De-risk the breach™
Veza, the Identity Security company, has cracked the code on cybersecurity’s
hardest question: “Who can take what action on what data?”































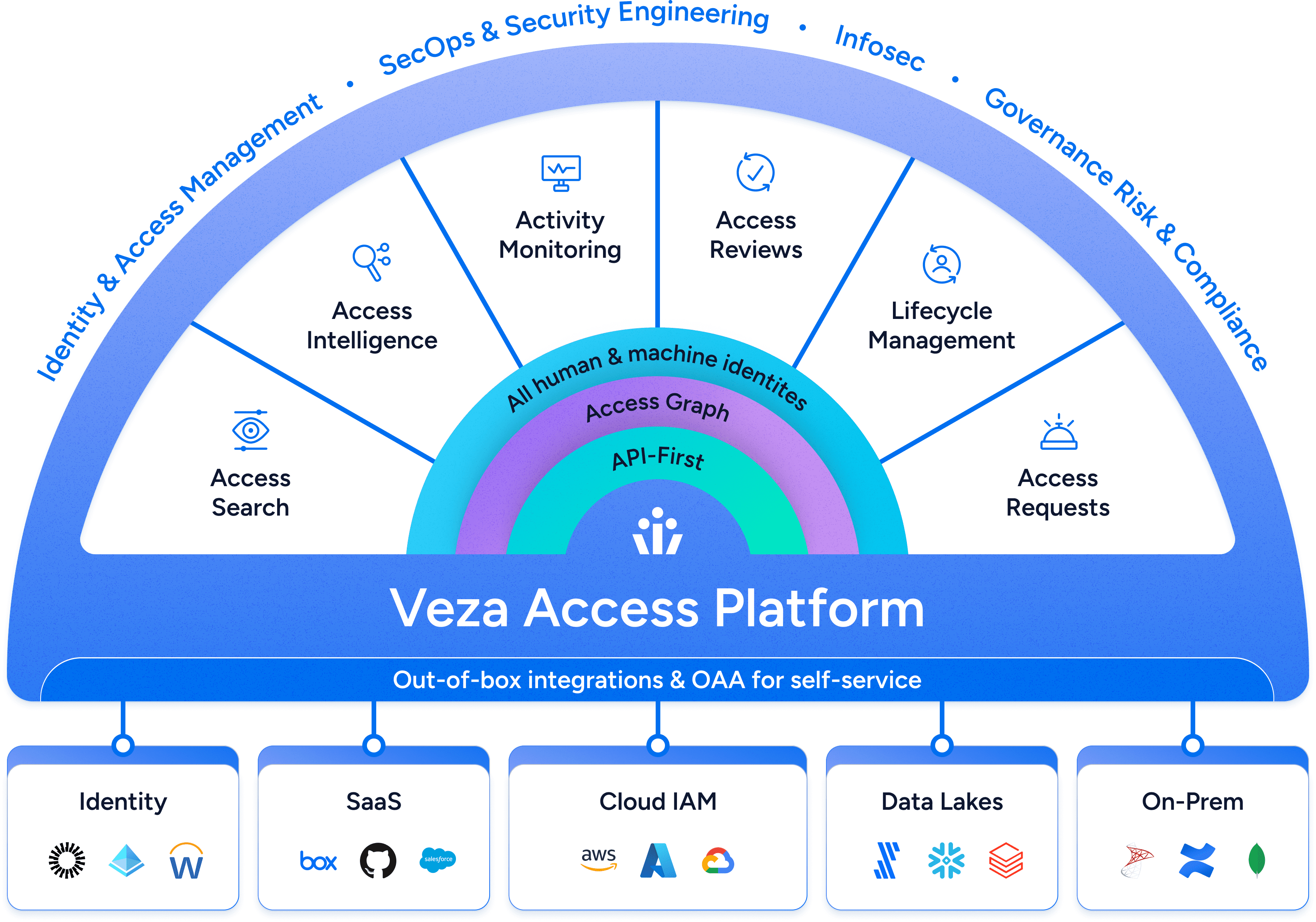
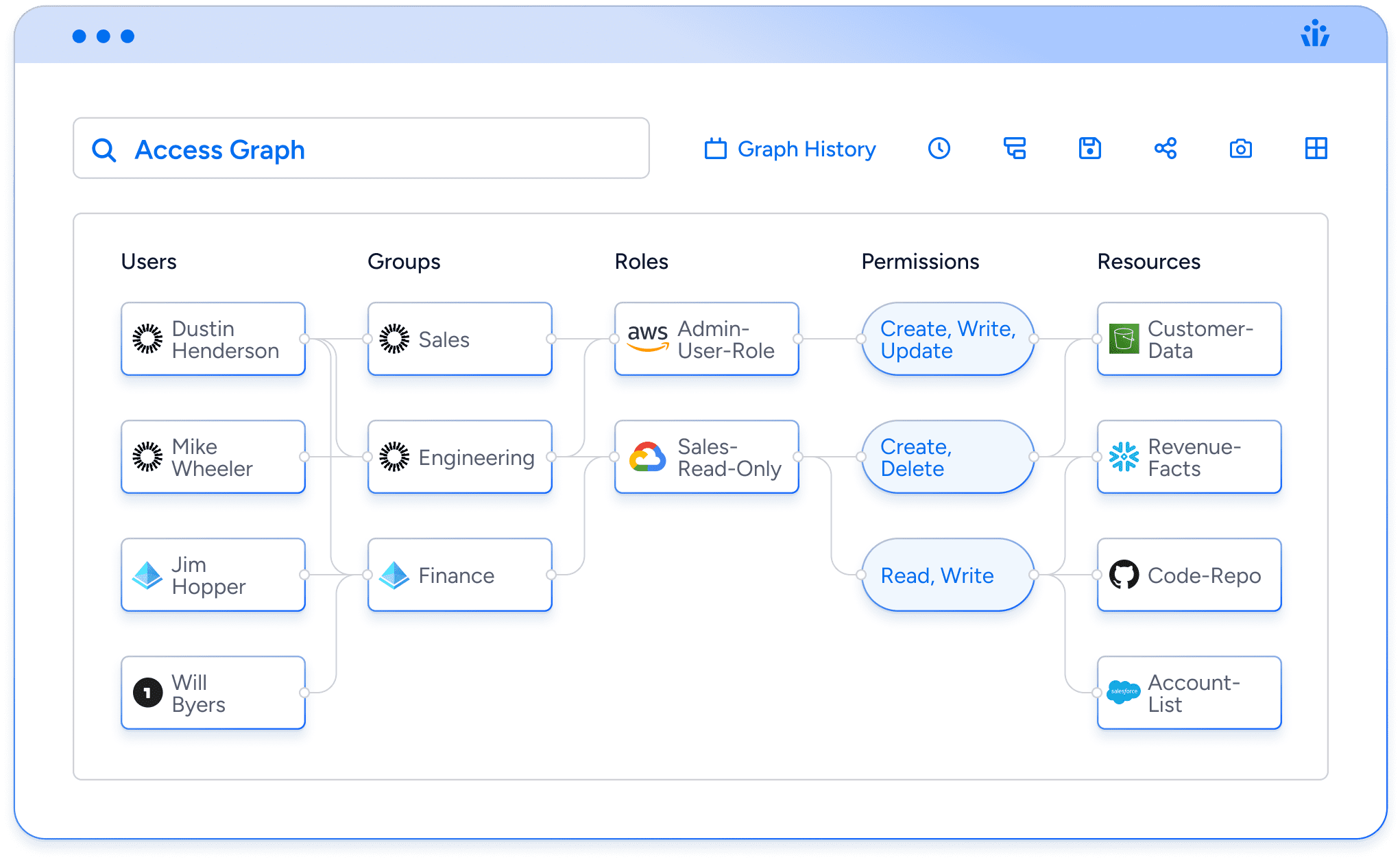
Veza Access Graph
Traditional identity systems have a fatal flaw. Nobody can see the reality of access. Veza captures access metadata from all enterprise systems and organizes it into our unique Access Graph, so you can answer, in real-time: who can take what action on what data?
Revolutionizing identity
governance at Blackstone
“We’re using Veza for access reviews and certifications with more than 700 reviewers. At this point, we’ve onboarded over 60 applications, including data, on-prem, and SaaS applications.”
Adam Fletcher | Chief Security Officer
A practitioners guide to Intelligent Access
Join cybersecurity leader Phil Venables, and Veza CEO and Co-Founder Tarun Thakur as they lay out the five principles of intelligent access and how to achieve them in your organization.
Safeguarding 100 years of entertainment with Deluxe Media
“Veza gives my team and I complete visibility and control of our data. That makes it very simple for our teams to determine any misconfiguration or inappropriate access. For example, we are able to identify everyone in GitHub that has access to specific code repositories, and understand AWS user access down to the bucket level.”
Sean Moore | Executive Vice President of Engineering
Top use cases
Leverage Veza’s Intelligent Access to power key business initiatives in your organization
Privileged Access Monitoring
Visualize and control data access across all systems, proactively mitigating risks for both human and machine identities.
Non-Human Identity Management
Untangle the complex web of cloud IAM to know the true permissions of all identities, including service accounts, and other machine identities.
Data System Access
Understand and control access to unstructured data, in your data lakes, ML datasets, shared drives, and cloud storage.
SaaS Access Security
Visualize and control data access across all systems, proactively mitigating risks for both human and machine identities.
Next-Gen IGA
Enforce least privilege & compliance with access reviews based on the effective permissions of identities. Identity Hygiene. Identity Analytics. Role/Group Analytics. User/Group Comparisons.
One platform for all identity‑based threats
Traditional identity systems have a fatal flaw. Nobody can see the reality of access. Veza ingests access metadata from all enterprise systems and organizes it in an Access Graph, optimized for real-time analytics, enabling you to answer who can take what action on our data
IGA
Identity Governance and Administration
Integrate quickly with all systems, cloud or on-prem, to remediate bad permissions and run comprehensive certifications.
PAM
Privileged Access Monitoring
Monitor and alert for new privileged accounts, including service accounts, that slip through the cracks of PAM and IGA.
IAM
Identity & Access Management
Overcome the blind spots of centralized IAM to see effective permissions at the data level and drive proactively toward least privilege.
ISPM
Identity Security Posture Management
Fight identity-based attacks by proactively managing access permissions and configurations across all identities.
CIEM
Cloud Infrastructure & Entitlements Management
Find and fix accidental over-permissioning and risky misconfigurations across all cloud providers.
SSPM
SaaS Security Posture Managmement
Go beyond SSO to monitor all your apps, see the reality of permissions, fix risky posture, and stay compliant.
ITDR
Identity Threat Detection & Response
Monitor and alert for sudden changes in access, and analyze potential blast-radius of compromised identities.