-
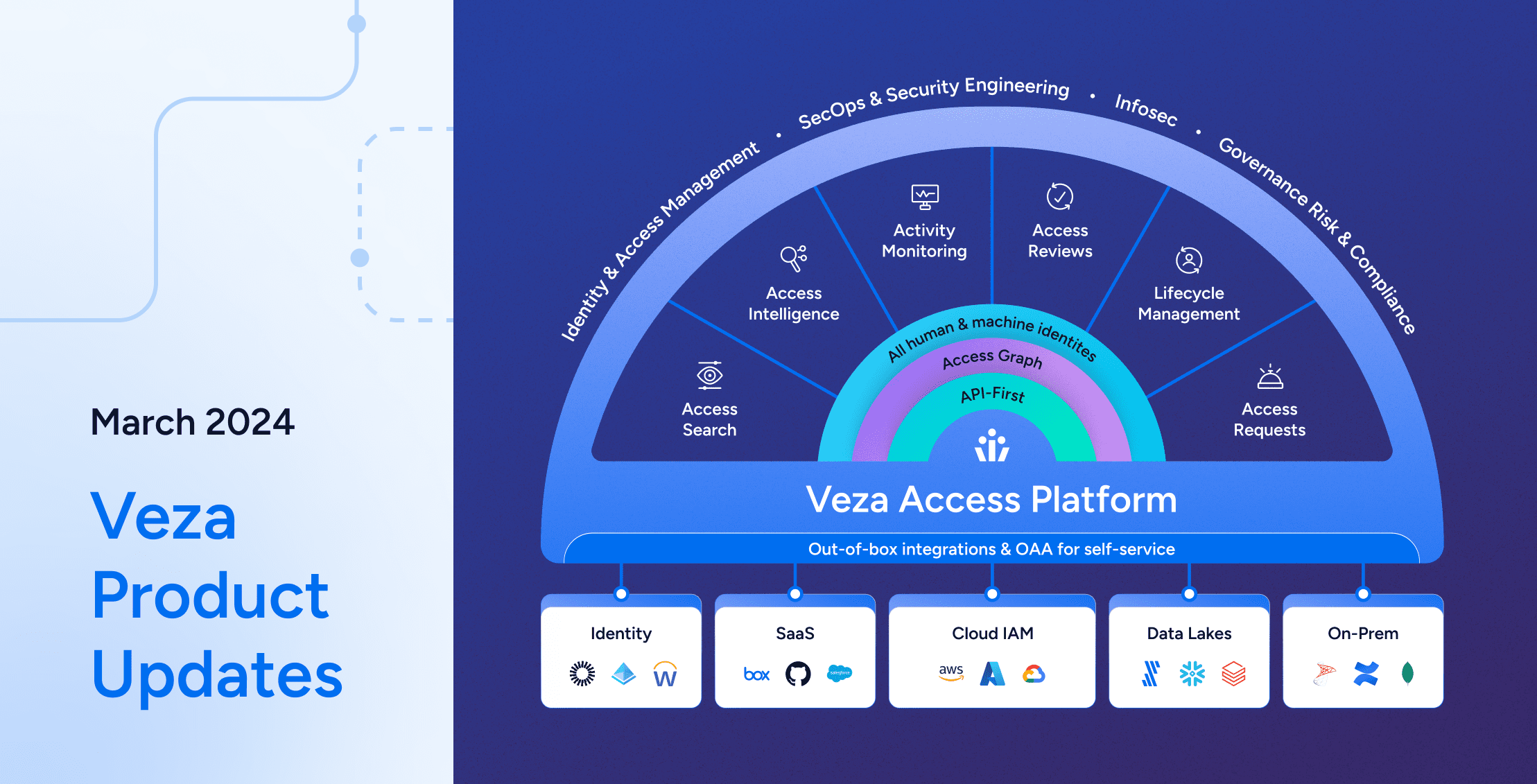 Product
ProductVeza Product Updates – March 2024
Learn more -
 Privileged Access
Privileged AccessWhat is non-human identity management
Learn more -
 Company
CompanyIdentity Security Posture Management
Learn more -
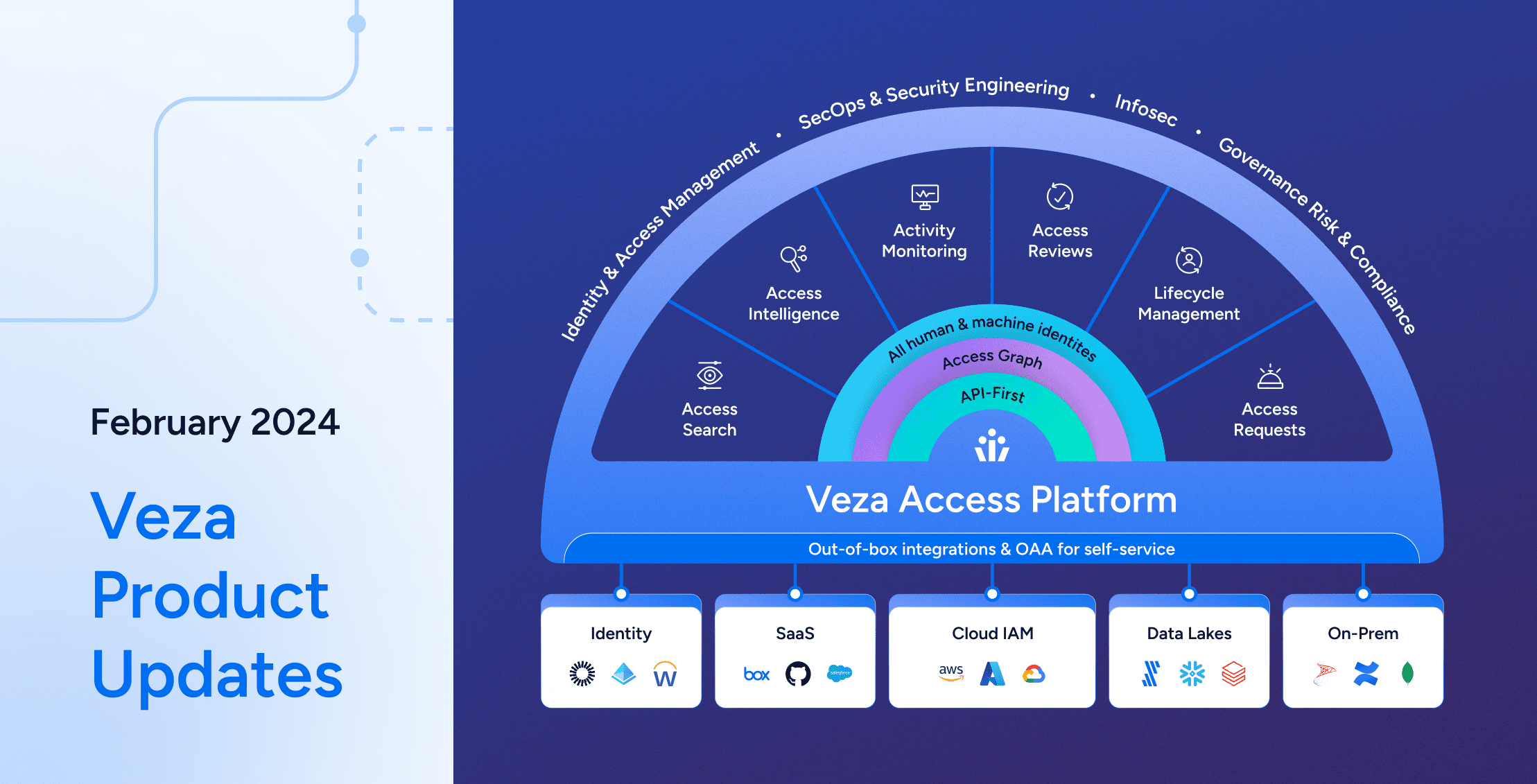 Product
ProductVeza Product Updates – February 2024
Learn more -
 Company
CompanyVeza @ Blackstone: Modernizing IGA with Automation and Intelligence
Learn more -
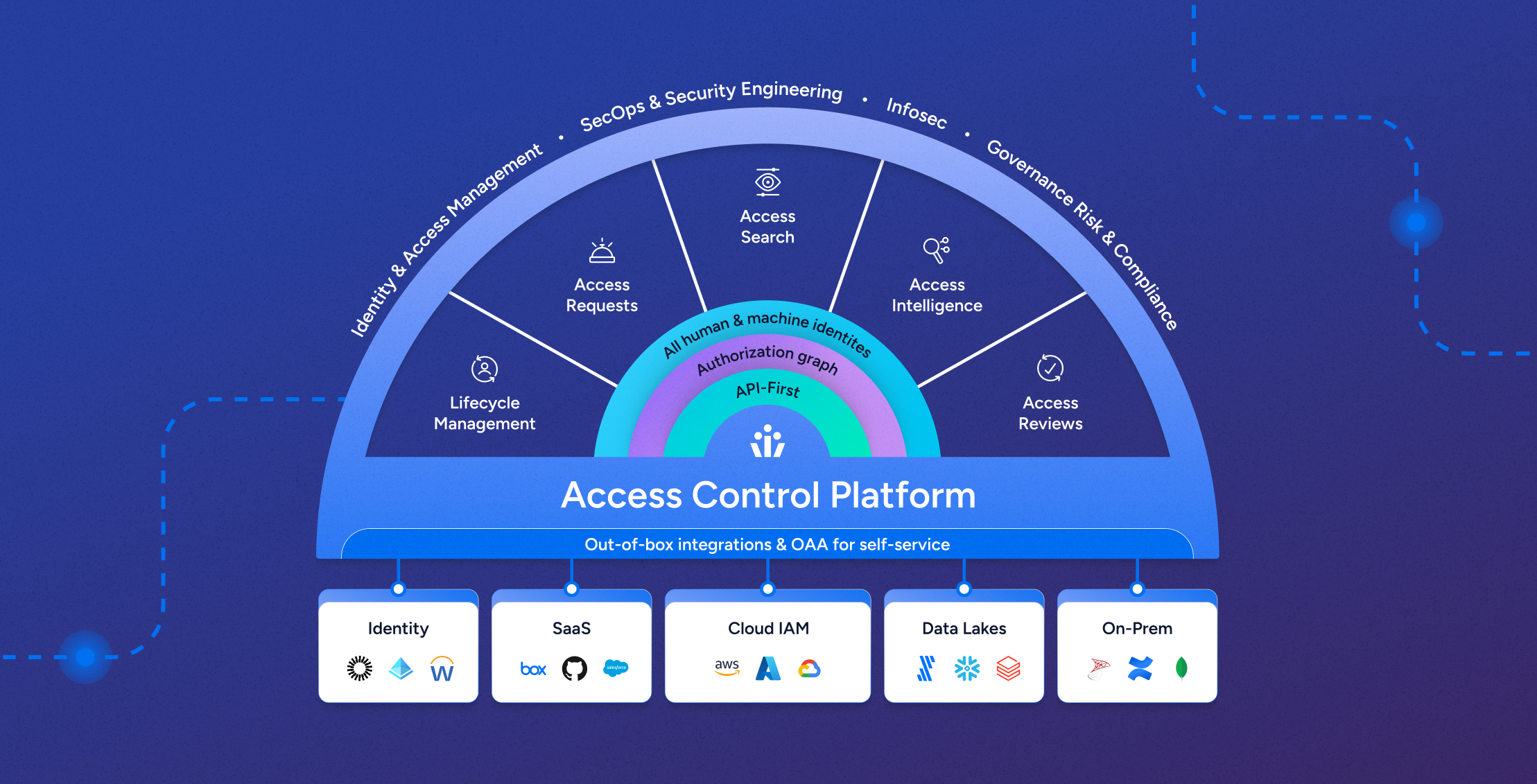 Product
ProductProduct updates: 2H Release Summary
Learn more -
 Product
ProductA field guide to bad permissions part 4: policy-violating permissions
Learn more -
 Product
ProductA field guide to bad permissions, part 3: excessive permissions
Learn more -
 Product
ProductWhat is identity security and why is it so complicated?
Learn more -
 Product
ProductA field guide to bad permissions part 2: expired permissions
Learn more




