-
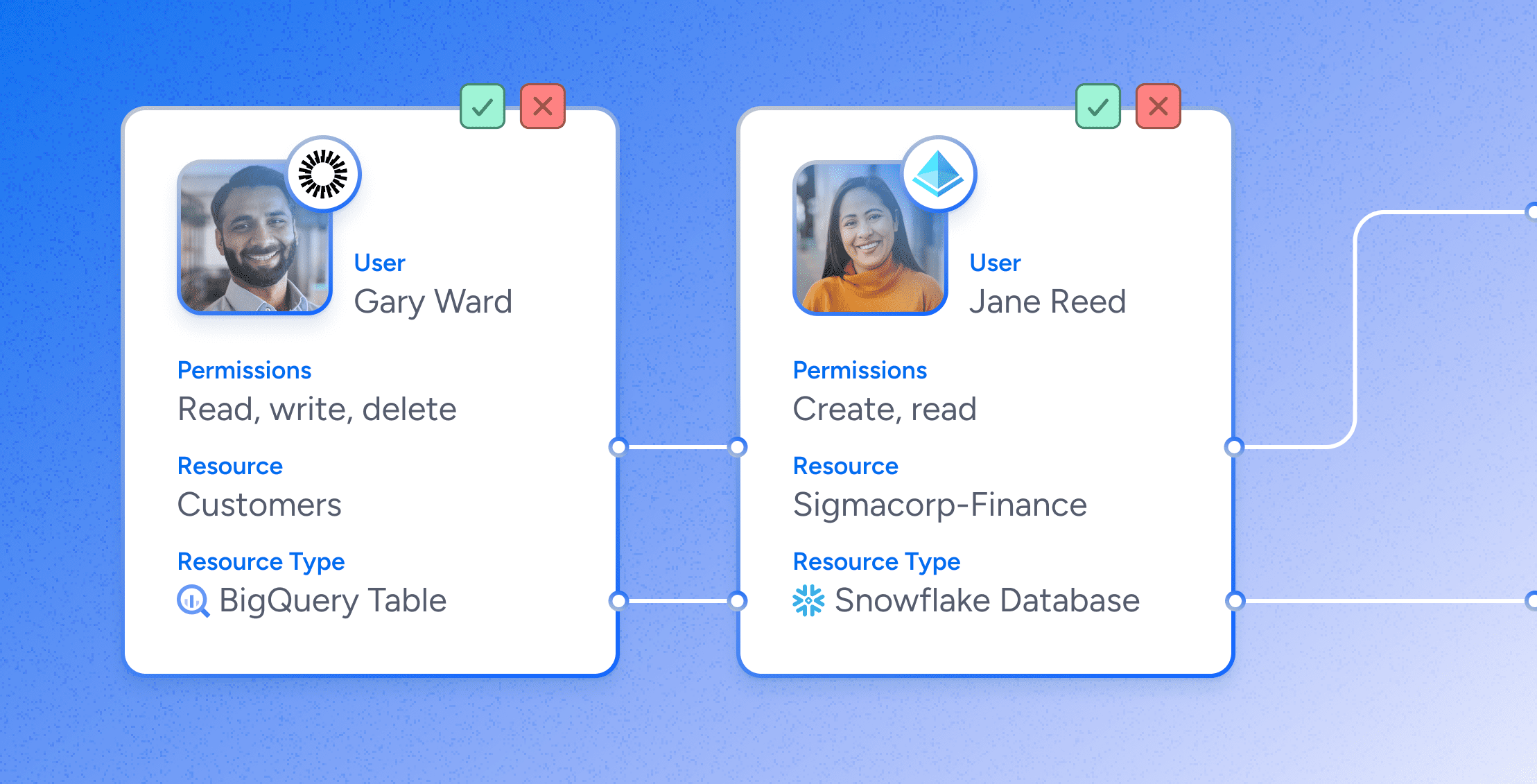 Technical Thought Leadership
Technical Thought LeadershipUser Access Reviews: How They Work & Best Practices
Learn more -
 Industry News
Industry NewsThe hard thing about Zero Trust
Learn more -
 Technical Thought Leadership
Technical Thought LeadershipRansomware supply chain threats: What made a global automotive company shut their plants this past spring?
Learn more -
Technical Thought Leadership
RBAC vs ABAC: Access Control Explained
Learn more -
Industry Events
Identity-Security Trends: Expectations vs Reality in Securing Data
Learn more -
Industry Events
Identiverse 2022 – where are we after a rapid move to cloud data?
Learn more -
Technical Thought Leadership
5 Keys To Securing Your Data in a Multi-Cloud Environment
Learn more -
Technical Thought Leadership
The Next Wave of Implementing Zero Trust: Moving from Authentication to Authorization
Learn more




