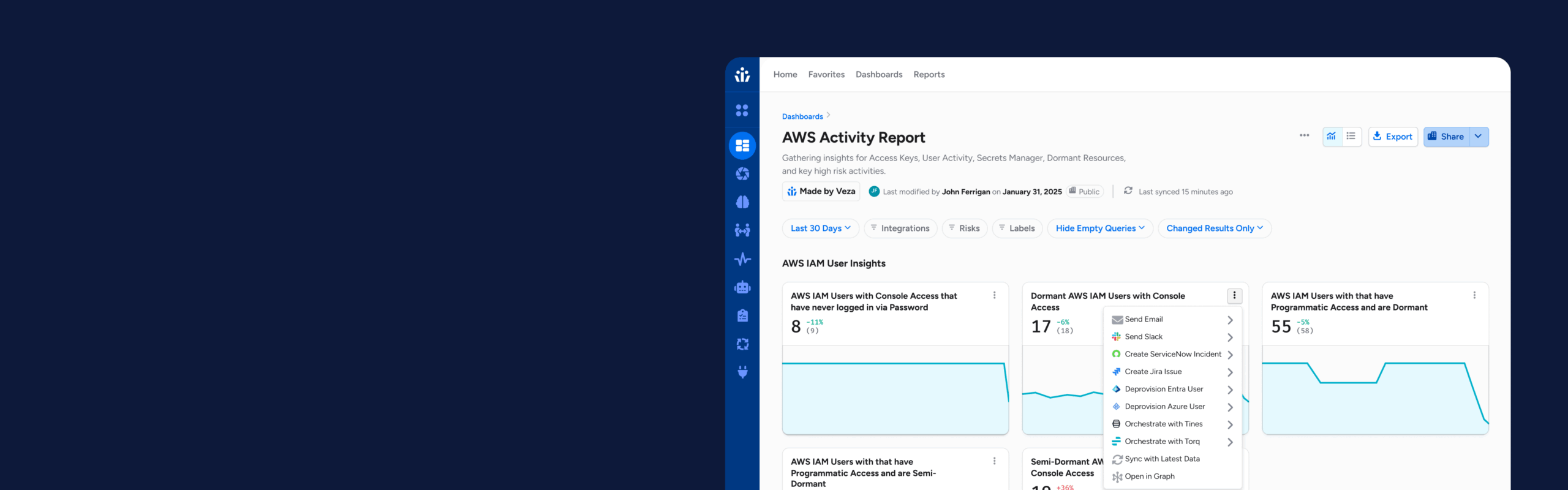
Veza Actions
Veza Actions transforms identity security from a passive control mechanism into an active operational engine.
Platform Features
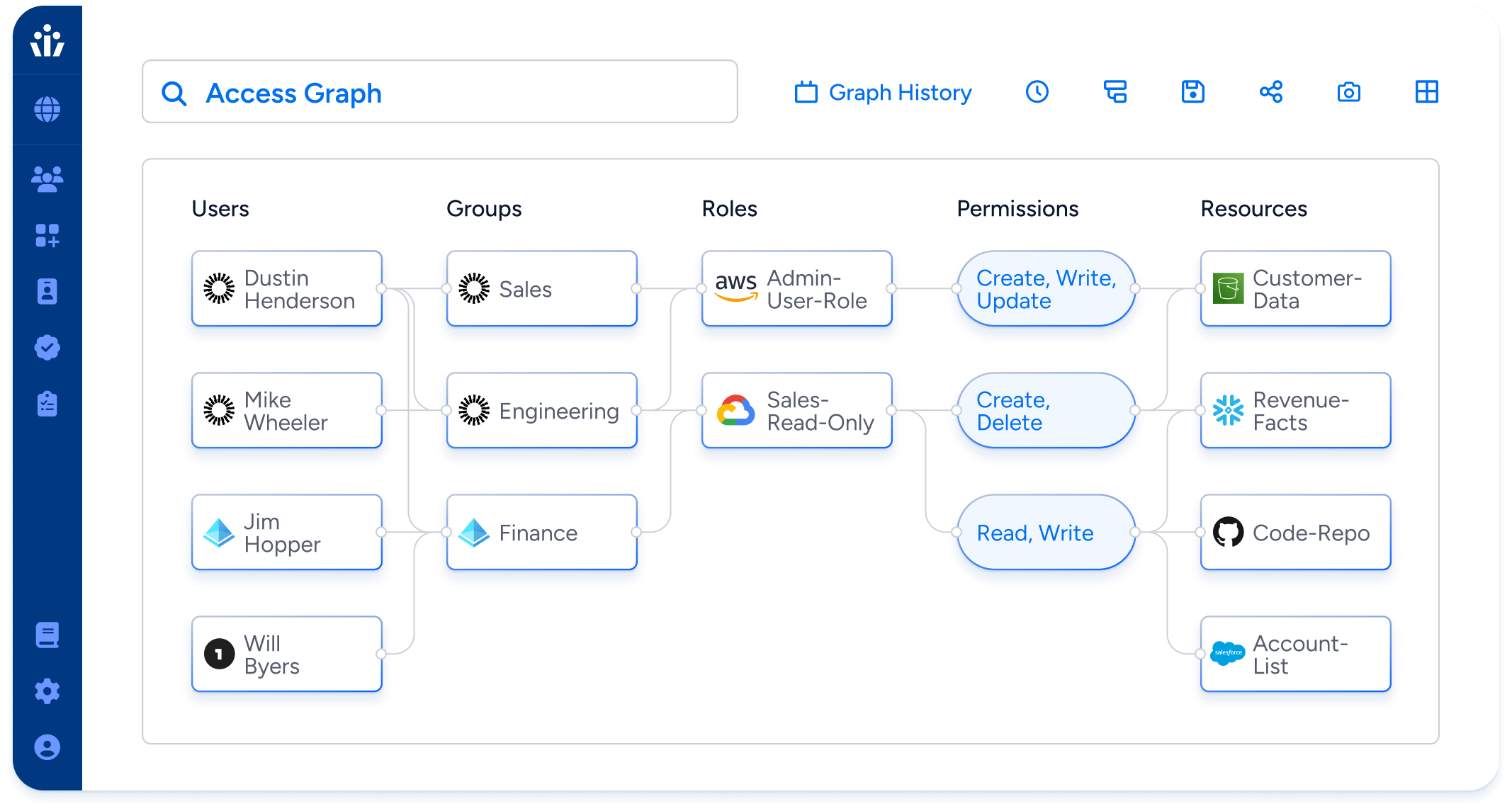
Access Graph
Visualize the relationships between all human and machine users, apps, systems, and data sources. The Access Graph traverses users, groups, roles, and policies to connect identities to their “effective permissions”, explained in the simple language of “create, read, update, delete”.

Integrations
300+ agentless, read-only integrations with identity systems, cloud service providers, data systems, and on-prem applications reveal the effective permissions to your most critical data. Veza integrations deploy fast, without the risk of service interruptions. For everything else, the Open Authorization API enables rapid development of integrations for custom applications without expensive professional services engagements.

API First
Programmatically interact with core Veza features including search, access reviews, and more via REST API. Integrate Veza with your existing tools to automate processes, support existing workflows, integrate with ticketing systems, and provide data enrichment for other solutions.

Enterprise Scale
Legacy systems built on relational databases haven’t kept up with the explosion of entities in the cloud. Veza’s purpose-built graph infrastructure makes light work of the massive scale of enterprise cloud IAM to support AI/ML-based capabilities, like access recommendations, universal natural language search, and more.

Platform Security
Veza practices regular independent penetration testing, data-at-rest and inflight encryption, strict role-based access controls, complete tenant isolation and zero external access by design, and we use our own products to monitor and secure access to our environments. Veza is SOC 2 Type I, SOC 2 Type II, and ISO 27001 certified, demonstrating our dedication to security and compliance across all our processes, people, and technology.

Modernize identity Governance at Blackstone
Learn More
-
 Report
ReportVeza Named NHI Leader In The Frost Radar™ Report For 2025
Learn moreFrost & Sullivan has recognized Veza as a leader in their latest report, Frost Radar™: Non-Human Identity Solutions, with standout scores in both Innovation and Growth. This independent validation highlights how Veza is redefining the way enterprises discover, govern, and secure machine and workload identities. As machine identities multiply far faster than human users, organizations […] -
 Report
ReportVeza Named NHI Leader In The Frost Radar™ Report For 2025
Learn moreFrost & Sullivan has recognized Veza as a leader in their latest report, Frost Radar™: Non-Human Identity Solutions, with standout scores in both Innovation and Growth. This independent validation highlights how Veza is redefining the way enterprises discover, govern, and secure machine and workload identities. As machine identities multiply far faster than human users, organizations […] -
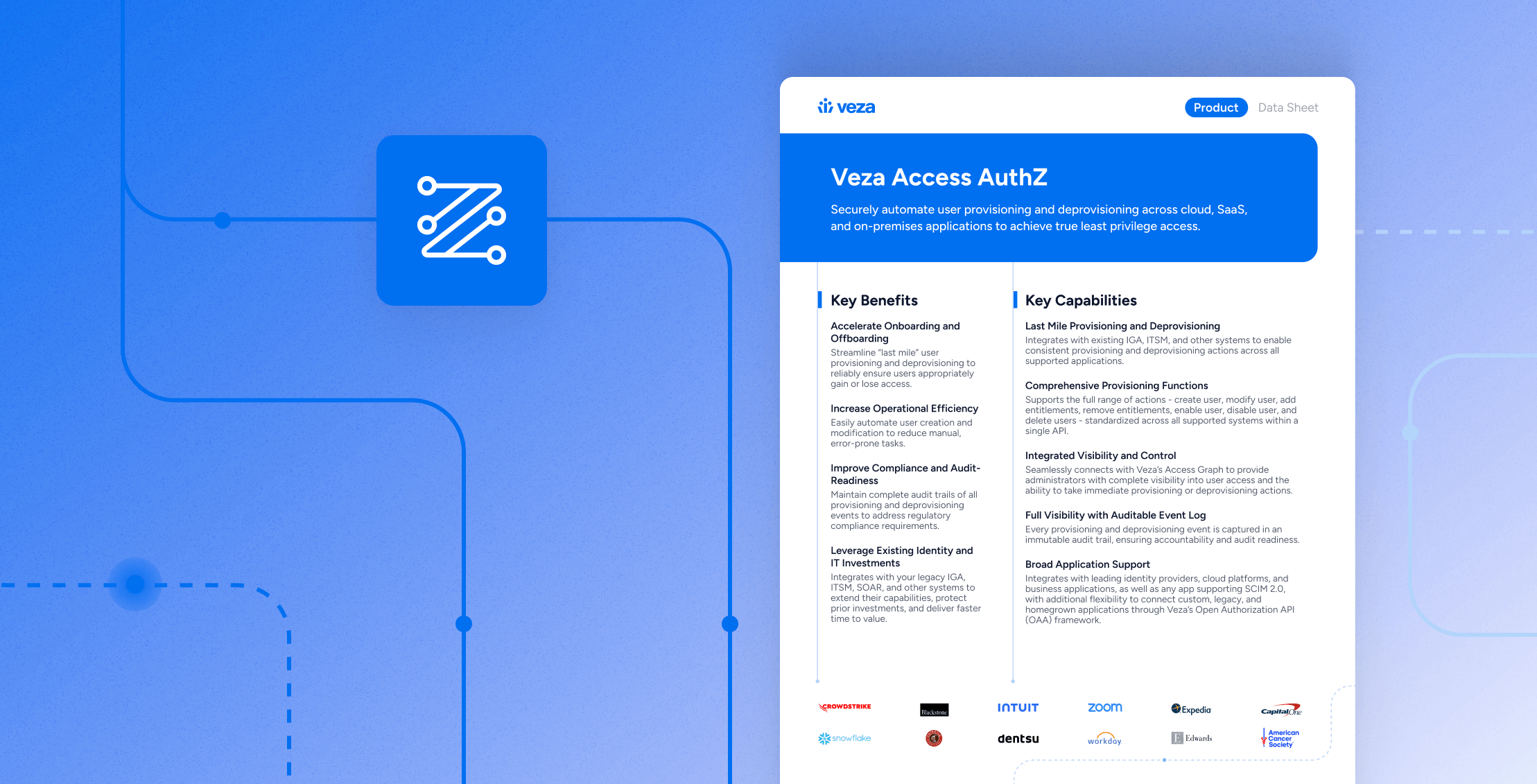 Data Sheet
Data SheetAccess AuthZ – Data Sheet
Learn more